[2024年04月30日] NSE5_FCT-7.0 PDFで最近更新された問題です集試験点数を伸ばそう
NSE5_FCT-7.0完全版問題集には無料PDF問題で合格させる
Fortinet NSE5_FCT-7.0認定試験は、Fortinetのエンドポイントセキュリティソリューションの展開と管理に必要な知識とスキルを評価するために設計されたベンダー固有の試験です。この認定試験では、Forticlient EMS 7.0のインストールと構成、エンドポイントコンプライアンス、エンドポイントテレメトリ、エンドポイント保護などの幅広いトピックをカバーしています。この試験は、複数選択の質問で構成されており、候補者の知識を実際のシナリオに適用する能力をテストするように設計されています。
質問 # 18
An administrator installs FortiClient EMS in the enterprise.
Which component is responsible for enforcing protection and checking security posture?
- A. FortiClient vulnerability scan
- B. FortiClient EMS tags
- C. FortiClient
- D. FortiClient EMS
正解:C
質問 # 19
Refer to the exhibit.
Based on the Security Fabric automation settings, what action will be taken on compromised endpoints?
- A. Endpoints will be banned on FortiGate
- B. Endpoints will be quarantined through EMS
- C. Endpoints will be quarantined through FortiSwitch
- D. An email notification will be sent for compromised endpoints
正解:B
質問 # 20
Which three types of antivirus scans are available on FortiClient? (Choose three )
- A. Flow scan
- B. Quick scan
- C. Proxy scan
- D. Full scan
- E. Custom scan
正解:B、D、E
質問 # 21
Refer to the exhibit.
Which shows FortiClient EMS deployment profiles.
When an administrator creates a deployment profile on FortiClient EMS, which statement about the deployment profile is true?
- A. Deployment-2 will install FortiClient on both the AD group and workgroup
- B. Deployment-1 will upgrade FortiClient only on the workgroup
- C. Deployment-2 will upgrade FortiClient on both the AD group and workgroup
- D. Deployment-1 will install FortiClient on new AD group endpoints
正解:C
質問 # 22
When site categories are disabled in FortiClient webfilter and antivirus (malicious websites), which feature can be used to protect the endpoint from malicious web access?
- A. Real-time protection list
- B. Block malicious websites on antivirus
- C. FortiSandbox URL list
正解:A
質問 # 23
Which two statements are true about the ZTNA rule? (Choose two. )
- A. It enforces access control
- B. It redirects the client request to the access proxy
- C. It applies security profiles to protect traffic
- D. It defines the access proxy
正解:A
質問 # 24
Refer to the exhibit.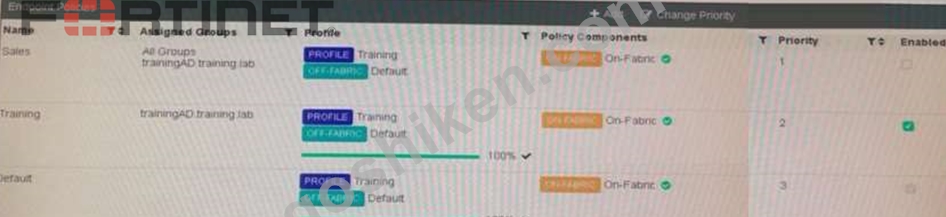
Which shows multiple endpoint policies on FortiClient EMS.
Which policy is applied to the endpoint in the AD group trainingAD?
- A. The Sales policy
- B. The Training policy
- C. Both the Sales and Training policies because their priority is higher than the Default policy
- D. The Default policy because it has the highest priority
正解:B
解説:
Explanation
Training policy because:
- Policy is enabled
- Priority is better than Default Policy
質問 # 25
Refer to the exhibit.
Based on the settings shown in the exhibit, which action will FortiClient take when users try to access www.facebook.com?
- A. FortiClient will block access to Facebook and its subdomains.
