2022年02月実際に出るPCNSE試験問題集には正確で更新された問題
PCNSE試験問題集でPDF問題とテストエンジン
Palo Alto Networks PCNSE 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
| トピック 7 |
|
| トピック 8 |
|
| トピック 9 |
|
| トピック 10 |
|
| トピック 11 |
|
質問 228
Which method will dynamically register tags on the Palo Alto Networks NGFW?
- A. Restful API or the VMWare API on the firewall or on the User-ID agent or the read-only domain controller (RODC)
- B. XML API or the VM Monitoring agent on the NGFW or on the User-ID agent
- C. Restful API or the VMware API on the firewall or on the User-ID agent
- D. XML-API or the VMware API on the firewall or on the User-ID agent or the CLI
正解: C
解説:
Reference:
https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/policy/register-ip-addresses-and-tags-dynam
https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-admin/policy/monitor-changes-in-the-virtual-environment/
質問 229
A customer has an application that is being identified as unknown-top for one of their custom PostgreSQL database connections. Which two configuration options can be used to correctly categorize their custom database application? (Choose two.)
- A. Custom application.
- B. Custom Service object.
- C. Security policy to identify the custom application.
- D. Application Override policy.
正解: A,D
解説:
Explanation
Unlike the App-ID engine, which inspects application packet contents for unique signature elements, the Application Override policy's matching conditions are limited to header-based data only. Traffic matched by an Application Override policy is identified by the App-ID entered in the Application entry box.Choices are limited to applications currently in the App-ID database.Because this traffic bypasses all Layer 7 inspection, the resulting security is that of a Layer-4 firewall. Thus, this traffic should be trusted without the need for Content-ID inspection. The resulting application assignment can be used in other firewall functions such as Security policy and QoS.Use CasesThree primary uses cases for Application Override Policy are:
To identify "Unknown" App-IDs with a different or custom application signature To re-identify an existing application signature To bypass the Signature Match Engine (within the SP3 architecture) to improve processing timesA discussion of typical uses of application override and specific implementation examples is here:https://live.paloaltonetworks.com/t5/Learning-Articles/Tips-amp-Tricks-How-to-Create-an-Application- Ov
質問 230
Refer to the exhibit.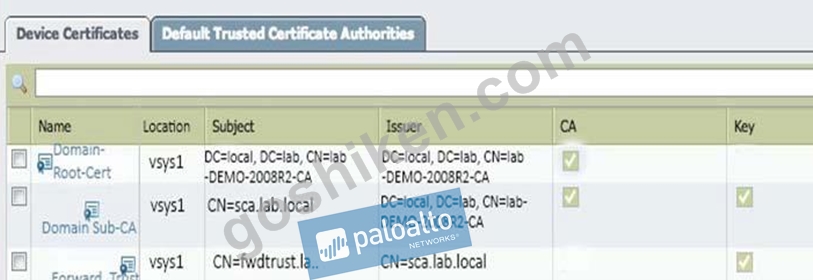
Which certificates can be used as a Forward Trust certificate?
- A. Domain Sub-CA
- B. Domain-Root-Cert
- C. Certificate from Default Trust Certificate Authorities
- D. Forward_Trust
正解: C
質問 231
Refer to exhibit. An organization has Palo Alto Networks NGFWs that send logs to remote monitoring and security management platforms. The network team has reported excessive traffic on the corporate WAN.
How could the Palo Alto Networks NGFW administrator reduce WAN traffic while maintaining support for all existing monitoring platforms?
- A. Any configuration on an M-500 would address the insufficient bandwidth concerns.
- B. Forward logs from external sources to Panorama for correlation, and from Panorama send them to the NGFW.
- C. Forward logs from firewalls only to Panorama and have Panorama forward logs to other external services.
- D. Configure log compression and optimization features on all remote firewalls.
正解: D
質問 232
VPN traffic intended for an administrator's Palo Alto Networks NGFW is being maliciously intercepted and retransmitted by the interceptor.
When creating a VPN tunnel, which protection profile can be enabled to prevent this malicious behavior?
- A. Replay
- B. Zone Protection
- C. DoS Protection
- D. Web Application
正解: A
解説:
https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/vpns/set-up-site-to-site- vpn/set-up-an-ipsec-tunnel
質問 233
Which DoS protection mechanism detects and prevents session exhaustion attacks?
- A. Packet Based Attack Protection
- B. TCP Port Scan Protection
- C. Flood Protection
- D. Resource Protection
正解: D
解説:
Explanation/Reference:
Reference: https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/policy/dos-protection- profiles
質問 234
A company is upgrading its existing Palo Alto Networks firewall from version 7.0.1 to 7.0.4.
