[2024年02月]更新のFortinet NSE7_PBC-7.2試験基本問題には解答が付きます
2024年最新の実際に出るFortinet NSE7_PBC-7.2試験問題集と解答
質問 # 12
Refer to the exhibit
An administrator deployed a FortiGate-VM in a high availability (HA)
(active/passive) architecture in Amazon Web Services (AWS) using Terraform for testing purposes. At the same time, the administrator deployed a single Linux server using AWS Marketplace Which two options are available for the administrator to delete all the resources created in this test? (Choose two.)
- A. Use the terraform validate command.
- B. Use the terraform destroy command
- C. Use the terraform destroy all command.
- D. The administrator must manually delete the Linux server.
正解:B、D
解説:
Explanation
A: Use the terraform destroy command. This command is used to remove all the resources that were created using the Terraform configuration1. It is the opposite of the terraform apply command, which is used to create resources. The terraform destroy command will first show a plan of what resources will be destroyed, and then ask for confirmation before proceeding. The command will also update the state file to reflect the changes. D.
The administrator must manually delete the Linux server. This is because the Linux server was not deployed using Terraform, but using AWS Marketplace2. Therefore, Terraform does not have any information about the Linux server in its state file, and cannot manage or destroy it. The administrator will have to use the AWS console or CLI to delete the Linux server manually.
The other options are incorrect because:
There is no terraform validate command. The correct command is terraform plan, which is used to show a plan of what changes will be made by applying the configuration3. However, this command does not delete any resources, it only shows what will happen if terraform apply or terraform destroy is run.
There is no terraform destroy all command. The correct command is terraform destroy, which will destroy all the resources in the current configuration by default1. There is no need to add an all argument to the command.
質問 # 13
Refer to the exhibit
An administrator deployed an HA active-active load balance sandwich in Microsoft Azure. The setup requires configuration synchronization between devices- What are two outcomes from the configured settings? (Choose two.)
- A. FortiGate-VM instances are scaled out automatically according to predefined workload levels.
- B. FortiGate A and FortiGate B are two independent devices.
- C. It does not synchronize the FortiGate hostname
- D. By default, FortiGate uses FGCP
正解:B、C
解説:
Explanation
B: FortiGate A and FortiGate B are two independent devices. This means that they are not part of a cluster or a high availability group, and they do not share the same configuration or state information. They are configured as standalone FortiGates with standalone configuration synchronization enabled1. This feature allows them to synchronize most of their configuration settings with each other, except for some settings that identify the FortiGate to the network, such as the hostname1. D. It does not synchronize the FortiGate hostname. This is one of the settings that are excluded from the standalone configuration synchronization, as mentioned above. The hostname is a unique identifier for each FortiGate device, and it should not be changed by the synchronization process1.
The other options are incorrect because:
FortiGate-VM instances are not scaled out automatically according to predefined workload levels. This is a feature of the auto scaling solution for FortiGate-VM on Azure, which requires a different deployment and configuration than the one shown in the exhibit2. The exhibit shows a static deployment of two FortiGate-VM instances behind an Azure load balancer, which does not support auto scaling.
By default, FortiGate does not use FGCP. FGCP stands for FortiGate Clustering Protocol, which is used to synchronize configuration and state information between FortiGate devices in a cluster or a high availability group3. However, the exhibit shows that the FortiGates are not in a cluster or a high availability group, and they use standalone configuration synchronization instead of FGCP.
質問 # 14
You need a solution to safeguard public cloud-hosted web applications from the OWASP Top 10 vulnerabilities. The solution must support the same region in which your applications reside, with minimum traffic cost Which solution meets the requirements?
- A. Use FortiADC
- B. Use FortiGate
- C. Use FortiWebCloud
- D. Use FortiCNP
正解:C
解説:
Explanation
The correct answer is C. Use FortiWebCloud.
FortiWebCloud is a SaaS cloud-based web application firewall (WAF) that protects public cloud hosted web applications from the OWASP Top 10, zero day threats, and other application layer attacks1.FortiWebCloud also includes robust features such as API discovery and protection, bot mitigation, threat analytics, and advanced reporting2.FortiWebCloud supports multiple regions across the world, and you can choose the region that is closest to your applications to minimize traffic cost3.
