[2022年02月07日] 究極のAZ-500準備ガイド!無料最新のMicrosoft練習テスト問題集
今すぐゲットせよ!高評価Microsoft AZ-500試験問題集
質問 30
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Azure Username: [email protected]
Azure Password: Ag1Bh9!#Bd
The following information is for technical support purposes only:
Lab Instance: 10598168



You need to prevent administrative users from accidentally deleting a virtual network named VNET1. The administrative users must be allowed to modify the settings of VNET1.
To complete this task, sign in to the Azure portal.
正解:
解説:
See the explanation below.
Explanation
Locking prevents other users in your organization from accidentally deleting or modifying critical resources, such as Azure subscription, resource group, or resource.
Note: In Azure, the term resource refers to an entity managed by Azure. For example, virtual machines, virtual networks, and storage accounts are all referred to as Azure resources.
1. In the Settings blade for virtual network VNET, select Locks.
2. To add a lock, select Add.
3. For Lock type select Delete lock, and click OK
Reference:
https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-lock-resources
質問 31
You have an Azure subscription that contains virtual machines.
You enable just in time (JIT) VM access to all the virtual machines.
You need to connect to a virtual machine by using Remote Desktop.
What should you do first?
- A. From the Azure portal, select the virtual machine and add the Network Watcher Agent virtual machine
- B. From Azure Directory (Azure AD) Privileged Identity Management (PIM), activate the Security administrator user role.
- C. From the Azure portal, select the virtual machine, select Connect, and then select Request access.
- D. From Azure Active Directory (Azure AD) Privileged Identity Management (PIM), activate the Owner role for the virtual machine.
正解: C
解説:
extension.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-machines/windows/connect-logon
質問 32
You have an Azure subscription that contains 100 virtual machines. Azure Diagnostics is enabled on all the virtual machines.
You are planning the monitoring of Azure services in the subscription.
You need to retrieve the following details:
* Identify the user who deleted a virtual machine three weeks ago.
* Query the security events of a virtual machine that runs Windows Server 2016.
What should you use in Azure Monitor? To answer, drag the appropriate configuration settings to the correct details. Each configuration setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
正解:
解説:
Explanation
Box1: Activity log
Azure activity logs provide insight into the operations that were performed on resources in your subscription.
Activity logs were previously known as "audit logs" or "operational logs," because they report control-plane events for your subscriptions.
Activity logs help you determine the "what, who, and when" for write operations (that is, PUT, POST, or DELETE).
Box 2: Logs
Log Integration collects Azure diagnostics from your Windows virtual machines, Azure activity logs, Azure Security Center alerts, and Azure resource provider logs. This integration provides a unified dashboard for all your assets, whether they're on-premises or in the cloud, so that you can aggregate, correlate, analyze, and alert for security events.
References:
https://docs.microsoft.com/en-us/azure/security/azure-log-audit
質問 33
You have an Azure Container Registry named Registry1.
You add role assignment for Registry1 as shown in the following table.
Which users can upload images to Registry1 and download images from Registry1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
正解:
解説:
References:
https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-roles
質問 34
You have an Azure subscription named Subscription1 that contains the resources shown in the following table.
You create an Azure role by using the following JSON file.
You assign Role1 to User1 for RG1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
正解:
解説:
Reference:
https://docs.microsoft.com/en-us/azure/role-based-access-control/built-in-roles#compute
質問 35
You have an Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com.
The User administrator role is assigned to a user named Admin1.
An external partner has a Microsoft account that uses the [email protected] sign in.
Admin1 attempts to invite the external partner to sign in to the Azure AD tenant and receives the following error message: "Unable to invite user [email protected] Generic authorization exception." You need to ensure that Admin1 can invite the external partner to sign in to the Azure AD tenant.
What should you do?
- A. From the Roles and administrators blade, assign the Security administrator role to Admin1.
- B. From the Organizational relationships blade, add an identity provider.
- C. From the Custom domain names blade, add a custom domain.
- D. From the Users blade, modify the External collaboration settings.
正解: D
解説:
You need to allow guest invitations in the External collaboration settings.
質問 36
Your company has two offices in Seattle and New York. Each office connects to the Internet by using a NAT device. The offices use the IP addresses shown in the following table.