- B. FortiClient will allow access to Facebook
- C. FortiClient will monitor only the user's web access to the Facebook website
- D. FortiClient will prompt a warning message to warn the user before they can access the Facebook website
正解:B
質問 # 26
Refer to the exhibits.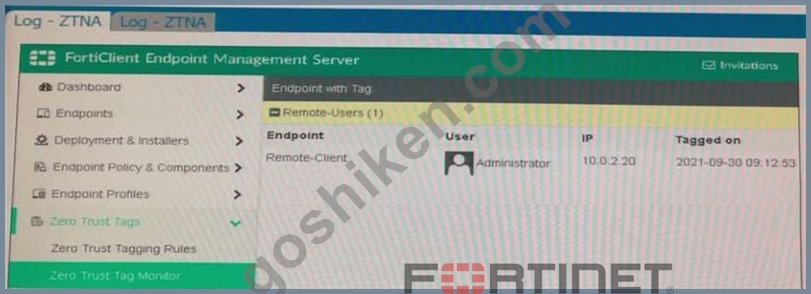
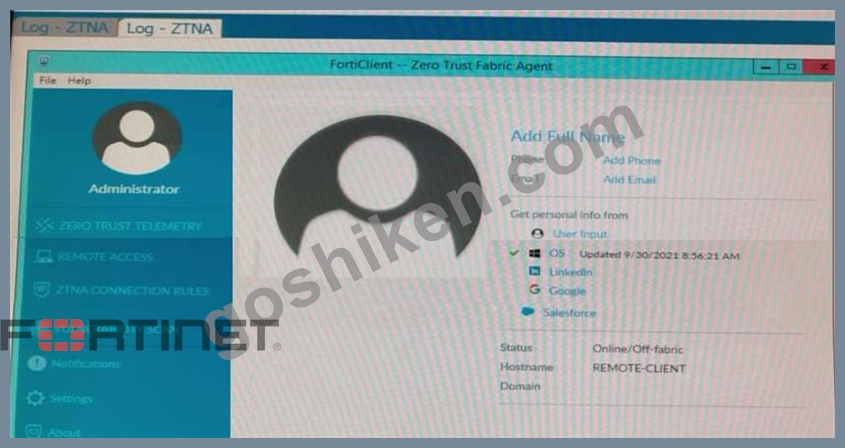
Which show the Zero Trust Tag Monitor and the FortiClient GUI status.
Remote-Client is tagged as Remote-Users on the FortiClient EMS Zero Trust Tag Monitor.
What must an administrator do to show the tag on the FortiClient GUI?
- A. Change the user identity settings to enable tag visibility
- B. Update tagging rule logic to enable tag visibility
- C. Change the FortiClient system settings to enable tag visibility
- D. Change the endpoint control setting to enable tag visibility
正解:C
質問 # 27
Which two statements are true about the ZTNA rule? (Choose two. )
- A. It redirects the client request to the access proxy
- B. It applies security profiles to protect traffic
- C. It defines the access proxy
正解:A
質問 # 28
An administrator has a requirement to add user authentication to the ZTNA access for remote or off-fabric users Which FortiGate feature is required m addition to ZTNA?
- A. FortiGate certificates
- B. FortiGate endpoint control
- C. FortiGate FSSO
- D. FortiGate explicit proxy
正解:D
質問 # 29
An administrator is required to maintain a software vulnerability on the endpoints, without showing the feature on the FortiClient dashboard. What must the administrator do to achieve this requirement?
- A. Use the default endpoint profile
- B. Disable select the vulnerability scan feature in the deployment package
- C. Click the hide icon on the vulnerability scan tab
- D. Select the vulnerability scan feature in the deployment package, but disable the feature on the endpoint profile
正解:D
質問 # 30
Which two benefits are benefits of using multi-tenancy mode on FortiClient EMS? (Choose two.)
- A. Separate host servers manage each site.
- B. It provides granular access and segmentation.
- C. The fabric connector must use an IP address to connect to FortiClient EMS
- D. Licenses are shared among sites.
正解:A、B
質問 # 31
A new chrome book is connected in a school's network.
Which component can the EMS administrator use to manage the FortiClient web filter extension installed on the Google Chromebook endpoint?
- A. FortiClient site categories
- B. FortiClient customer URL list
- C. FortiClient web filter extension
正解:A
質問 # 32
An administrator needs to connect FortiClient EMS as a fabric connector to FortiGate. What is the prerequisite to get FortiClient EMS to connect to FortiGate successfully?
- A. Import and verify the FortiClient EMS root CA certificate on FortiGate
- B. Revoke and update the FortiClient EMS root CA.
- C. Import and verify the FortiClient client certificate on FortiGate.
- D. Revoke and update the FortiClient client certificate on EMS.
正解:A
解説:
Explanation
The FortiClient EMS root CA certificate needs to be imported and verified on the FortiGate appliance. This allows the FortiGate to trust the certificate authority (CA) used by FortiClient EMS for issuing client certificates. By importing and verifying the root CA certificate, FortiGate can establish a secure connection with FortiClient EMS and validate the authenticity of the client certificates presented during the connection process.
質問 # 33
An administrator configures ZTNA configuration on the FortiGate for remote users. Which statement is true about the firewall policy?
- A. It applies security profiles to protect traffic
- B. It redirects the client request to the access proxy
- C. It defines the access proxy
- D. It enforces access control
正解:A
解説:
https://docs.fortinet.com/document/fortigate/7.0.0/new-features/194961/basic-ztna-configuration
質問 # 34
When site categories are disabled in FortiClient webfilter and antivirus (malicious websites), which feature can be used to protect the endpoint from malicious web access?