The other options are incorrect because:
FortiADC is an application delivery controller that provides load balancing, acceleration, and security for web applications.It is not a dedicated WAF solution and does not offer the same level of protection as FortiWebCloud4.
FortiCNP is a cloud-native platform that provides security and visibility for containerized applications.It is not a WAF solution and does not protect web applications from the OWASP Top 10 vulnerabilities5.
FortiGate is a next-generation firewall (NGFW) that provides network security and threat prevention. It is not a WAF solution and doesnot offer the same level of protection as FortiWebCloud for web applications.It also requires additional configuration and management to deploy in the public cloud6.
1:Overview | FortiWeb Cloud 23.3.0 - Fortinet Documentation2:Web Application Firewall (WAF) & API Protection | Fortinet3: [FortiWeb Cloud WAF-as-a-Service | Fortinet]4: [Application Delivery Controller (ADC) | Fortinet]5: [Fortinet Cloud Native Platform | Fortinet]6: [FortiGate Next-Generation Firewall (NGFW) | Fortinet]
質問 # 15
Refer to the exhibit
You attempted to access the Linux1 EC2 instance directly from the internet using its public IP address in AWS.
However, your connection is not successful.
Given the network topology, what can be the issue?
- A. The Transit Gateway BGP IP address is incorrect.
- B. There is no internet gateway attached to the Spoke VPC A.
- C. There is no connection between VPC A and VPC B.
- D. There is no elastic IP address attached to FortiGate in the Security VPC.
正解:B
解説:
Explanation
This is because the Linux1 EC2 instance is not accessible directly from the internet using its public IP address in AWS.
An internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows communication between instances in your VPC and the internet. Without an internet gateway, the Linux1 EC2 instance cannotreceive or send traffic to or from the internet, even if it has a public IP address assigned to it.
To fix this issue, you need to attach an internet gateway to the Spoke VPC A and configure a route table that directs internet-bound traffic to the internet gateway. You also need to ensure that the Linux1 EC2 instance has a security group that allows inbound and outbound traffic on the desired ports.
[Internet Gateways - Amazon Virtual Private Cloud] : [Attach an Internet Gateway to Your VPC - Amazon Virtual Private Cloud] : [Security Groups for Your VPC - Amazon Virtual Private Cloud]
質問 # 16
What are two main features in Amazon Web Services (AWS) network access control lists (ACLs)? (Choose two.)
- A. Network ACLs are tied to an instance
- B. NetworkACLs are stateless, and inbound and outbound rules are used for traffic filtering
- C. You cannot use Network ACL and Security Group at the same time.
- D. The default network ACL is configured to allow all traffic
正解:B、D
解説:
Explanation
B: The default network ACL is configured to allow all traffic. This means that when you create a VPC, AWS automatically creates a default network ACL for that VPC, and associates it with all the subnets in the VPC1. By default, the default network ACL allows all inbound and outbound IPv4 traffic and, if applicable, IPv6 traffic1. You can modify the default network ACL, but you cannot delete it1. C. Network ACLs are stateless, and inbound and outbound rules are used for traffic filtering. This means that network ACLs do not keep track of the traffic that they allow or deny, and they evaluate each packet separately1. Therefore, you need to create both inbound and outbound rules for each type of traffic that you want to allow or deny1. For example, if you want to allow SSH traffic from a specific IP address to your subnet, you need to create an inbound rule to allow TCP port 22 from that IP address, and an outbound rule to allow TCP port 1024-65535 (the ephemeral ports) to that IP address2.
The other options are incorrect because:
You can use network ACL and security group at the same time. Network ACL and security group are two different types of security layers for your VPC that can work together to control traffic3. Network ACLacts as a firewall for your subnets, while security group acts as a firewall for your instances3. You can use both of them to create a more granular and effective security policy for your VPC.
Network ACLs are not tied to an instance. Network ACLs are associated with subnets, not instances1. This means that network ACLs apply to all the instances in the subnets that they are associated with1. You cannot associate a network ACL with a specific instance. However, you can associate a security group with a specific instance or multiple instances3.
質問 # 17
Refer to Exhibit:
After the initial Terraform configuration in Microsoft Azure, the terraform plan command is run Which two statements about running the plan command are true? (Choose two.)
