あなたを合格させる試験には100%確認済みEPM-DEF試験問題
EPM-DEF問題集PDFでEPM-DEFリアル試験問題解答
CyberArk EPM-DEF 認定を取得することで、サイバーセキュリティの専門家はエンドポイント特権管理の専門知識を誇示し、就職市場で差別化することができます。この認定は、世界的に認知されており、サイバーセキュリティの分野でのスキルと知識を証明するための優れた方法です。
質問 # 10
A Helpdesk technician needs to provide remote assistance to a user whose laptop cannot connect to the Internet to pull EPM policies. What CyberArk EPM feature should the Helpdesk technician use to allow the user elevation capabilities?
- A. Just In Time Access and Elevation
- B. Elevate Trusted Application If Necessary
- C. Loosely Connected Devices Credential Management
- D. Offline Policy Authorization Generator
正解:A
質問 # 11
An EPM Administrator needs to create a policy to allow the MacOS developers elevation to an application.
What type of policy should be used?
- A. Elevate Trusted Applications If Necessary Advanced Policy
- B. Elevate MacOS Policy
- C. Developer Applications Application Group
- D. Elevate Application Group
正解:A
質問 # 12
When enabling Threat Protection policies, what should an EPM Administrator consider? (Choose two.)
- A. Some Threat Protection policies are applicable only for Windows Servers as opposed to Workstations.
- B. Certain Threat Protection policies apply for specific applications not found on all machines
- C. Threat Protection policies requires an additional agent to be installed.
- D. Threat Protection features are not available in all regions.
正解:A、B
質問 # 13
When blocking applications, what is the recommended practice regarding the end-user UI?
- A. Show no prompts for blocked applications.
- B. Enable the Default Deny policy.
- C. Show a block prompt for blocked applications.
- D. Hide the CyberArk EPM Agent icon in the system tray.
正解:C
質問 # 14
What is a valid step to investigate an EPM agent that is unable to connect to the EPM server?
- A. Ping the endpoint from the EPM server.
- B. On the end point, open a browser session to the URL of the EPM server.
- C. Ping the server from the endpoint.
- D. Restart the end point
正解:C
質問 # 15
An EPM Administrator would like to include a particular file extension to be monitored and protected under Ransomware Protection. What setting should the EPM Administrator configure to add the extension?
- A. Anti-tampering Protection
- B. Authorized Applications (Ransomware Protection)
- C. Default Policies
- D. Files to be Ignored Always
正解:B
質問 # 16
An EPM Administrator would like to exclude an application from all Threat Protection modules. Where should the EPM Administrator make this change?
- A. Protect Against Ransomware under Default Policies.
- B. Privilege Threat Protection under Policies.
- C. Authorized Applications under Application Groups.
- D. Threat Protection under Agent Configurations.
正解:C
質問 # 17
After a clean installation of the EPM agent, the local administrator password is not being changed on macOS and the old password can still be used to log in.
What is a possible cause?
- A. Secure Token on macOS endpoint is not enabled.
- B. Endpoint password policy is too restrictive.
- C. After installation, Full Disk Access for the macOS agent to support EPM policies was not approved.
- D. EPM agent is not able to connect to the EPM server.
