GoShikenからの試験合格準備の必需品DEA-1TT5試験トレーニング問題
有効なパス率はEMC DCA-ISMのDEA-1TT5試験問題
質問 # 32
What does the "X" represent in the exhibit?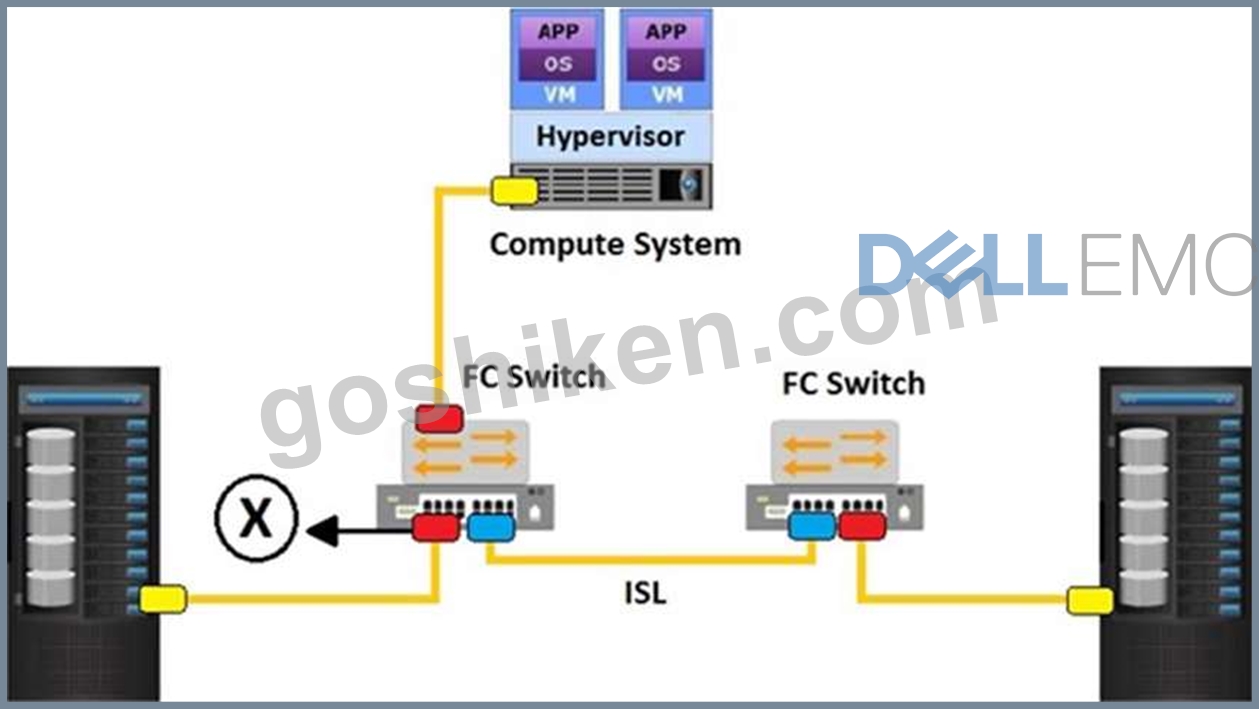
- A. F_port
- B. E_port
- C. NL_port
- D. N_port
正解:D
質問 # 33
What is the lowest to highest order of I/O performance among these storage devices?
- A. SSD --> SCM--> SATA--> DRAMcorrect
- B. SATA--> SSD--> SCM --> DRAM
- C. SCM--> SSD --> DRAM--> SATA
- D. DRAM--> SCM--> SSD-> SATA
正解:A
質問 # 34
Which plane of the SDDC architecture provides a CL and GUI for IT to administrator the infrastructure and to configure policies?
- A. Control plane
- B. Service plane
- C. Data plane
- D. Management plane
正解:D
質問 # 35
Which feature of an object-based storage system abstracts and provides a common view of storage independent of location to applications?
Response:
- A. Global namespace
- B. Scale-out architecture
- C. Multi-tenancy
- D. Flexible data access
正解:A
質問 # 36
What is an accurate statement about Storage Class Memory (SCM)?
- A. SCM read and write speeds are slower than flash
- B. SCM has volatile memory
- C. SCM is faster than DRAM
- D. SCM can be addressed at the bit or word level
正解:D
質問 # 37
What is a specialized replication technique that enables moving data from one storage system to another within a data center without incurring downtime?
