[2024年01月01日] 365日無料更新S1000-007知能問題集をゲット
ベスト品質のIBM S1000-007試験問題
質問 # 15
An administrator has configured NFS export in the /etc/exports file. Based on the following output, with which permissions has the /tmp directory been exported?
- A. no permissions
- B. read-write permissions
- C. read-only permissions
- D. write-only permissions
正解:C
質問 # 16
A customer calls to complain about slow workload performance but offers no additional details. What should the administrator do next?
- A. Increase CPU entitlement by 10%
- B. Add two more virtual CPUs by DLPAR operation.
- C. Ask the caller for additional details.
- D. Add 10% more memory by DLPAR operation
正解:D
質問 # 17
An administrator finds that their development server has crashed and an error code 554 is displayed. They know that this error is typically associated with a problem executing varyon rootvg and they should boot from AIX Media to be able to perform maintenance tasks. When the administrator checks the crontab of the NIM server, they find that a mksysb image is created each night.
Can the administrator use this mlcsysb to boot the server and perform the required maintenance tasks?
- A. No, because mksysb is not bootable.
- B. Yes, but they may need to create a machine resource first.
- C. No, because they need to use the original AIX installation media for that server.
- D. Yes, but they may need to create a spot first.
正解:B
解説:
A mksysb image is a snapshot of the AIX operating system and its configuration, so it can be used to boot the server and perform the required maintenance tasks. However, in order to use the mksysb image, the administrator may need to create a machine resource in the NIM environment first. According to the IBM AIX v7 Administrator Specialty Study Guide (page 13-6), the mksysb image should be used in combination with a previously created machine resource, which defines the parameters for the installation.
質問 # 18
An administrator has configured NFS export in the /etc/exports file. Based on the following output, with which permissions has the /tmp directory been exported?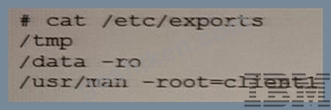
- A. no permissions
- B. read-write permissions
- C. read-only permissions
- D. write-only permissions
正解:B
質問 # 19
A system administrator includes the values RES TIMEOUT=1 and RES_RETRY=1 in the /etc/environment file. What is the effect of this change?
- A. It reduces the failover time to the secondary name server when the first name server is not reachable.
- B. It avoids NFS mounts appearing to be hung or stalled indefinitely when there are network outages.
- C. It causes ssh connections to disconnect after 1 minute of no activity.
- D. It reduces the failover time to the secondary NTP Server when the first NTP Server is unavailable.
正解:B
質問 # 20
An administrator finds that their development server has crashed and an error code 554 is displayed. They know that this error is typically associated with a problem executing varyon rootvg and they should boot from AIX Media to be able to perform maintenance tasks. When the administrator checks the crontab of the NIM server, they find that a mksysb image is created each night.
Can the administrator use this mlcsysb to boot the server and perform the required maintenance tasks?
- A. No, because they need to use the original AIX installation media for that server.
- B. No, because mksysb is not bootable.
- C. Yes, but they may need to create a spot first.
- D. Yes, but they may need to create a machine resource first.
正解:B
質問 # 21
The administrator of an AIX NIM client system has accidentally removed the /etc/niminfo file. Which method is used to rebuild the /etc/niminfo file?
- A. Use the nimclient command to restore the /etc/niminfo file from the most recent mksysb backup image.
- B. Use the niminit command on the AIX client system to rebuild the /etc/niminfo file.
- C. Use the nimclient command on the AIX client system to rebuild the /etc/niminfo file.
- D. Use the rep command on the AIX client system to copy the /etc/niminfo file from the NIM master.
正解:B
解説:
The niminit command can be used to rebuild the /etc/niminfo file on an AIX NIM client system if it has been accidentally deleted. This command will read the NIM database on the NIM master and generate the /etc/niminfo file accordingly. Reference: IBM AIX v7 Administrator Specialty Study Guide.
質問 # 22
Which statement is true regarding the snap command?
- A. The data must be stored in /tmp.
- B. All options are enabled by default.
- C. It collects performance related data.
- D. By default, it will check there is enough space where the data is to be stored.
正解:C
質問 # 23
While trying to extend a file system named /work an administrator receives the following error. 0516-787 extendlv: Maximum allocation for logical volume fslv00 is 256.
