Palo Alto Networks PCNSE日常練習試験は2022年最新のに更新された394問あります
有効問題を試そう!PCNSE試験で実際の試験問題と解答
Palo Alto Networks PCNSE 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
| トピック 7 |
|
質問 190
An administrator needs to upgrade a Palo Alto Networks NGFW to the most current version of PAN-OS® software. The firewall has internet connectivity through an Ethernet interface, but no internet connectivity from the management interface. The Security policy has the default security rules and a rule that allows all web-browsing traffic from any to any zone. What must the administrator configure so that the PAN-OS® software can be upgraded?
- A. CRL
- B. Security policy rule
- C. Scheduler
- D. Service route
正解: B
質問 191
Which two benefits come from assigning a Decryption Profile to a Decryption policy rule with a "No Decrypt" action? (Choose two.)
- A. Block sessions with expired certificates
- B. Block sessions with client authentication
- C. Block sessions with unsupported cipher suites
- D. Block sessions with untrusted issuers
- E. Block credential phishing
正解: A,B,C
解説:
Reference: https://www.paloaltonetworks.com/documentation/71/pan-os/pan- os/decryption/create-a-decryption-profile
質問 192
YouTube videos are consuming too much bandwidth on the network, causing delays in mission-critical traffic.
The administrator wants to throttle YouTube traffic. The following interfaces and zones are in use on the firewall:
* ethernet1/1, Zone: Untrust (Internet-facing)
* ethernet1/2, Zone: Trust (client-facing)
A QoS profile has been created, and QoS has been enabled on both interfaces. A QoS rule exists to put the YouTube application into QoS class 6. Interface Ethernet1/1 has a QoS profile called Outbound, and interface Ethernet1/2 has a QoS profile called Inbound.
Which setting for class 6 with throttle YouTube traffic?
- A. Outbound profile with Guaranteed Ingress
- B. Inbound profile with Guaranteed Egress
- C. Inbound profile with Maximum Egress
- D. Outbound profile with Maximum Ingress
正解: C
質問 193
Refer to the exhibit. An administrator is using DNAT to map two servers to a single public IP address. Traffic will be steered to the specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and HOST B (10.1.1.101) receives SSH traffic.)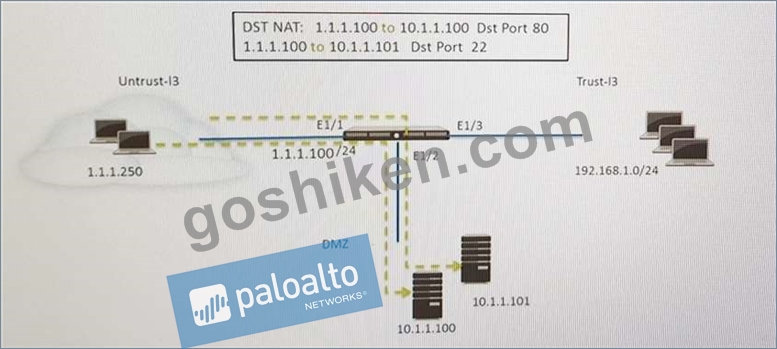