- A. Real-time protection list
- B. Block malicious websites on antivirus
- C. FortiSandbox URL list
正解:A
解説:
Explanation
Site Categories enables site categories from FortiGuard. When site categories are disabled, FortiClient is protected by the exclusion list. For all categories below, you can configure an action for the entire site category by selecting either Block, Warn, Allow, or Monitor. Each site category is shown on this slide.
質問 # 35
Refer to the exhibit.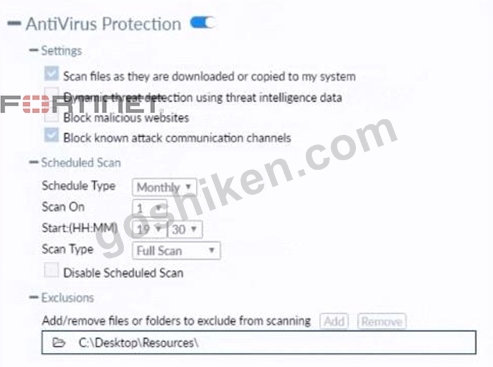
Based on the settings shown in the exhibit which statement about FortiClient behavior is true?
- A. FortiClient blocks and deletes infected files after scanning them.
- B. FortiClient copies infected files to the Resources folder without scanning them.
- C. FortiClient scans infected files when the user copies files to the Resources folder
- D. FortiClient quarantines infected files and reviews later, after scanning them.
正解:D
質問 # 36
What is the function of the quick scan option on FortiClient?
- A. It scans programs and drivers that are currently running, for threats.
- B. It scans executable files, DLLs, and drivers that are currently running, for threats.
- C. It allows users to select a specific file folder on their local hard disk drive (HDD), to scan for threats.
- D. It performs a full system scan including all files, executable files, DLLs, and drivers for threats.
正解:A
質問 # 37
Refer to the exhibits.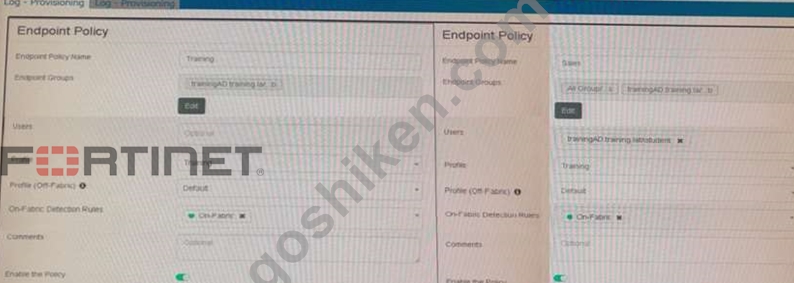
Which shows the configuration of endpoint policies.
Based on the configuration, what will happen when someone logs in with the user account student on an endpoint in the trainingAD domain?
- A. FortiClient EMS will assign the Default policy
- B. FortiClient EMS will assign the Training policy
- C. FortiClient EMS will assign the Training policy for on-fabric endpoints and the Sales policy for the off-fabric endpoint
- D. FortiClient EMS will assign the Sales policy
正解:B
質問 # 38
A new chrome book is connected in a school's network.
Which component can the EMS administrator use to manage the FortiClient web filter extension installed on the Google Chromebook endpoint?
- A. FortiClient web filter extension
- B. FortiClient customer URL list
- C. FortiClient site categories
- D. FortiClient EMS
正解:A
質問 # 39
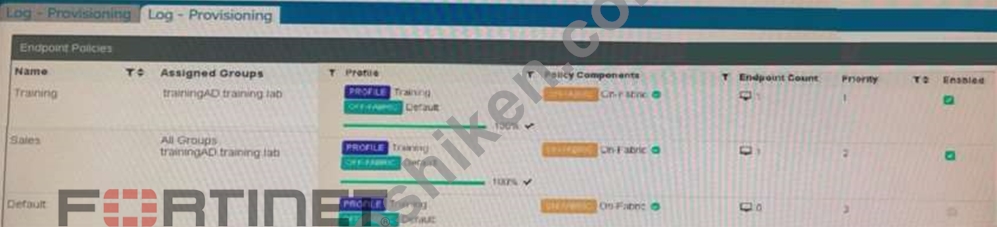
Refer to the exhibit.
Which shows multiple endpoint policies on FortiClient EMS.
Which policy is applied to the endpoint in the AD group trainingAD?