What must be done to allow the file system to be extended?
- A. Change the logical volume type to jfs2 as JFS logical volumes cannot extend past 256.
- B. Increase the volume group's maximum limit of logical partitions per logical volume.
- C. Increase the setting for maximum number of logical partitions for that logical volume.
- D. Change the file system's maximum capacity.
正解:C
解説:
This error indicates that the maximum number of logical partitions for the logical volume is set to 256 and needs to be increased in order to allow the file system to be extended. From the IBM AIX v7 Administrator Specialty Study Guide: "The 0516-787 error indicates that the maximum number of logical partitions for the logical volume is set to 256, and needs to be increased in order to allow the file system to be extended."
質問 # 24
An administrator checks the IBM Fix Level Recommendation Tool (FLRT) for their system to see if they need to update IBM firmware or software.
The tool asks for their current system firmware level. How can the administrator confirm what it is?
- A. run lsattr -El sys0 Igrep mcode
- B. run lsattr -1 firmware0
- C. run lsmcode -A
- D. run lscfg -vl sys0
正解:C
解説:
According to the IBM AIX v7 Administrator Specialty Study Guide, the lsmcode command is used to list the microcode of the system. The -A flag is used to list the microcode level and the active microcode level of the system. This command can be used to confirm the system firmware level which is required to use the IBM Fix Level Recommendation Tool (FLRT).
質問 # 25
An administrator is tasked with installing an open source package. They are told to use the IBM AIX Toolbox for Linux Applications because the organization wants to be able to open tickets with IBM support.
What should the administrator tell the requester?
- A. IBM offers extended support for open source software that is licensed with the hardware.
- B. IBM offers extended support for open source software and they need to verify entitlement.
- C. IBM offers this open source software as-is.
- D. IBM offers standard support for open source software that is licensed with the operating system.
正解:B
質問 # 26
How are console log messages recorded by AIX?
- A. syslog
- B. errdemon
- C. rsyslog
- D. alog
正解:C
質問 # 27
What command is used to monitor SAN I/O performance/throughput?
- A. mpstat -w 1
- B. ioo -L
- C. iostat -DIRT 60 10
- D. vmstat -i 1
正解:C
解説:
The command used to monitor SAN I/O performance/throughput is iostat -DIRT 60 10. The iostat command is used to monitor I/O performance and throughput on a SAN device. The DIRT (Disk I/O Response Time) flag can be used to display the response time for each I/O request. The last two arguments, 60 and 10, are the interval (in seconds) and the number of iterations respectively. This command will monitor I/O performance/throughput every 60 seconds for 10 iterations.
質問 # 28
When attempting to recover a corrupted file system an administrator runs the command fsck against the unmounted file system and receives the following error: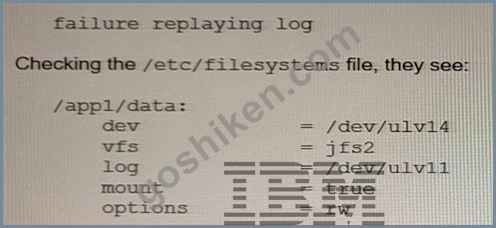
After confirming that the file system is not mounted, what should the administrator do next?
- A. Convert the log to INLINE.
- B. Run logform /dev/u1v11.
- C. Run fsck: with the -F (force) flag.
- D. Run logrcvr /dev/ulv14 .
正解:C
解説:
When attempting to recover a corrupted file system, the administrator should first confirm that the file system is not mounted. If the file system is not mounted, then the administrator should run the fsck command with the -F (force) flag. This will force the fsck command to check the file system for errors and attempt to fix them. Reference: IBM AIX v7 Administrator Specialty Study Guide (page 8-23).
質問 # 29
What AIX feature will allow data to be mirrored to a remote site?
- A. Geographic Logical Volume Manager
- B. Mirror Pools
- C. Remote Volume Groups
- D. Asynchronous Dispersed Logical Volumes
正解:A
質問 # 30
Which logical volume Mirror Write Consistency policy should an AIX V7.2 administrator use to achieve the data consistency between mirrors?
- A. superstrict
- B. round robin
- C. off
- D. active
正解:A
解説:
The superstrict mirror write consistency policy is the most reliable policy for achieving data consistency between mirrors in AIX V7.2. This policy will maintain the data consistency between mirrors by writing the data to both mirrors before the write operation is acknowledged as complete. Reference: IBM AIX v7 Administration Specialty Study Guide (section 10.6.2, pp. 651-652).