Response:
- A. Image-level backup
- B. Archive
- C. Migration
- D. VM-level backup
正解:C
質問 # 38
Which type of zoning does the "X" represent?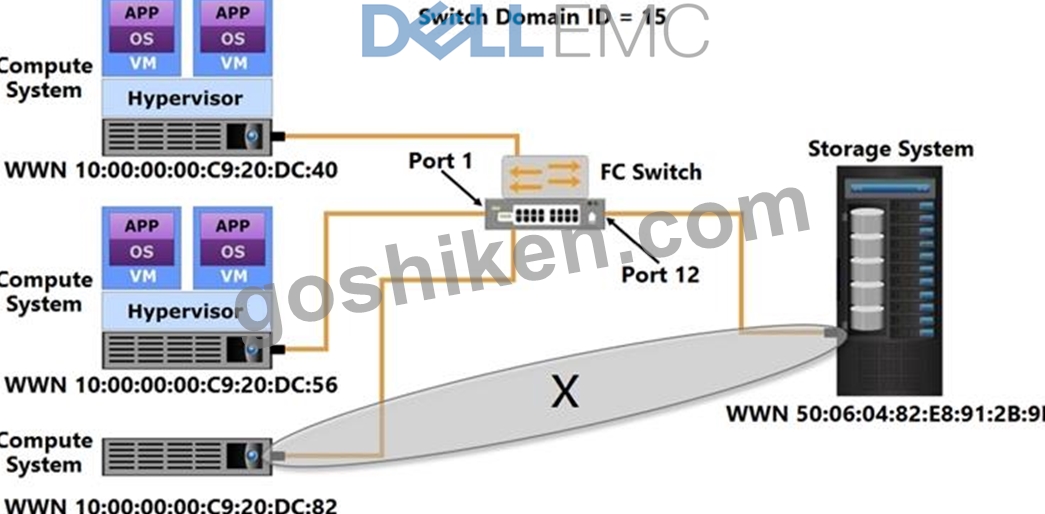
- A. WWN zoning
- B. Port zoning
- C. Fabric zoning
- D. Mixed zoning
正解:C
質問 # 39
What is an accurate statement about variable prefetching?
Response:
- A. Many blocks that have recently been written to storage by the compute system are retrieved and placed in cache.
- B. Storage system prefetches data in multiples of the original I/O request size from the compute system.
- C. Many non-contiguous blocks that are not currently required can be retrieved from cache in advance.
- D. Storage system prefetches many non-contiguous blocks of data, with varied sizes, from cache.
正解:D
質問 # 40
What is a function of a continuous data protection (CDP) appliance?
- A. Intercepts writes to the production volume and splits each write into two copies
- B. Manages both local and remote replications within and across data centers
- C. Stores all data that has changed from the time the replication session started
- D. Migrates deduplicated data from the source volume to the target volume during replication
正解:C
解説:
Explanation
A continuous data protection (CDP) is a system that backs up data on a computer system every time a change is made. CDP maintains a continuous journal of data changes and makes it possible to restore a system to any previous point in time.
質問 # 41
What is a function of a cloud-based object storage gateway?
Response:
- A. Converting a block storage system into an object storage system for cloud usage
- B. Performing protocol conversion to send data directly to cloud storage
- C. Creating object IDs before storing all objects in cloud storage
- D. Creating a flat file system to store block data in cloud storage
正解:B
質問 # 42
What is an accurate statement about an integrated NAS controller?
Response:
- A. Abstracts and pools NAS controllers across multiple NAS systems
- B. Contains a specialized operating system dedicated to file serving
- C. Contains an FC Forwarder that is optimized for file sharing functions
- D. Stripes data across multiple NAS systems for data protection
正解:B
質問 # 43
A company is interested in an architecture that provides multitenancy. In addition, they want to lower CAPEX and OPEX for acquiring and managing an end-user computing infrastructure. Which recommended cloud service will meet these requirements?
Response:
- A. Database as a Service
- B. Storage as a Service
- C. Desktop as a Service
- D. Network as a Service
正解:C
質問 # 44
What provides users with self-service access to pre-defined storage services?
Response:
- A. Storage controller
- B. Control plane
- C. Service catalog
- D. Service discovery
正解:C
質問 # 45
What statement describes machine learning?
- A. Replicating a detailed process and then implementing it in software
- B. Developing a program to compute every possible outcome
- C. Organizes data efficiently so that compute systems can learn
- D. Applies an algorithm to large amounts of data for pattern discovery
正解:D
解説:
Explanation
Machine learning is a subfield of artificial intelligence that gives computers the ability to learn without explicitly being programmed [1]. It does this by applying an algorithm to large amounts of data in order to discover patterns and insights that can be used to inform decisions and predictions. This allows machines to learn from experience and make decisions in a way that mimics the human brain.
質問 # 46
What keeps the name server up-to-date on all switches in a fabric?
Response:
- A. Management server
- B. SW-RSCN
- C. Zoning
- D. FLOGI
正解:B
質問 # 47
Which loT architecture component provides the connection to monitor and control user devices? (First Choose Correct option and give detailed explanation delltechnologies.com)
- A. Middleware
- B. Gateways
- C. Applications
- D. Smart Devices
正解:B
解説:
Explanation
Gateways are an essential component of an IoT architecture, providing the connection between user devices and the network. Gateways act as a bridge between the device layer and the cloud layer, enabling the remote monitoring and control of user devices. Gateways also provide security features such as data encryption and authentication, which helps protect user data. Additionally, gateways provide additional features, such as data aggregation and protocol conversion, which can help increase the efficiency of the overall IoT architecture.
