CyberArk PAM-CDE-RECERT試験問題集にはPDF問題とテストエンジンを試せ!
最新PAM-CDE-RECERT試験問題集には合格保証付きます
質問 # 108
Match each PTA alert category with the PTA sensors that collect the data for it.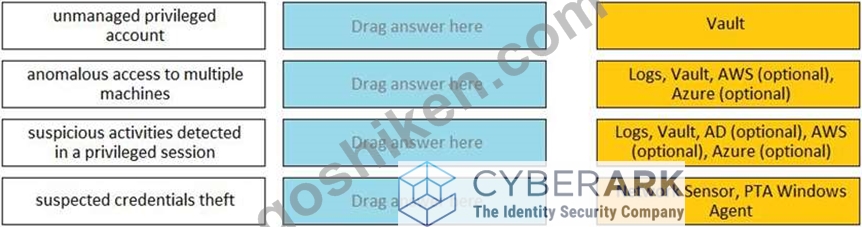
正解:
解説: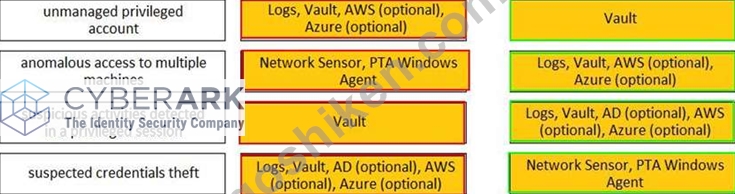
質問 # 109
Users who have the 'Access Safe without confirmation' safe permission on a safe where accounts are configured for Dual control, still need to request approval to use the account.
- A. FALSE
- B. TRUE
正解:B
質問 # 110
If a transparent user matches two different directory mappings, how does the system determine which user template to use?
- A. The system will grant only the Vault authorizations that are listed in both templates.
- B. The system will use the template for the mapping listed first.
- C. The system will use the template for the mapping listed last.
- D. The system will grant all of the Vault authorizations from the two templates.
正解:B
質問 # 111
The System safe allows access to the Vault configuration files.
- A. FALS
- B. TRUE
正解:B
質問 # 112
You are onboarding an account that is not supported out of the box.
What should you do first to obtain a platform to import?
- A. Search common community portals like stackoverflow, reddit, github for an existing platform.
- B. From the platforms page, uncheck the "Hide non-supported platforms" checkbox and see if a platform meeting your needs appears.
- C. Visit the CyberArk marketplace and search for a platform that meets your needs.
- D. Create a service ticket in the customer portal explaining the requirements of the custom platform.
正解:D
質問 # 113
The password upload utility must run from the Central Policy Manager (CPM) server.
- A. False
- B. True
正解:A
質問 # 114
Which CyberArk group does a user need to be part of to view recordings or live monitor sessions?
- A. Auditors
- B. DR Users
- C. Operators
- D. Vault Admin
正解:A
質問 # 115
In addition to disabling Windows services or features not needed for PVWA operations, which tasks does PVWA Hardening.ps1 perform when run?
- A. Configures Windows Firewall: Removes all installation files.
- B. Performs IIS hardening: Configures all group policy settings
- C. Performs IIS hardening: Imports the CyberArk INF configuration
- D. Performs IIS hardening: Renames the local Administrator Account
正解:B
質問 # 116
PTA can automatically suspend sessions if suspicious activities are detected in a privileged session, but only if the session is made via the CyberArk PSM.
- A. False, the PTA can suspend sessions whether the session is made via the PSM or not
- B. True
正解:A
質問 # 117
According to the default web options settings, which group grants access to the reports page?
- A. Auditors
- B. PVWAUsers
- C. PVWAMonitor
- D. Vault administrators
正解:C
質問 # 118
What is the chief benefit of PSM?
- A. 'Privileged session isolation' and 'Privileged session recording'
- B. Privileged session recording
- C. Automatic password management
- D. Privileged session isolation
正解:B
質問 # 119
For Digital Vault Cluster in a high availability configuration, how does the cluster determine if a node is down?
- A. The Digital Vault Cluster does not detect a node failure.
- B. The shared storage array is offline.
- C. The heartbeat s no longer detected on the private network.
- D. An alert is generated in the Windows Event log.
正解:C
質問 # 120
What is the purpose of the Interval setting in a CPM policy?
- A. To control how long the CPM rests between password changes.
- B. To control the maximum amount of time the CPM will wait for a password change to complete.
- C. To control how often the CPM looks for User Initiated CPM work.
- D. To control how often the CPM looks for System Initiated CPM work.
正解:D
質問 # 121
Users can be resulted to using certain CyberArk interfaces (e.g.PVWA or PACLI).
- A. FALS
- B. TRUE
正解:B
質問 # 122
One can create exceptions to the Master Policy based on ____________________.
- A. Policies
- B. Platforms
- C. Accounts
- D. Safes
正解:C
質問 # 123
Secure Connect provides the following. Choose all that apply.
- A. Session Recording
- B. PSM connections to target devices that are not managed by CyberArk.
- C. PSM connections from a terminal without the need to login to the PVWA
- D. Real-time live session monitoring.
正解:A、B
質問 # 124
Which type of automatic remediation can be performed by the PTA in case of a suspected credential theft security event?
- A. Password reconciliation
- B. Session suspension
- C. Session termination
- D. Password change
正解:D
質問 # 125
What is the purpose of the password change process?
- A. To generate a new complex password
- B. To change the password of an account according to organizationally defined password rules
- C. To test that CyberArk is storing accurate credentials for accounts
- D. To allow CyberArk to manage unknown or lost credentials
正解:B
質問 # 126
It is possible to leverage DNA to provide discovery functions that are not available with auto-detection.
- A. FALS
- B. TRUE
正解:B
質問 # 127
Which tools are used during a CPM renaming process?
- A. CreateCredFile Utility
- B. PMTerminal.exe
- C. CPMinDomain_Hardening.ps1
- D. APIKeyManager Utility
- E. Data Execution Prevention
正解:A、D
質問 # 128
Multiple Password Vault Web Access (PVWA) servers can be load balanced.
- A. True
- B. False
正解:A
質問 # 129
Accounts Discovery allows secure connections to domain controllers.
- A. TRUE
- B. FALSE
正解:B
質問 # 130
Customers who have the 'Access Safe without confirmation' safe permission on a safe where accounts are configured for Dual control, still need to request approval to use the account.
- A. TRUE
- B. FALSE
正解:B
質問 # 131
......
CyberArk CDE再認定試験は、CyberArkソリューションに関連する幅広いトピックをカバーする包括的な試験です。これには、パスワード管理、資格情報管理、特権アカウント管理、セッション管理などが含まれます。この試験は、オンプレミス、クラウド、ハイブリッド環境を含む様々な環境でCyberArkソリューションを維持および再認定する管理者の知識とスキルをテストするために設計されています。
信頼できるCyberArk CDE Recertification PAM-CDE-RECERT問題集PDFには2023年11月27日更新された問題です:https://www.goshiken.com/CyberArk/PAM-CDE-RECERT-mondaishu.html