- A. The terraform plan command will deploy the rest of the resources except the service principle details.
- B. You cannot run the terraform apply command before the terraform plan command.
- C. The terraform plan command makes terraform do a dry run.
- D. You must run the terraform init command once, before the terraform plan command
正解:C、D
解説:
A is incorrect because the terraform plan command will not deploy any resources at all. It will only show the changes that would be made if the terraform apply command was run. The error message in the exhibit indicates that the service principal details are invalid, which means that Terraform cannot authenticate to Azure and cannot create any resources1.
B is incorrect because you can run the terraform apply command without running the terraform plan command first. The terraform apply command will automatically generate a new plan and prompt you to approve it before applying it2. However, running the terraform plan command first can help you preview the changes and avoid any unwanted or unexpected actions.
C is correct because you must run the terraform init command once before the terraform plan command.
The terraform init command initializes a working directory containing Terraform configuration files. It downloads and installs the provider plugins required for your configuration, such as the Azure provider2. It also creates a hidden directory called .terraform to store the plugin binaries and other metadata1. Without running the terraform init command, the terraform plan command will fail because it cannot find the required plugins or modules.
D is correct because the terraform plan command makes Terraform do a dry run. A dry run is a simulation of what would happen if you executed a certain action, without actually performing it. The terraform plan command creates an execution plan, which is a description of the actions that Terraform would take to make your infrastructure match your configuration2. The execution plan shows you what resources will be created, modified, or destroyed, and what attributes will be changed. The execution plan does not affect your infrastructure or state file until you apply it with the terraform apply command1.
質問 # 18
You are automating configuration changes on one of the FortiGate VMS using Linux Red Hat Ansible.
How does Linux Red Hat Ansible connect to FortiGate to make the configuration change?
- A. It uses SSH as a connection method to FortiOS.
- B. It uses a FortiGate internal or external IP address with TCP port 21
- C. It uses an API.
- D. It uses YAML
正解:C
解説:
Explanation
Ansible connects to FortiGate using an API, which is a method of communication between different software components. Ansible uses the fortios_* modules to interact with the FortiOS API, which is a RESTful API that allows configuration and monitoring of FortiGate devices12. Ansible can use either HTTP or HTTPS as the transport protocol, and can authenticate with either a username and password or an API token3.
The other options are incorrect because:
Ansible does not use TCP port 21 to connect to FortiGate. Port 21 is typically used for FTP, which is not supported by FortiOS4.
Ansible does not use SSH as a connection method to FortiOS. SSH is a secure shell protocol that allows remote command execution and file transfer, but it is not the preferred way of automating configuration changes on FortiGate devices.
Ansible does not use YAML to connect to FortiGate. YAML is a data serialization language that Ansible uses to write playbooks and inventory files, but it is not a connection method. References:
Fortinet.Fortios - Ansible Documentation
FortiOS REST API Reference
FortiOS Module Guide - Ansible Documentation
FortiOS 7.0 CLI Reference
[Connection methods and details - Ansible Documentation]
[YAML Syntax - Ansible Documentation]
質問 # 19
How does the immutable infrastructure strategy work in automation?
- A. It runs two live environments for configuration changes.
- B. It runs one idle and two live environments for configuration changes.
- C. It runs one idle and a single live environment for configuration changes.
- D. It runs a single live environment for configuration changes.
正解:A
解説:
Explanation
Immutable infrastructure is a DevOps approach that emphasizes the creation of disposable resources instead of modifying existing ones1. This approach helps to achieve stability, consistency, and predictability in IT operations by reducing the risk of configuration drift and eliminating stateful components1.
One way to implement immutable infrastructure is to use a blue-green deployment strategy, which runs two live environments for configuration changes2. The blue environment is the current production environment, while the green environment is the new version of the application or service. When the green environment is ready, the traffic is switched from blue to green, and the blue environment is destroyed or kept as a backup2.
This way, there is no need to update or patch the existing infrastructure, but rather replace it with a new one.
References:
1: Immutable Infrastructure, Architecture, and its benefits
2: Introduction to Immutable Infrastructure - BMC Software | Blogs
質問 # 20
You must allow an SSH traffic rule in an Amazon Web Services (AWS) network access list (NACL) to allow SSH traffic to travel to a subnetfor temporary testing purposes. When you review the current inbound network ACL rules, you notice that rule number 5 demes SSH and telnet traffic to the subnet What can you do to allow SSH traffic?