質問 # 31
The lspv and Iquerypv commands show a different PVID for an hdisk. How is this possible?
- A. lspv shows the contents of the ODM.
- B. lspv is querying a disk at a different location.
- C. lspv is incorrectly hashing the UDID of the disk.
- D. The system has the wrong version of the lspv command installed.
正解:D
質問 # 32
What are three states a device can have when connected to an AIX system?
- A. Stopped
- B. Blocked
- C. Suspended
- D. Running
- E. Available
- F. Defined
正解:A、E、F
解説:
Devices that are connected to the system can be in one of four states.
Devices that are connected to the system can be in one of the following states:
Item
Description
Undefined
The device is unknown to the system.
Defined
Specific information about the device is recorded in the customized database, but it is unavailable to the system.
Available
A defined device is coupled to the operating system, or the defined device is configured.
Stopped
The device is unavailable but remains known by its device driver.
If a tty device and a printer alternately use the same tty connector, both a tty device and a printer are defined on the same parent and port in the device configuration database. Only one of these devices can be configured at a time. When the tty connector is configured, the printer specific setup information is retained until it is configured again. The device is not removed; it is in the defined state. Maintaining a device in defined state retains customized information for a device that is not currently in use, either before it is first made available or while it is temporarily removed from the system.
If a device driver exists for a device, the device can be made available through the device driver.
https://www.ibm.com/docs/en/aix/7.2?topic=nodes-device-states
質問 # 33
What are three states a device can have when connected to an AIX system?
- A. Stopped
- B. Blocked
- C. Suspended
- D. Running
- E. Available
- F. Defined
正解:A、E、F
解説:
Explanation
Devices that are connected to the system can be in one of four states.
Devices that are connected to the system can be in one of the following states:
Item
Description
Undefined
The device is unknown to the system.
Defined
Specific information about the device is recorded in the customized database, but it is unavailable to the system.
Available
A defined device is coupled to the operating system, or the defined device is configured.
Stopped
The device is unavailable but remains known by its device driver.
If a tty device and a printer alternately use the same tty connector, both a tty device and a printer are defined on the same parent and port in the device configuration database. Only one of these devices can be configured at a time. When the tty connector is configured, the printer specific setup information is retained until it is configured again. The device is not removed; it is in the defined state. Maintaining adevice in defined state retains customized information for a device that is not currently in use, either before it is first made available or while it is temporarily removed from the system.
If a device driver exists for a device, the device can be made available through the device driver.
https://www.ibm.com/docs/en/aix/7.2?topic=nodes-device-states
質問 # 34
An administrator is tasked with installing an open source package. They are told to use the IBM AIX Toolbox for Linux Applications because the organization wants to be able to open tickets with IBM support.
What should the administrator tell the requester?
- A. IBM offers extended support for open source software that is licensed with the hardware.
- B. IBM offers extended support for open source software and they need to verify entitlement.
- C. IBM offers this open source software as-is.
- D. IBM offers standard support for open source software that is licensed with the operating system.
正解:B
解説:
"IBM provides extended support for open source software installed on AIX systems. The customer must verify entitlement for such packages and must contact IBM Support to open a ticket." Therefore, the administrator should tell the requester that IBM offers extended support for open source software, but they need to verify entitlement before they can open a ticket with IBM Support.
質問 # 35
An application administrator needs an account on the AIX server, but does not know it which group it should belong. What is the default group for AIX users, if one was not specified during creation of the account?
- A. users
- B. staff
- C. no group
- D. the group name will be the same as the user name
正解:A
解説:
This is the default primary group for all newly created AIX user accounts. From the IBM AIX v7 Administrator Specialty Study Guide: "By default, all new user accounts are assigned to the 'users' primary group."
質問 # 36
An IT security department would like to limit root user access to only members of the group called system.
Which command will accomplish this?
- A. chgroup admin=root system
- B. chadmin group=system root
- C. cruiser sugroups=system root
- D. chadmin user=root system
正解:A
質問 # 37
......
IBM試験練習テスト問題で高得点を目指そう:https://www.goshiken.com/IBM/S1000-007-mondaishu.html