The company has an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains the users shown in the following table.
The MFA service settings are configured as shown in the exhibit. (Click the Exhibit tab.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
正解:
解説:
Explanation
Box 2: No
Use of Microsoft Authenticator is not required.
Note: Microsoft Authenticator is a multifactor app for mobile devices that generates time-based codes used during the Two-Step Verification process.
Box 3: No
The New York IP address subnet is included in the "skip multi-factor authentication for request.
References:
https://www.cayosoft.com/difference-enabling-enforcing-mfa/
質問 37
You are evaluating the security of VM1, VM2, and VM3 in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
正解:
解説:
Explanation
質問 38
You have an Azure subscription named Sub1.
You have an Azure Active Directory (Azure AD) group named Group1 that contains all the members of your IT team.
You need to ensure that the members of Group1 can stop, start, and restart the Azure virtual machines in Sub1. The solution must use the principle of least privilege.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
正解:
解説:
References:
https://www.petri.com/cloud-security-create-custom-rbac-role-microsoft-azure
質問 39
You need to configure WebApp1 to meet the data and application requirements.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. Turn on the Incoming client certificates protocol setting.
- B. Turn on the HTTPS Only protocol setting.
- C. Set the Minimum TLS Version protocol setting to 1.2.
- D. Change the pricing tier of the App Service plan.
- E. Upload a public certificate.
正解: A,B
解説:
https://docs.microsoft.com/en-us/azure/app-service/app-service-web-configure-tls-mutual-auth
Topic 1, Litware, inc
Existing Environment
Litware has an Azure subscription named Sub1 that has a subscription ID of 43894a43-17c2-4a39-8cfc-3540c2653ef4.
Sub1 is associated to an Azure Active Directory (Azure AD) tenant named litwareinc.com. The tenant contains the user objects and the device objects of all the Litware employees and their devices. Each user is assigned an Azure AD Premium P2 license. Azure AD Privileged Identity Management (PIM) is activated.
The tenant contains the groups shown in the following table.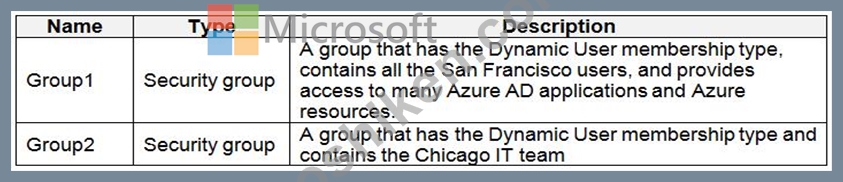
The Azure subscription contains the objects shown in the following table.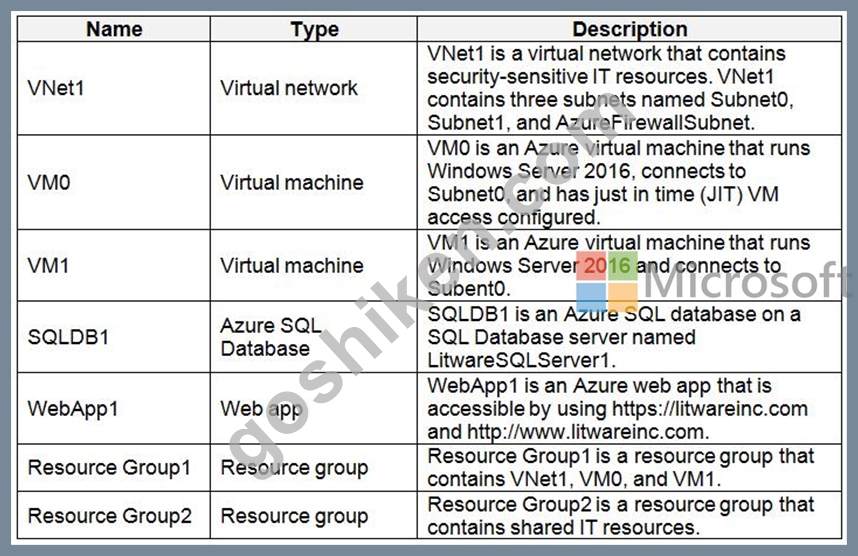
Azure Security Center is set to the Free tier.