- A. You do not have to create any NACL rules because the default security group rule automatically allows SSH traffic to the subnet.
- B. You must create a new allow SSH rule anywhere in the network ACL rule base to allow SSH traffic.
- C. You must create a new allow SSH rule below rule number 5
- D. You must create a new allow SSH rule above rule number 5-
正解:D
解説:
Explanation
Network ACLs are stateless, and they evaluate each packet separately based on the rules that you define. The rules are processed in order, starting with the lowest numbered rule1. If the traffic matches a rule, the rule is applied and no further rules are evaluated1. Therefore, if you want to allow SSH traffic to a subnet, you must create a new allow SSH rule above rule number 5, which denies SSH and telnet traffic. Otherwise, the deny rule will take precedence and block the SSH traffic.
The other options are incorrect because:
Creating a new allow SSH rule below rule number 5 will not allow SSH traffic, because the deny rule will be evaluated first and block the traffic.
Creating a new allow SSH rule anywhere in the network ACL rule base will not guarantee that SSH traffic will be allowed, because it depends on the order of the rules. If the allow SSH rule is below the deny rule, it will not be effective.
You cannot rely on the default security group rule to allow SSH traffic to the subnet, because network ACLs act as an additional layer of security for your VPC. Even if your security group allows SSH traffic, your network ACL must also allow it. Otherwise, the traffic will be blocked at the subnet level.
質問 # 21
Refer to the exhibit.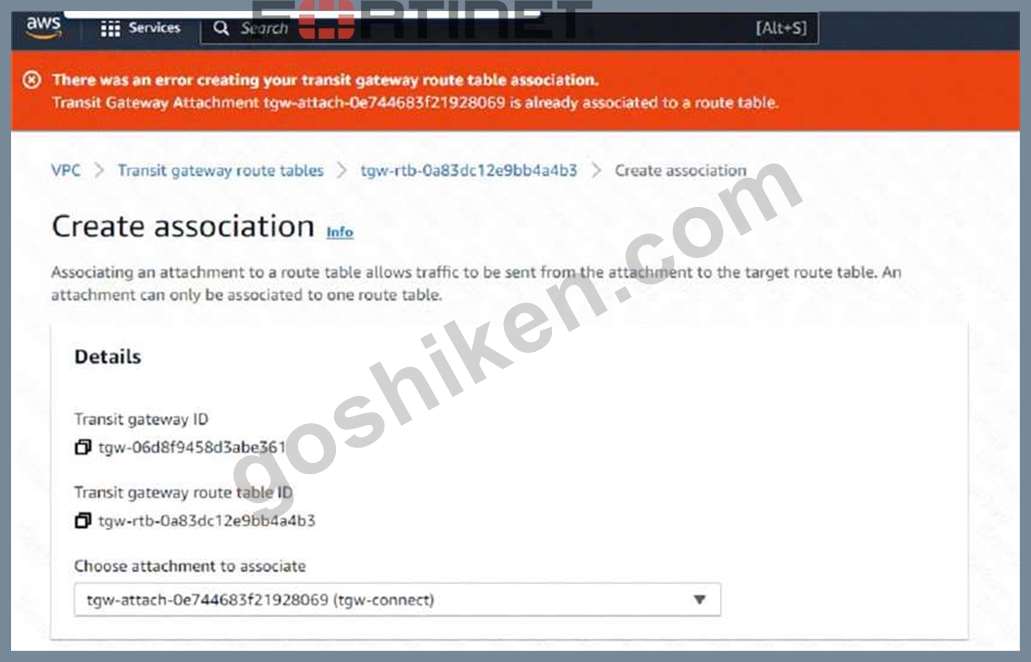
You are configuring a second route table on a Transit Gateway to accommodate east-west traffic inspection between two VPCs_ However, you are getting an error during the transit gateway route table association With the Connect attachment.
Which action Should you take to fulfill your requirement?
- A. Add both Associations and Propagations in the second TGW route table.
- B. Delete the both Connect and Transport attachments from the first TGW route table
- C. In the second route table: create a propagation with the Connect attachment.