正解:A
質問 # 18
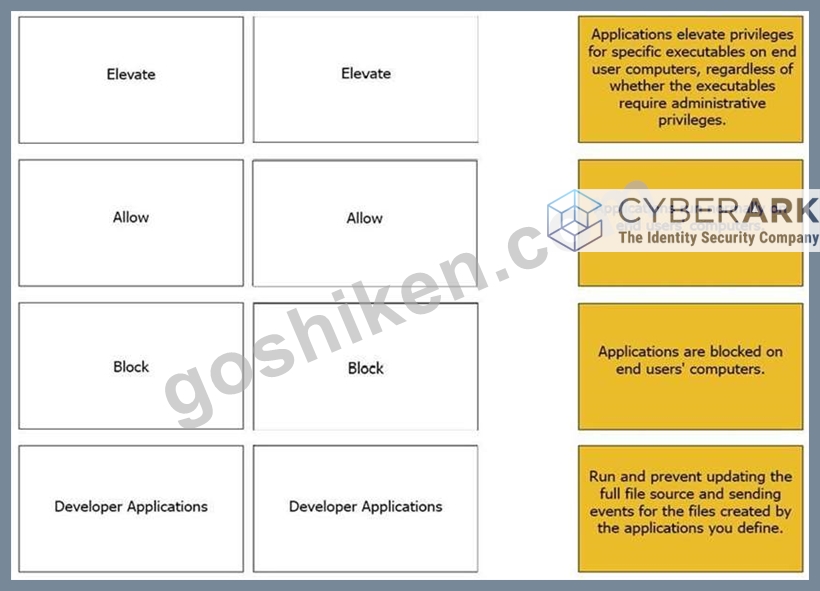
Match the Application Groups policy to their correct description.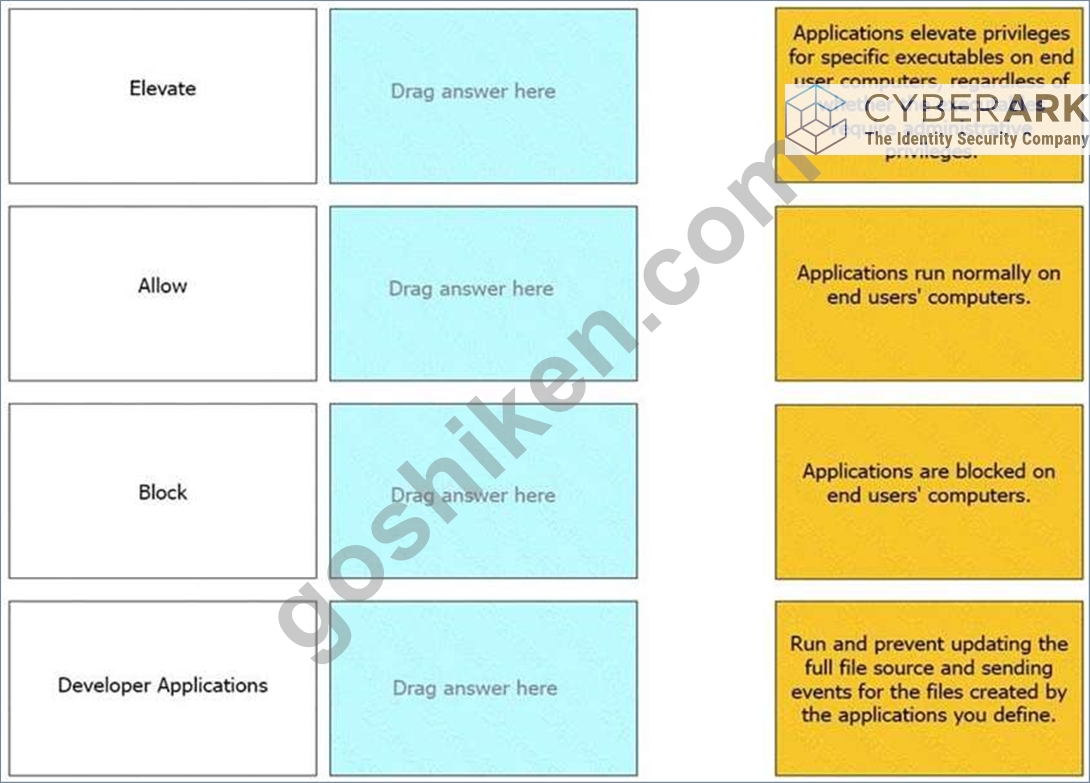
正解:
解説: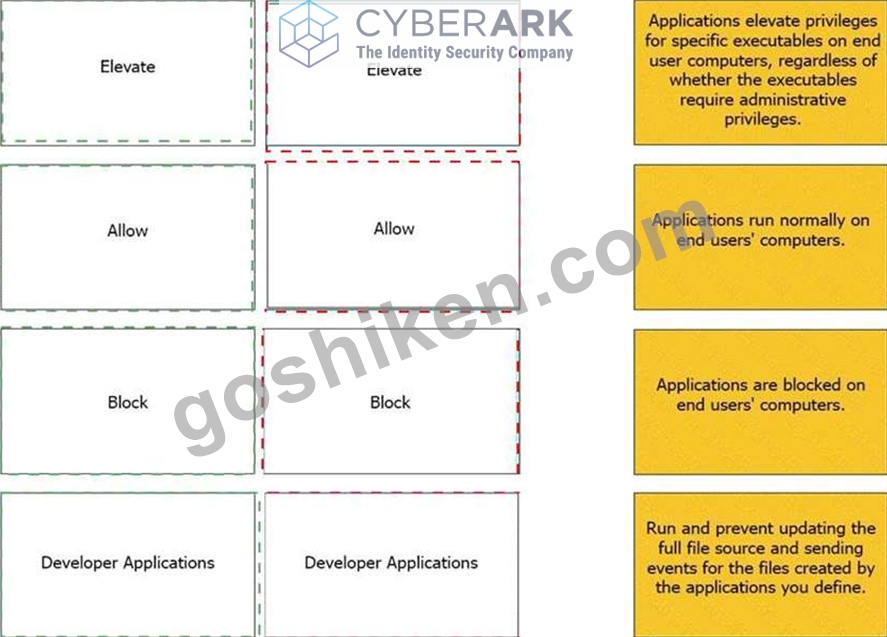
質問 # 19
What are valid policy options for JIT and elevation policies?