Which three methods can the firewall administrator use to install PAN-OS 7.0.4 across the enterprise?( Choose three)
- A. Push the PAN-OS 7.0.4 updates from the support site to install on each firewall.
- B. Download and push PAN-OS 7.0.4 from Panorama to each firewall.
- C. Download PAN-OS 7.0.4 files from the support site and install them on each firewall after manually uploading.
- D. Download and install PAN-OS 7.0.4 directly on each firewall.
- E. Download PAN-OS 7.0.4 to a USB drive and the firewall will automatically update after the USB drive is inserted in the firewall.
- F. Push the PAN-OS 7.0.4 update from one firewall to all of the other remaining after updating one firewall.
正解: B,C,D
質問 235
Which three types of software will receive a Grayware verdict from WildFire? (Choose Three)
- A. Potentially unwanted programs
- B. Trojans
- C. Browser Toolbar
- D. Ransomeware
- E. Adware.
正解: A,C,E
解説:
https://www.paloaltonetworks.com/documentation/translated/70/newfeaturesguide/wildfire- features/wildfire-grayware-verdict
質問 236
An Administrator is configuring an IPSec VPN toa Cisco ASA at the administrator's home and experiencing issues completing the connection. The following is th output from the command:
less mp-log ikemgr.log: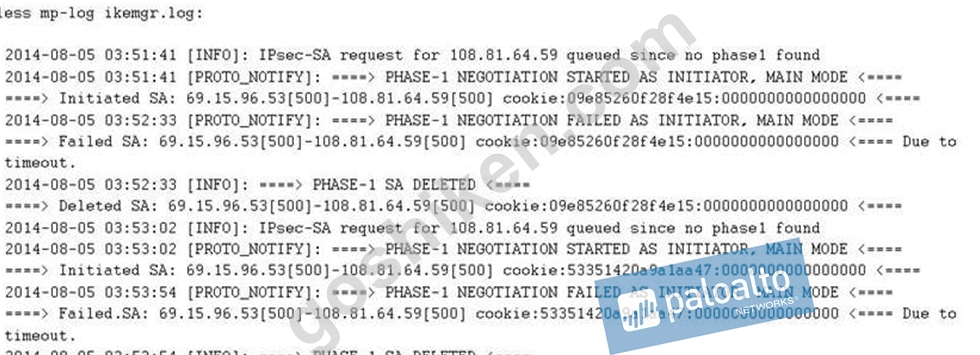
What could be the cause of this problem?
- A. The public IP addresse do not match for both the Palo Alto Networks Firewall and the ASA.
- B. The shared secerts do not match between the Palo Alto firewall and the ASA
- C. The Proxy IDs on the Palo Alto Networks Firewall do not match the settings on the ASA.
- D. The deed peer detection settings do not match between the Palo Alto Networks Firewall and the ASA
正解: C
質問 237
Which two settings can be configured only locally on the firewall and not pushed from a Panorama
template or template stack? (Choose two.)
- A. Network Interface Type
- B. HA1 IP Address
- C. Zone Protection Profile
- D. Master Key
正解: B,D
質問 238
If an administrator wants to decrypt SMTP traffic and possesses the server's certificate, which SSL decryption mode will allow the Palo Alto Networks NGFW to inspect traffic to the server?
- A. SMTP Inbound Decryption
- B. SSL Inbound Inspection
- C. TLS Bidirectional Inspection
- D. SSH Forward Proxy
正解: B
解説:
https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/decryption/configure-ssl- inbound-inspection
質問 239
If the firewall has the link monitoring configuration, what will cause a failover?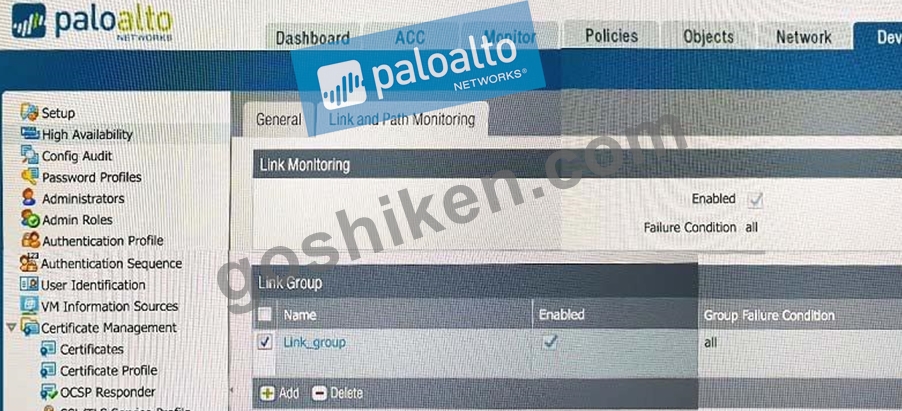
- A. ethernet1/3 or Ethernet1/6 going down
- B. ethernet1/6 going down
- C. ethernet1/3 and ethernet1/6 going down
- D. ethernet1/3 going down
正解: C
質問 240
A firewall should be advertising the static route 10 2 0 0/24 into OSPF The configuration on the neighbor is correct but the route is not in the neighbor's routing table Which two configurations should you check on the firewall'? (Choose two )
- A. In the OSFP configuration ensure that the correct redistribution profile is selected in the OSPF Export Rules section
- B. Within the redistribution profile ensure that Redist is selected
- C. In the redistribution profile check that the source type is set to "ospf"
- D. Ensure that the OSPF neighbor state is "2-Way"
正解: A,B
質問 241
A users traffic traversing a Palo Alto networks NGFW sometimes can reach http //www company com At other times the session times out. At other times the session times out The NGFW has been configured with a PBF rule that the user traffic matches when it goes to http://www.company.com goes to http://www company com How can the firewall be configured to automatically disable the PBF rule if the next hop goes down?