- D. Add a static route in the Routes section
正解:C
解説:
Explanation
The error message indicates that the Connect attachment is already associated with another transit gateway route table. You cannot associate the same attachment with more than one route table. However, you can propagate the same attachment to multiple route tables. Therefore, to fulfill your requirement of configuring a second route table for east-west traffic inspection between two VPCs, you need to create a propagation with the Connect attachment in the second route table. This will allow the second route table to learn the routes from the Connect attachment and forward the traffic to the securityVPC1. You also need to associate the second route table with the Transport attachment, which is the transit gateway attachment for the security VPC1.
References:
Transit gateway route tables - Amazon VPC | AWS Documentation
Getting started with transit gateways - Amazon VPC | AWS Documentation
Configuring TGW route tables | FortiGate Public Cloud 7.4.0 | Fortinet Document Library
質問 # 22
Refer to the exhibit
A customer has deployed an environment in Amazon Web Services (AWS) and is now trying to send outbound traffic from the Linux1 and Linux2 instances to the internet through the security VPC (virtual private cloud). The FortiGate policies are configured to allow all outbound traffic; however, the traffic is not reaching the FortiGate internal interface. Assume there are no issues with the Transit Gateway (TGW) configuration Which two settings must the customer add to correct the issue? (Choose two.)
- A. Both landing subnets in the spoke VPCs must have a 0.0.0.0/0 traffic route to the Internet Gateway (IOW).
- B. Both landing subnets in the security VPC must have a 0.0.0.0/0 traffic route to the FortiGate port2.
- C. The four landing subnets in all the VPCs must have a 0.0 0 0/0 traffic route to the TGW
- D. Both landing subnets in the spoke VPCs must have a 0.0 00/0 traffic route to the TGW
正解:B、D
解説:
Explanation
The correct answer is B and C. Both landing subnets in the spoke VPCs must have a 0.0.0.0/0 traffic route to the TGW. Both landing subnets in the security VPC must have a 0.0.0.0/0 traffic route to the FortiGate port2.
According to the AWS documentation for Transit Gateway, a transit gateway is a network transit hub that connects VPCs and on-premises networks. To send outbound traffic from the Linux instances to the internet through the security VPC, you need to do the following steps:
In the main subnet routing table in the spoke VPCs, add a new route with destination 0.0.0.0/0, next hop TGW. This route directs all traffic from the Linux instances to the TGW, which can then forward it to the appropriate destination based on the TGW route table.
In the main subnet routing table in the security VPC, add a new route with destination 0.0.0.0/0, next hop FortiGate port2. This route directs all traffic from the TGW to the FortiGate internal interface, where it can be inspected and allowed by the FortiGate policies.
The other options are incorrect because:
Adding a 0.0.0.0/0 traffic route to the Internet Gateway (IGW) in the spoke VPCs is not correct, as this would bypass the TGW and the security VPC and send all traffic directly to the internet.
Adding a 0.0.0.0/0 traffic route to the TGW in all the VPCs is not necessary, as only the spoke VPCs need to send traffic to the TGW. The security VPC needs to send traffic to the FortiGate port2.
Transit Gateways - Amazon Virtual Private Cloud:Fortinet Documentation Library - Deploying FortiGate VMs on AWS
質問 # 23
You are troubleshooting an Azure SDN connectivity issue with your FortiGate VM Which two queries does that SDN connector use to interact with the Azure management API? (Choose two.)
- A. The first query is targeted to IP address 8.8
- B. The first query is targeted to a special IP address to get a token.
- C. There is only one query initiating from FortiGate port1 -
- D. Some queries are made to manage public IP addresses.
正解:B、D
解説:
Explanation
The Azure SDN connector uses two types of queries to interact with the Azure management API. The first query is targeted to a special IP address to get a token. This token is used to authenticate the subsequent queries. The second type of query is used to retrieve information about the Azure resources, such as virtual machines, network interfaces, network security groups, and public IP addresses. Some queries are made to manage public IP addresses, such as assigning or releasing them from the FortiGate VM. References: Configuring an SDN connector in Azure, Azure SDN connector using service principal, Troubleshooting Azure SDN connector
質問 # 24
Refer to the exhibit
You are tasked with deploying FortiGate using Terraform. When you run the terraform version command during the Terraform installation, you get an error message.