- A. Grant administrative access, Policy name, Log off to apply policy, Collect policy violation information
- B. Grant temporary access for all users, Policy name, Restart administrative processes in admin approval mode, Collect audit information
- C. Grant temporary access for, Policy name, Terminate administrative processes when the policy expires, Collect audit information
- D. Terminate administrative services, Grant policy access for, Policy name, Collect audit reports
正解:A
質問 # 20
An application has been identified by the LSASS Credentials Harvesting Module.
What is the recommended approach to excluding the application?
- A. Add the application to the Files to be Ignored Always in Agent Configurations.
- B. Add the application to an Advanced Policy or Application Group with an Elevate policy action.
- C. Exclude the application within the LSASS Credentials Harvesting module.
- D. In Agent Configurations, add the application to the Threat Protection Exclusions
正解:D
質問 # 21
Select the default threat intelligence source that requires additional licensing.
- A. VirusTotal
- B. Palo Alto WildFire
- C. CyberArk Application Risk Analysis Service
- D. NSRL
正解:B
質問 # 22
An EPM Administrator is looking to enable the Threat Deception feature, under what section should the EPM Administrator go to enable this feature?
- A. Policies
- B. Policy Audit
- C. Threat Intelligence
- D. Threat Protection Inbox
正解:A
質問 # 23
What type of user can be created from the Threat Deception LSASS Credential Lures feature?
- A. It does not create any users
- B. A standard user
- C. A domain admin user
- D. A local administrator user
正解:B
質問 # 24
Which setting in the agent configuration controls how often the agent sends events to the EPM Server?
- A. Heartbeat Timeout
- B. Policy Update Rate
- C. Condition Timeout
- D. Event Queue Flush Period
正解:D
質問 # 25
Which of the following is CyberArk's Recommended FIRST roll out strategy?
- A. Implement Threat Detection
- B. Implement Privilege Management
- C. Implement Ransomware Protection
- D. Implement Application Control
正解:B
質問 # 26
A policy needs to be created to block particular applications for a specific user group. Based on CyberArk's policy naming best practices, what should be included in the policy's name?
- A. Policy creation date
- B. Target use group
- C. The policy's Set name
- D. Creator of the policy
正解:B
質問 # 27
What are the policy targeting options available for a policy upon creation?
- A. EPM Sets, Computers in AD Security Groups, AD Users and AD Security Groups
- B. OS Computers, EPM Sets, AD Users
- C. Computers in this set, Computers in AD Security Groups, Users and Groups
- D. AD Users and Groups, Computers in AD Security Groups, Servers
正解:A
質問 # 28
In EPM, creation of which user type is required to use SAML?
- A. Local CyberArk EPM User
- B. AD User
- C. SQL User
- D. Azure AD User
正解:D
質問 # 29
For the CyberArk EPM Threat Deception Credential Lure feature, what is the recommendation regarding the username creation?
- A. The username should match the built-in local Administrator.
- B. The username should match to an existing account.
- C. The username should not match to an existing account.
- D. The username should have a strong password associated.
正解:C
質問 # 30
What EPM component is responsible for communicating password changes in credential rotation?
- A. EPM Agent
- B. EPM Discovery
- C. EPM Server
- D. EPM API
正解:C
質問 # 31
......
EPM-DEF問題集100合保証には最新のサンプル:https://www.goshiken.com/CyberArk/EPM-DEF-mondaishu.html