Planned changes
Litware plans to deploy the Azure resources shown in the following table.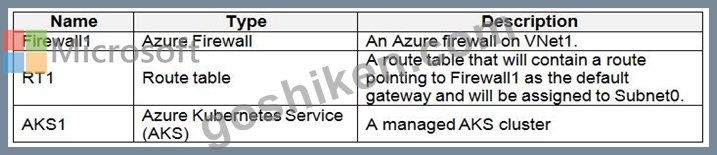
Litware identifies the following identity and access requirements:
All San Francisco users and their devices must be members of Group1.
The members of Group2 must be assigned the Contributor role to Resource Group2 by using a permanent eligible assignment.
Users must be prevented from registering applications in Azure AD and from consenting to applications that access company information on the users' behalf.
Platform Protection Requirements
Litware identifies the following platform protection requirements:
Microsoft Antimalware must be installed on the virtual machines in Resource Group1.
The members of Group2 must be assigned the Azure Kubernetes Service Cluster Admin Role.
Azure AD users must be to authenticate to AKS1 by using their Azure AD credentials.
Following the implementation of the planned changes, the IT team must be able to connect to VM0 by using JIT VM access.
A new custom RBAC role named Role1 must be used to delegate the administration of the managed disks in Resource Group1. Role1 must be available only for Resource Group1.
Security Operations Requirements
Litware must be able to customize the operating system security configurations in Azure Security Center.
質問 40
A user named Debbie has the Azure app installed on her mobile device.
You need to ensure that [email protected] is alerted when a resource lock is deleted.
To complete this task, sign in to the Azure portal.
You need to configure an alert rule in Azure Monitor.
Type Monitor into the search box and select Monitor from the search results.
Click on Alerts.
Click on +New Alert Rule.
In the Scope section, click on the Select resource link.
In the Filter by resource type box, type locks and select Management locks (locks) from the filtered results.
Select the subscription then click the Done button.
In the Condition section, click on the Select condition link.
Select the Delete management locks condition the click the Done button.
In the Action group section, click on the Select action group link.
Click the Create action group button to create a new action group.
Give the group a name such as Debbie Mobile App (it doesn't matter what name you enter for the exam) then click the Next: Notifications > button.
In the Notification type box, select the Email/SMS message/Push/Voice option.
In the Email/SMS message/Push/Voice window, tick the Azure app Push Notifications checkbox and enter [email protected] in the Azure account email field.
Click the OK button to close the window.
- A. Click the Review & Create button then click the Create button to create the action group.
- B. Back in the Create alert rule window, in the Alert rule details section, enter a name such as Management lock deletion in the Alert rule name field.
- C. Enter a name such as Debbie Mobile App in the notification name box.
- D. Click the Create alert rule button to create the alert rule.
正解: A
質問 41
You have an Azure subscription that contains a virtual machine named VM1.
You create an Azure key vault that has the following configurations:
* Name: Vault5
* Region: West US
* Resource group: RG1
You need to use Vault5 to enable Azure Disk Encryption on VM1. The solution must support backing up VM1 by using Azure Backup.
Which key vault settings should you configure?
- A. Secrets
- B. Access policies
- C. Locks
- D. Keys
正解: B
解説:
References:
https://docs.microsoft.com/en-us/azure/key-vault/key-vault-secure-your-key-vault
質問 42
You have an Azure subscription that contains the virtual networks shown in the following table.
The subscription contains the virtual machines shown in the following table.
On NIC1, you configure an application security group named ASG1.
On which other network interfaces can you configure ASG1?
- A. NIC2, NIC3, and NIC4 only
- B. NIC2, NIC3, NIC4, and NIC5
- C. NIC2 and NIC3 only
- D. NIC2 only
正解: C
解説:
Only network interfaces in NVET1, which consists of Subnet11 and Subnet12, can be configured in ASG1, as all network interfaces assigned to an application security group have to exist in the same virtual network that the first network interface assigned to the application security group is in.
Reference:
https://azure.microsoft.com/es-es/blog/applicationsecuritygroups/
質問 43
You need to create Role1 to meet the platform protection requirements.