Which two security policy rules will accomplish this configuration? (Choose two.)
- A. Untrust (Any) to Untrust (10.1.1.1), ssh -Allow
- B. Untrust (Any) to Untrust (10.1.1.1), web-browsing -Allow
- C. Untrust (Any) to DMZ (10.1.1.100.10.1.1.101), ssh, web-browsing -Allow
- D. Untrust (Any) to DMZ (10.1.1.1), web-browsing -Allow
- E. Untrust (Any) to DMZ (10.1.1.1), ssh -Allow
正解: D,E
質問 194
Exhibit: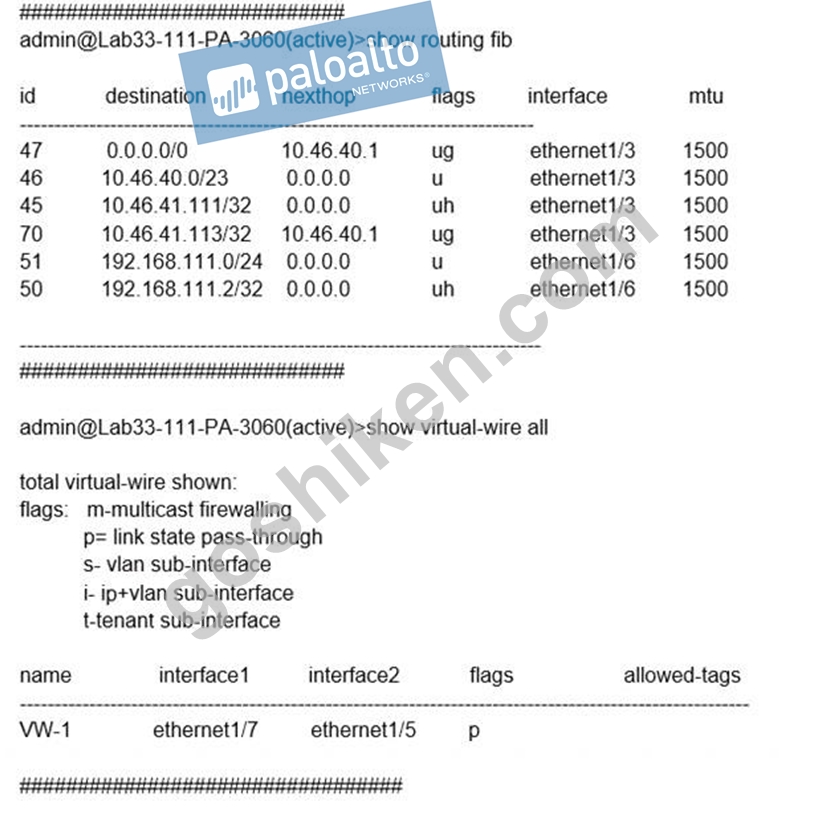
What will be the egress interface if the traffic's ingress interface is ethernet1/6 sourcing from 192.168.111.3 and to the destination 10.46.41.113 during the time shown in the image?
- A. ethernet1/3
- B. ethernet1/6
- C. ethernet1/5
- D. ethernet1/7
正解: A
質問 195
A session in the Traffic log is reporting the application as "incomplete." What does "incomplete" mean?
- A. The traffic is coming across UDP, and the application could not be identified.
- B. The three-way TCP handshake was observed, but the application could not be identified.
- C. The three-way TCP handshake did not complete.
- D. Data was received but was instantly discarded because of a Deny policy was applied before App-ID could be applied.
正解: A
質問 196
Which feature must you configure to prevent users form accidentally submitting their corporate credentials to a phishing website?
- A. Anti-Spyware profile
- B. Zone Protection profile
- C. Vulnerability Protection profile
- D. URL Filtering profile
正解: D
解説:
Explanation/Reference:
Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/threat-prevention/prevent- credential-phishing
質問 197
Click the Exhibit button below,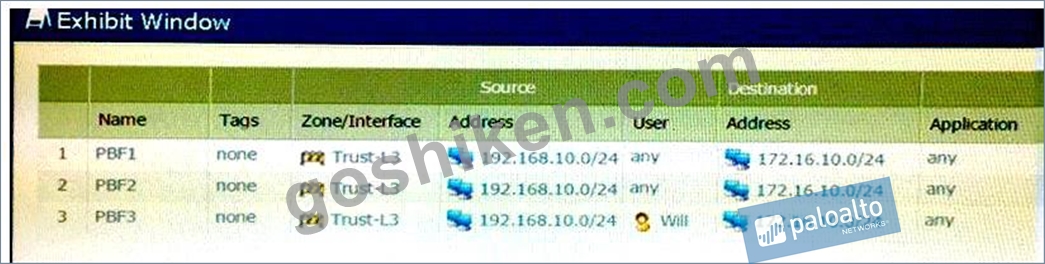
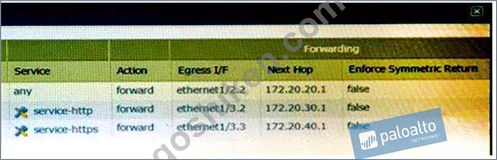
A firewall has three PBF rules and a default route with a next hop of 172.20.10.1 that is configured in the default VR. A user named Will has a PC with a 192.168.10.10 IP address. He makes an HTTPS connection to
172.16.10.20.
Which is the next hop IP address for the HTTPS traffic from Will's PC?
- A. 172.20.30.1
- B. 172.20.10.1
- C. 172.20.20.1
- D. 172.20.40.1
正解: C
質問 198
When using the predefined default profile, the policy will inspect for viruses on the decoders. Match each decoder with its default action.