- A. Create and add a monitor profile with an action of wait recover in the PBF rule in question
- B. Configure path monitoring for the next hop gateway on the default route in the virtual router
- C. Create and add a monitor profile with an action of fail over in the PBF rule in question
- D. Enable and configure a link monitoring profile for the external interface of the firewall
正解: B
質問 242
How does an administrator schedule an Applications and Threats dynamic update while delaying installation of the update for a certain amount of time?
- A. Configure the option for "Threshold".
- B. Disable automatic updates during weekdays.
- C. Automatically "download only" and then install Applications and Threats later, after the administrator approves the update.
- D. Automatically "download and install" but with the "disable new applications" option used.
正解: C
解説:
Explanation
質問 243
Which CLI command enables an administrator to check the CPU utilization of the dataplane?
- A. show running resource-monitor
- B. debug running resources
- C. show system resources
- D. debug data-plane dp-cpu
正解: A
質問 244
If a template stack is assigned to a device and the stack includes three templates with overlapping settings, which settings are published to the device when the template stack is pushed?
- A. All the settings configured in all templates.
- B. The administrator will be promoted to choose the settings for that chosen firewall.
- C. The settings assigned to the template that is on top of the stack.
- D. Depending on the firewall location, Panorama decides with settings to send.
正解: B
解説:
Reference:
https://www.paloaltonetworks.com/documentation/80/panorama/panorama_adminguide/manage-firewalls/manage-templates-and-template-stacks/configure-a-template-stack
質問 245
Refer to Exhibit. A firewall has three PBF rules and a default route with a next hop of 172.20.10.1 that is configured in the default VR. A user named Will has a PC with a 192.168.10.10 IP address.
He makes an HTTPS connection to 172.16.10.20.
Which is the next hop IP address for the HTTPS traffic from Will's PC?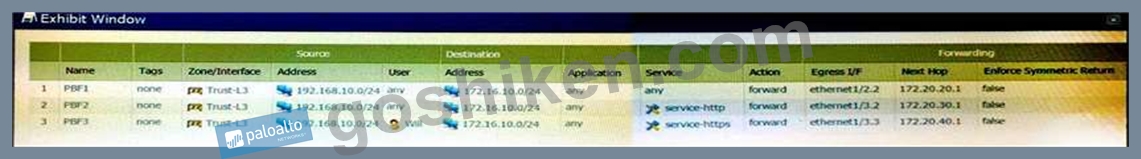
- A. 172.20.30.1
- B. 172.20.10.1
- C. 172.20.20.1
- D. 172.20.40.1
正解: C
質問 246
Which DoS protection mechanism detects and prevents session exhaustion attacks?
- A. Packet Based Attack Protection
- B. TCP Port Scan Protection
- C. Flood Protection
- D. Resource Protection
正解: D
質問 247
An administrator deploys PA-500 NGFWs as an active/passive high availability pair. The devices are not participating in dynamic routing, and preemption is disabled.
What must be verified to upgrade the firewalls to the most recent version of PAN-OS software?
- A. User-ID agent.
- B. WildFire update package.
- C. Applications and Threats update package.
- D. Antivirus update package.
正解: C
解説:
Explanation/Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/newfeaturesguide/upgrade-to-pan-os-
80/upgrade-the-firewall-to-pan-os-80/upgrade-an-ha-firewall-pair-to-pan-os-80
質問 248
......
合格させるPalo Alto Networks PCNSE試験最速合格にはGoShiken:https://www.goshiken.com/Palo-Alto-Networks/PCNSE-mondaishu.html
PCNSE問題集で必ず試験合格させる:https://drive.google.com/open?id=1ce7TdI6ASs9iAHlLOOL5tpYv3XvfcHjw