What could be the reason that you are getting the command not found error?
- A. You must reinstall Terraform
- B. You must change the directory location to the root directory
- C. You must move the binary file to the bin directory.
- D. You must assign correct permissions to the ec2-user.
正解:C
解説:
Explanation
According to the Terraform documentation for installing Terraform on Linux1, you need to download a zip archive that contains a single binary file called terraform. You need to unzip the archive and move the binary file to a directory that is included in your system's PATH environment variable, such as /usr/local/bin. This way, you can run the terraform command from any directory without specifying the full path1.
If you do not move the binary file to the bin directory, you will get a command not found error when you try to run the terraform version command, as shown in the screenshot. To fix this error, you need to move the binary file to the bin directory or specify the full path of the binary file when running the command1.
1: Install Terraform | Terraform - HashiCorp Learn
質問 # 25
Refer to the exhibit.
You are troubleshooting a FortiGate HA floating IP issue with Microsoft Azure. After the failover, the new primary device does not have the previous primary device floating IP address.
What could be the possible issue With this scenario?
- A. FortiGate port4 does not have internet access.
- B. The Azure service principle account must have a contributor role.
- C. A wrong client secret credential is used
- D. The error is caused by credential time expiration.
正解:B
解説:
Explanation
In this scenario, the issue is caused by the Azure service principle account nothaving a contributor role. This is required for the FortiGate HA floating IP to work properly. Without this role, the new primary device will not have the previous primary device floating IP address after failover. References: Fortinet Public Cloud Security knowledge source documents or study guide.
https://docs.fortinet.com/product/fortigate-public-cloud/7.2
質問 # 26
Refer to the exhibit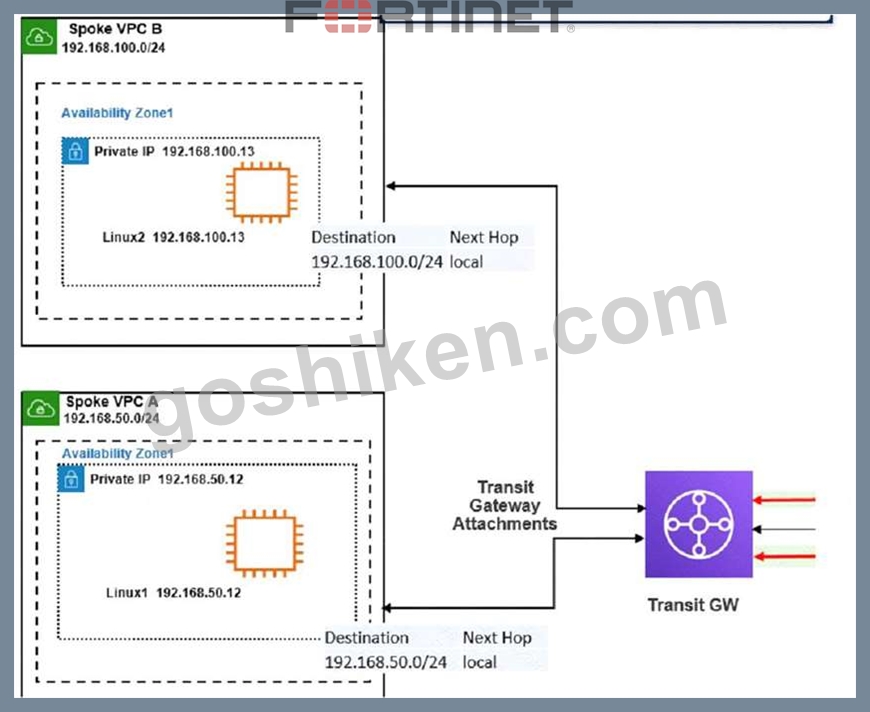
The exhibit shows a customer deployment of two Linux instances and their main routing table in Amazon Web Services (AWS). The customer also created a Transit Gateway (TGW) and two attachments Which two steps are required to route traffic from Linux instances to the TGWQ (Choose two.)
- A. In the TGW route table, associate two attachments.
- B. In the main subnet routing table in VPC A and B, add a new route with destination 0_0.0.0/0, next hop Internet gateway(IGW).