Answer options may be used more than once or not at all.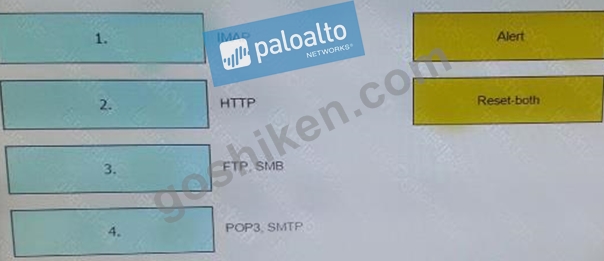
正解:
解説: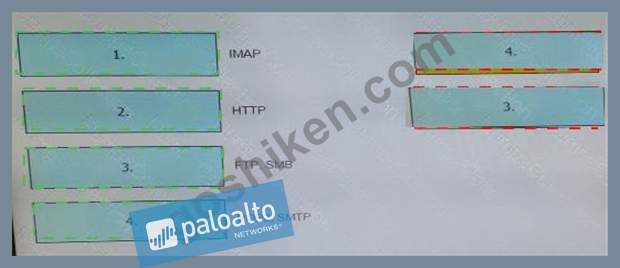
Explanation
IMAP , POP3 , SMTP - > Alert
HTTP,FTP,SMB -> Reset-both
質問 199
A Security policy rule is configured with a Vulnerability Protection Profile and an action of `Deny".
Which action will this cause configuration on the matched traffic?
- A. The configuration will allow the matched session unless a vulnerability is detected. The "Deny" action will supersede the per-severity defined actions defined in the associated Vulnerability Protection Profile.
- B. The configuration is invalid. It will cause the firewall to skip this Security policy rule. A warning will be displayed during a commit.
- C. The configuration is invalid. The Profile Settings section will be grayed out when the Action is set to "Deny".
- D. The configuration is valid. It will cause the firewall to deny the matched sessions. Any configured Security Profiles have no effect if the Security policy rule action is set to "Deny."
正解: D
解説:
"Security profiles are not used in the match criteria of a traffic flow. The security profile is applied to scan traffic after the application or category is allowed by the security policy."
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/policy/security-profiles.html#
質問 200
Which User-ID method maps IP addresses to usernames for users connecting through an 802.1x-enabled wireless network device that has no native integration with PAN-OS® software?
- A. XML API
- B. Client Probing
- C. Port Mapping
- D. Server Monitoring
正解: A
解説:
https://docs.paloaltonetworks.com/pan-os/10-0/pan-os-admin/user-id/user-id-concepts/user-mapping/xml-api.html
質問 201
A customer wants to set up a VLAN interface for a Layer 2 Ethernet port.
Which two mandatory options are used to configure a VLAN interface? (Choose two.)
- A. Virtual router
- B. ARP entries
- C. Netflow Profile
- D. Security zone
正解: A,D
解説:
Reference:
https://www.paloaltonetworks.com/documentation/80/pan-os/web-interface-help/network/network-interfaces/pa- layer-2-interface#idd2bcaacc-54b9-4ec9-a1dd-8064499f5b9d
質問 202
In a Panorama template which three types of objects are configurable? (Choose three)
- A. interface management profiles
- B. security profiles
- C. QoS profiles
- D. HIP objects
- E. certificate profiles
正解: A,C,E
質問 203
Refer to the exhibit.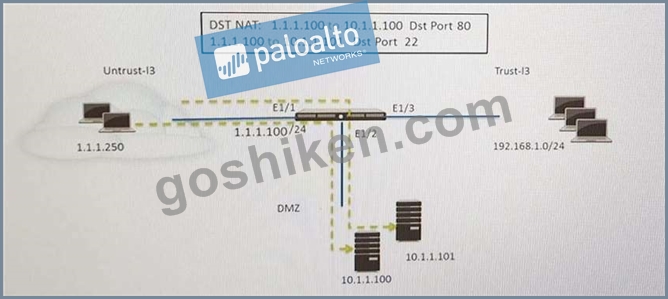
An administrator is using DNAT to map two servers to a single public IP address. Traffic will be steered to the specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and HOST B (10.1.1.101) receives SSH traffic.) Which two security policy rules will accomplish this configuration? (Choose two.)
- A. Untrust (Any) to Untrust (10.1.1.1), ssh -Allow
- B. Untrust (Any) to Untrust (10.1.1.1), web-browsing -Allow
- C. Untrust (Any) to DMZ (10.1.1.100.10.1.1.101), ssh, web-browsing -Allow
- D. Untrust (Any) to DMZ (10.1.1.1), web-browsing -Allow
- E. Untrust (Any) to DMZ (10.1.1.1), ssh -Allow
正解: D,E
質問 204
A customer wants to combine multiple Ethernet interfaces into a single virtual interface using link aggregation.
Which two formats are correct for naming aggregate interfaces? (Choose two.)
- A. aggregate.1
- B. ae.8
- C. ae.1
- D. aggregate.8
正解: B,C
質問 205
Which three file types can be forwarded to WildFire for analysis as a part of the basic WildFire service?
(Choose three.)
- A. .pdf
- B. .exe
- C. .fon
- D. .dll
- E. .apk
- F. .jar
正解: A,E,F
質問 206
Which CLI command can be used to export the tedium capture?