How should you complete the role definition of Role1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
正解:
解説:
Explanation
1) Microsoft.Compute/
2) disks
3) /subscrption/{subscriptionId}/resourceGroups/{Resource Group Id}
A new custom RBAC role named Role1 must be used to delegate the administration of the managed disks in Resource Group1. Role1 must be available only for Resource Group1.
質問 44
You have a web app named WebApp1.
You create a web application firewall (WAF) policy named WAF1.
You need to protect WebApp1 by using WAF1.
What should you do first?
- A. Deploy an Azure Front Door.
- B. Deploy Azure Firewall.
- C. Add an extension to WebApp1.
正解: A
解説:
References:
https://docs.microsoft.com/en-us/azure/frontdoor/quickstart-create-front-door
質問 45
You are troubleshooting a security issue for an Azure Storage account You enable Azure Storage Analytics logs and archive It to a storage account. What should you use to retrieve the diagnostics logs?
- A. Azure Cosmos DB explorer
- B. SQL query editor in Azure
- C. Azure Storage Explorer
- D. Azure Monitor
正解: C
質問 46
You need to deploy Microsoft Antimalware to meet the platform protection requirements.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
正解:
解説:
Explanation:
Scenario: Microsoft Antimalware must be installed on the virtual machines in RG1.
RG1 is a resource group that contains Vnet1, VM0, and VM1.
Box 1: DeployIfNotExists
DeployIfNotExists executes a template deployment when the condition is met.
Azure policy definition Antimalware
Incorrect Answers:
Append:
Append is used to add additional fields to the requested resource during creation or update. A common example is adding tags on resources such as costCenter or specifying allowed IPs for a storage resource.
Deny:
Deny is used to prevent a resource request that doesn't match defined standards through a policy definition and fails the request.
Box 2: The Create a Managed Identity setting
When Azure Policy runs the template in the deployIfNotExists policy definition, it does so using a managed identity. Azure Policy creates a managed identity for each assignment, but must have details about what roles to grant the managed identity.
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects
質問 47
You create an alert rule that has the following settings:
Resource: RG1
Condition: All Administrative operations
Actions: Action groups configured for this alert rule: ActionGroup1
Alert rule name: Alert1
You create an action rule that has the following settings:
Scope: VM1
Filter criteria: Resource Type = "Virtual Machines"
Define on this scope: Suppression
Suppression config: From now (always)
Name: ActionRule1
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Note: Each correct selection is worth one point.
正解:
解説:
References:
https://docs.microsoft.com/en-us/azure/azure-monitor/platform/alerts-activity-log
https://docs.microsoft.com/en-us/azure/azure-monitor/platform/alerts-action-rules
質問 48
You have two Azure virtual machines in the East US2 region as shown in the following table.
You deploy and configure an Azure Key vault.
You need to ensure that you can enable Azure Disk Encryption on VM1 and VM2.
What should you modify on each virtual machine? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
正解:
解説:
Explanation
VM1: The Tier
The Tier needs to be upgraded to standard.
Disk Encryption for Windows and Linux IaaS VMs is in General Availability in all Azure public regions and Azure Government regions for Standard VMs and VMs with Azure Premium Storage.
VM2: the operating system
References:
https://docs.microsoft.com/en-us/azure/virtual-machines/windows/generation-2#generation-1-vs-generation-2-ca
質問 49
You have a network security group (NSG) bound to an Azure subnet.
You run Get-AzureRmNetworkSecurityRuleConfig and receive the output shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
正解:
解説:
Explanation
Box 1: able to connect to East US 2
The StorageEA2Allow has DestinationAddressPrefix {Storage/EastUS2}
Box 2: dropped
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/manage-network-security-group
質問 50
On Monday, you configure an email notification in Azure Security Center to email notifications to [email protected].
On Tuesday, Security Center generates the security alerts shown in the following table.
How many email notifications will [email protected] receive on Tuesday? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
正解:
解説:
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-provide-security-contact-details
質問 51
......
Microsoft AZ-500 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
| トピック 7 |
|
| トピック 8 |
|
合格率取得する秘訣はAZ-500認定試験エンジンPDF:https://www.goshiken.com/Microsoft/AZ-500-mondaishu.html
AZ-500試験問題集で合格できるには更新されたテスト問題集:https://drive.google.com/open?id=10eV7n2mgHEZmKglcfK2Tx_Ze7kqOvQmh