- C. In the main subnet routing table in VPC A and B, add a new route with destination 0_0.0.0/0, next hop TGW.
- D. In the TGW route table, add route propagation to 192.168.0 0/16
正解:A、C
解説:
Explanation
According to the AWS documentation for Transit Gateway, a Transit Gateway is a network transit hub that connects VPCs and on-premises networks. To route traffic from Linux instances to the TGW, you need to do the following steps:
In the TGW route table, associate two attachments. An attachment is a resource that connects a VPC or VPN to a Transit Gateway. By associating the attachments to the TGW route table, you enable the TGW to route traffic between the VPCs and the VPN.
In the main subnet routing table in VPC A and B, add a new route with destination 0_0.0.0/0, next hop TGW. This route directs all traffic from the Linux instances to the TGW, which can then forward it to the appropriate destination based on the TGW route table.
The other options are incorrect because:
In the TGW route table, adding route propagation to 192.168.0 0/16 is not necessary, as this is already the default route for the TGW. Route propagation allows you to automatically propagate routes from your VPC or VPN to your TGW route table.
In the main subnet routing table in VPC A and B, adding a new route with destination 0_0.0.0/0, next hop Internet gateway (IGW) is not correct, as this would bypass the TGW and send all traffic directly to the internet. An IGW is a VPC component that enables communication between instances in your VPC and the internet.
[Transit Gateways - Amazon Virtual Private Cloud]
質問 # 27
Your administrator instructed you to deploy an Azure vWAN solution to create a connection between the main company site and branch sites to the other company VNETs.
What are the two best connection solutions available between your company headquarters, branch sites, and the Azure vWAN hub? (Choose two.)
- A. SSL VPN connections
- B. VPN Gateway
- C. GRE tunnels
- D. An L2TP connection
- E. ExpressRoute
正解:B、E
解説:
Explanation
The two best connection solutions available between your company headquarters, branch sites, and the Azure vWAN hub are A. ExpressRoute and E. VPN Gateway.
According to the Azure documentation for Virtual WAN, ExpressRoute and VPN Gateway are two of the supported connectivity options for connecting your on-premises sites and Azure virtual networks to the Azure vWAN hub1. These options provide secure, reliable, and high-performance connectivity for your network traffic.
ExpressRoute is a service that lets you create private connections between your on-premises sites and Azure.ExpressRoute connections do not go over the public internet, and offer more reliability, faster speeds, lower latencies, and higher security than typical connections over the internet2.
VPN Gateway is a service that lets you create encrypted connections between your on-premises sites and Azure over the internet using IPsec/IKE protocols.VPN Gateway also supports point-to-site VPN connections for individual clients using OpenVPN or IKEv2 protocols3.
The other options are incorrect because:
GRE tunnels are not a supported connectivity option for Azure vWAN. GRE is a protocol that encapsulates packets for tunneling purposes.GRE tunnels are established between the connect attachment and your appliance in Azure vWAN4.
SSL VPN connections are not a supported connectivity option for Azure vWAN. SSL VPN is a type of VPN that uses the Secure Sockets Layer (SSL) protocol to secure the connection between a client and a server.SSL VPN is not compatible with the Azure vWAN hub5.
An L2TP connection is not a supported connectivity option for Azure vWAN. L2TP is a protocol that creates a tunnel between two endpoints at the data link layer (Layer 2) of the OSI model.L2TP is not compatible with the Azure vWAN hub.
1:Azure Virtual WAN Overview | Microsoft Learn2: [ExpressRoute overview - Azure ExpressRoute | Microsoft Docs]3: [VPN Gateway - Virtual Networks | Microsoft Azure]4: [Transit Gateway Connect - Amazon Virtual Private Cloud]5: [SSL VPN - Wikipedia] : [Layer 2 Tunneling Protocol - Wikipedia]
質問 # 28
......
合格保証付きのNSE 7 Network Security Architect NSE7_PBC-7.2試験問題集:https://www.goshiken.com/Fortinet/NSE7_PBC-7.2-mondaishu.html
NSE7_PBC-7.2練習テストエンジンで今すぐ使おう40試験問題:https://drive.google.com/open?id=1aJyTaMxv8Ff7jKgHmSbGMlwAiMfxy9PD