- A. download mgmt.-pcap
- B. scp extract mgmt-pcap from mgmt.pcap to <username@host:path>
- C. scp export mgmt-pcap from mgmt.pcap to <username@host:path>
- D. scp export tcpdump from mgmt.pcap to <username@host:path>
正解: C
解説:
Reference:
https://live.paloaltonetworks.com/t5/Management-Articles/How-To-Packet-Capture-tcpdump-On-Management-I p/55415
質問 207
Which two virtualization platforms officially support the deployment of Palo Alto Networks VM-Series firewalls? (Choose two.)
- A. Kernel Virtualization Module (KVM)
- B. Microsoft Hyper-V
- C. Red Hat Enterprise Virtualization (RHEV)
- D. Boot Strap Virtualization Module (BSVM)
正解: A,B
解説:
Reference:
https://www.paloaltonetworks.com/products/secure-the-network/virtualized-next-generation-firewall/vm-series docs.paloaltonetworks.com/vm-series/8-0/vm-series-deployment/about-the-vm-series-firewall/vm-series-deploym
質問 208
If an administrator does not possess a website's certificate, which SSL decryption mode will allow the Palo Alto networks NGFW to inspect when users browse to HTTP(S) websites?
- A. SSL Outbound Inspection
- B. TLS Bidirectional proxy
- C. SSL Inbound Inspection
- D. SSL Forward Proxy
正解: D
解説:
Explanation
Explanation
質問 209
In a security-first network what is the recommended threshold value for content updates to be dynamically updated?
- A. 6 to 12 hours
- B. 36 hours
- C. 1 to 4 hours
- D. 24 hours
正解: A
解説:
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/threat-prevention/best-practices-for-content-and-threat-content-updates/best-practices-security-first.html
質問 210
If the firewall is configured for credential phishing prevention using the "Domain Credential Filter" method,
which login will be detected as credential theft?
- A. First four letters of the username matching any valid corporate username.
- B. Matching any valid corporate username.
- C. Mapping to the IP address of the logged-in user.
- D. Using the same user's corporate username and password.
正解: C
解説:
Explanation/Reference:
Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/newfeaturesguide/content-
inspection-features/credential-phishing-prevention
質問 211
The web server is configured to listen for HTTP traffic on port 8080. The clients access the web server using the IP address 1.1.1.100 on TCP Port 80. The destination NAT rule is configured to translate both IP address and report to 10.1.1.100 on TCP Port 8080.
Which NAT and security rules must be configured on the firewall? (Choose two)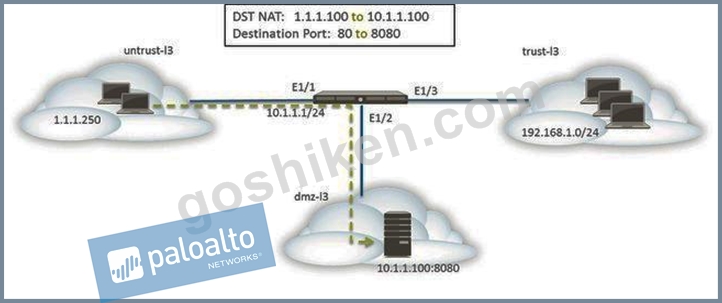
- A. A NAT rule with a source of any from untrust-I3 zone to a destination of 10.1.1.100 in dmz-zone using service-http service.
- B. A NAT rule with a source of any from untrust-I3 zone to a destination of 1.1.1.100 in untrust-I3 zone using service-http service.
- C. A security policy with a source of any from untrust-I3 zone to a destination of 1.1.100 in dmz-I3 zone using web-browsing application.
- D. A security policy with a source of any from untrust-I3 Zone to a destination of 10.1.1.100 in dmz- I3 zone using web-browsing application
正解: B,C
質問 212
What is a key step in implementing WildFire best practices?
- A. Configure the firewall to retrieve content updates every minute
- B. In a security-first network set the WildFire size limits to the minimum value
- C. In a mission-critical network, increase the WildFire size limits to the maximum value
- D. Ensure that a Threat Prevention subscription is active
正解: D
質問 213
Which virtual router feature determines if a specific destination IP address is reachable?
- A. Path Monitoring
- B. Ping-Path
- C. Heartbeat Monitoring
- D. Failover
正解: A
質問 214
......
テストエンジンに練習PCNSEテスト問題:https://www.goshiken.com/Palo-Alto-Networks/PCNSE-mondaishu.html
PCNSEリアル試験問題でテストエンジン問題集トレーニングには394問あります:https://drive.google.com/open?id=1ce7TdI6ASs9iAHlLOOL5tpYv3XvfcHjw