- A. The Sales policy
- B. The Training policy
- C. The Default policy because it has the highest priority
- D. Both the Sales and Training policies because their priority is higher than the Default policy
正解:D
質問 # 40
Refer to the exhibit, which shows the Zero Trust Tagging Rule Set configuration.
Which two statements about the rule set are true? (Choose two.)
- A. The endpoint must satisfy that only AV software is installed and running.
- B. The endpoint must satisfy that antivirus is installed and running and Windows 10 is running.
- C. The endpoint must satisfy that only Windows 10 is running.
- D. The endpoint must satisfy that only Windows Server 2012 R2 is running.
正解:A、B
質問 # 41
Refer to the exhibit.
Based on the settings shown in the exhibit, which two actions must the administrator take to make the endpoint compliant? (Choose two.)
- A. Enable the webfilter profile
- B. Patch applications that have vulnerability rated as high or above
- C. Run Calculator application on the endpoint
- D. Integrate FortiSandbox for infected file analysis
正解:B、C
質問 # 42
Refer to the exhibits.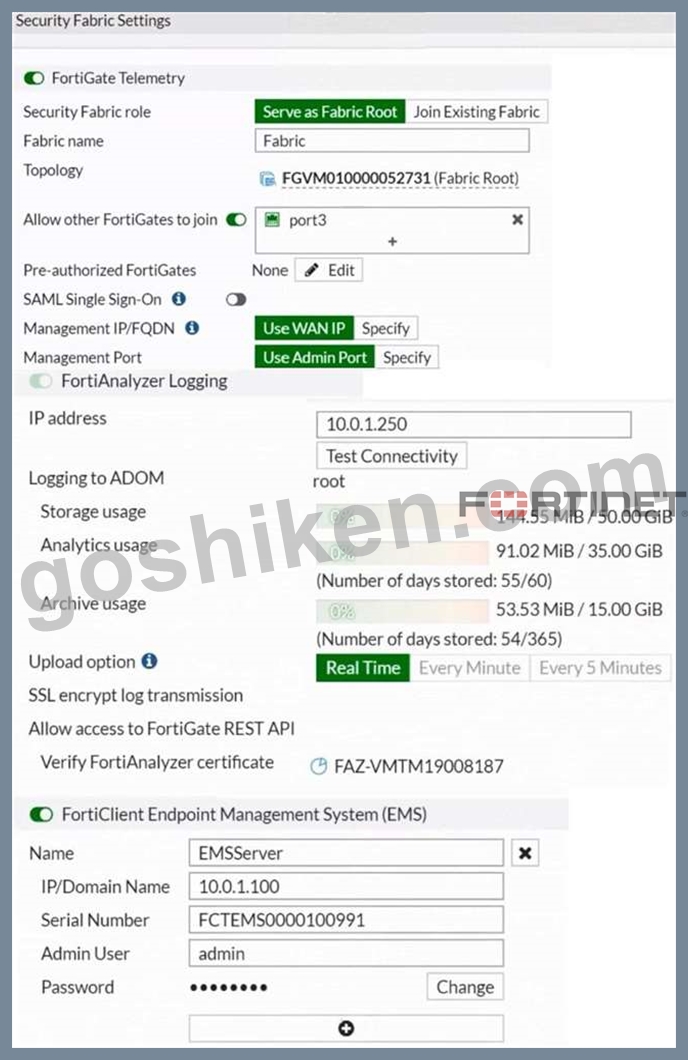
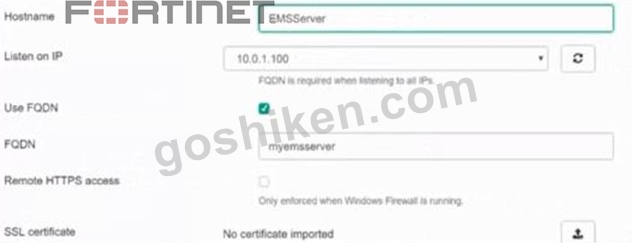
Based on the FortiGate Security Fabric settings shown in the exhibits, what must an administrator do on the EMS server to successfully quarantine an endpoint. when it is detected as a compromised host (loC)?
- A. The administrator must authorize FortiGate on FortiAnalyzer.
- B. The administrator must enable remote HTTPS access to EMS.
- C. The administrator must enable SSH access to EMS.
- D. The administrator must enable FQDN on EMS.
正解:B
質問 # 43
......
100%更新されたのはFortinet NSE5_FCT-7.0限定版PDF問題集:https://www.goshiken.com/Fortinet/NSE5_FCT-7.0-mondaishu.html
無料NSE 5 Network Security Analyst NSE5_FCT-7.0公式認定ガイドPDFダウンロード:https://drive.google.com/open?id=1bd_rChTz_E3N1pqDjP1mL_8DWryPyEem