質問 # 48
What is compromised by a passive attack on an IT infrastructure?
Response:
- A. Availability
- B. Confidentiality
- C. Integrity
- D. Repudiation
正解:B
質問 # 49
Which Dell EMC product is designed to host both file and object data?
- A. PowerVault
- B. PowerScale
- C. Cloud Tiering Appliance
- D. PowerEdge
正解:B
質問 # 50
Match the Fibre Channel (FC) layers with their respective features.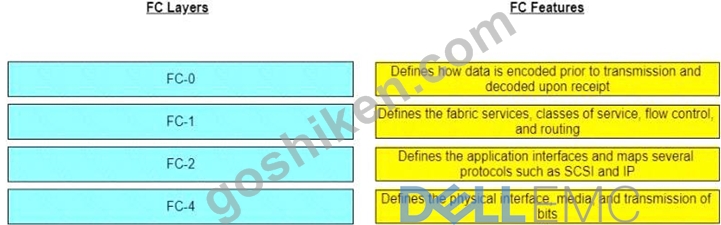
正解:
解説: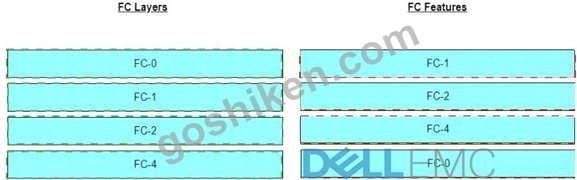
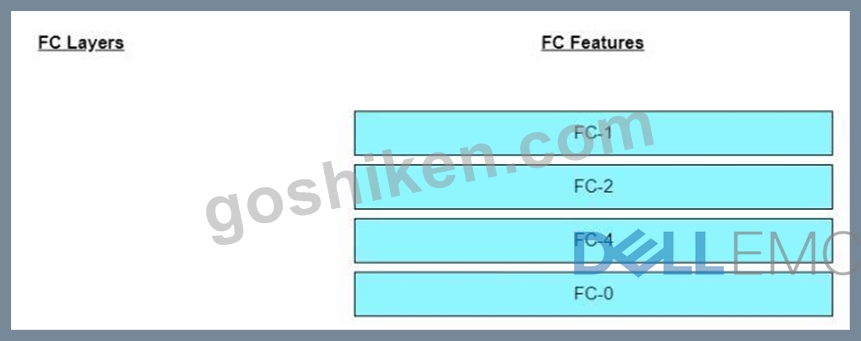
質問 # 51
What is a characteristic of an FC-AL implementation?
Response:
- A. Reserves one address for connecting an FC-SW port
- B. Requires at least one connectivity device
- C. Supports connectivity up to 15 million nodes
- D. Devices can be added and removed dynamically without any impact
正解:A
質問 # 52
What is an accurate statement about a denial-of-service attack?
Response:
- A. Prevents legitimate users from accessing resources or services
- B. Gaining unauthorized access to a user's accounts and data
- C. Captures a user's credentials and then sends to the attacker
- D. Intentional misuse of privileges to compromise data security
正解:A
質問 # 53
A company is using an intrusion detection and prevention system (IDPS) to scan and analyze intrusion events.
Which IDPS technique uses a database that contains known attack patterns?
- A. Signature-based
- B. Policy-based
- C. Intrusion-based
- D. Anomaly. based
正解:D
質問 # 54
What is an advantage of implementing email archiving?
- A. Reduce the cost of managing the email archiving server and storage
- B. Increase the mailbox space by moving old emails to archive storage
- C. Provide high availability and continuous access to business emails
- D. Reduce redundant emails in a mailbox to facilitate faster recovery
正解:B
質問 # 55
DRAG DROP
If the client requests authorization from the resource owner, what are the remaining sequence of steps to authenticate a user using OAuth control?
正解:
解説:
The client requests an access token by authenticating with the authorization server and presenting the authorization grant.
The authorization server authenticates the client and validates the authorization grant, and if valid, issues an access token.
The client requests the protected resource from the resource server and authenticates by presenting the access token.
The resource server validates the access token, and if valid, serves the request
質問 # 56
Which data archiving component scans primary storage to find the files that meet the archiving policy?
- A. Archive database server
- B. Archive agent
- C. Archive storage
- D. Archive stub file
正解:B
質問 # 57
......
全問DEA-1TT5問題集とAssociate - Information Storage and Management Examトレーニングコース:https://www.goshiken.com/EMC/DEA-1TT5-mondaishu.html
無料テストエンジンAssociate - Information Storage and Management Exam認定試験:https://drive.google.com/open?id=17uHlAzuBg1n8r193QBPFRSHhba0MN3w6
