PCNSE練習試験と学習ガイドは厳密検証されたGoShiken最新な211問題
2023年最新のな厳密検証された合格させるPCNSE学習ガイドベズトお試しセット
質問 118
An administrator creates a custom application containing Layer 7 signatures. The latest application and
threat dynamic update is downloaded to the same NGFW. The update contains an application that
matches the same traffic signatures as the custom application.
Which application should be used to identify traffic traversing the NGFW?
- A. Custom and downloaded application signature files are merged and both are used
- B. Downloaded application
- C. Custom application
- D. System logs show an application error and neither signature is used.
正解: C
質問 119
Which GlobalProtect component must be configured to enable Chentless VPN?
- A. GlobalProtect portal
- B. GlobalProtect satellite
- C. GlobalProtect gateway
- D. GlobalProtect app
正解: A
解説:
Creating the GlobalProtect portal is as simple as letting it know if you have accessed it already. A new gateway for accessing the GlobalProtect portal will appear. Client authentication can be used with an existing one.
https://www.nstec.com/how-to-configure-clientless-vpn-in-palo-alto/#5
質問 120
Which three function are found on the dataplane of a PA-5050? (Choose three)
- A. Signature Match
- B. Management
- C. Protocol Decoder
- D. Network Processing
- E. Dynamic routing
正解: A,D,E
解説:
In these devices, dataplane zero, or dp0 for short, functions as the master dataplane and determines which dataplane will be used as the session owner that is responsible for processing and inspection.
The data plane provides all data processing and security detection and enforcement, including:
* (B) All networking connectivity, packet forwarding, switching, routing, and network address translation
* Application identification, using the content of the applications, not just port or protocol
* SSL forward proxy, including decryption and re-encryption
* Policy lookups to determine what security policy to enforce and what actions to take, including scanning for threats, logging, and packet marking
* Application decoding, threat scanning for all types of threats and threat prevention
* Logging, with all logs sent to the control plane for processing and storage E: The following diagram depicts both the hardware and software architecture of the next- generation firewall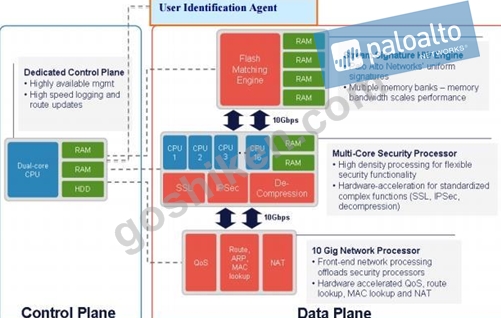
Incorrect Answers:
C: Management is done in the control plane.
https://www.niap-ccevs.org/st/st_vid10392-st.pdf
質問 121
Which three fields can be included in a pcap filter? (Choose three)
- A. Rule number
- B. Destination IP
- C. Source IP
- D. Ingress interface
- E. Egress interface
正解: A,B,C
解説:
Explanation
(https://live.paloaltonetworks.com/t5/Featured-Articles/Getting-Started-Packet-Capture/ta-p/72069)
質問 122
When you import the configuration of an HA pair into Panorama, how do you prevent the import from affecting ongoing traffic?
- A. Disable HA
- B. Set the passive link state to 'shutdown.-
- C. Disable config sync
- D. Disable the HA2 link
正解: C
解説:
https://docs.paloaltonetworks.com/panorama/10-1/panorama-admin/manage-firewalls/transition- a-firewall-to-panorama-management/migrate-a-firewall-ha-pair-to-panorama-management.html Step 2 is "Disable configuration synchronization between the HA peers."
質問 123
Which action disables Zero Touch Provisioning (ZTP) functionality on a ZTP firewall during the onboarding process?
- A. removing the firewall as a managed device in Panorama
- B. performing a factory reset of the firewall
- C. removing the Panorama serial number from the ZTP service
- D. performing a local firewall commit
正解: D
解説:
Explanation
Performing a local commit on the ZTP firewall disables ZTP functionality and results in the failure to successfully add the firewall to Panorama.
https://docs.paloaltonetworks.com/panorama/10-0/panorama-admin/manage-firewalls/set-up- zero-touch-provisioning/add-ztp-firewalls-to-panorama/add-a-ztp-firewall-to- panorama.html#id182211ac-a31c-4122-a11f-19450ec9ca4e
質問 124
An administrator has configured a pair of firewalls using high availability in Active/Passive mode. Link and Path Monitoring Is enabled with the Failure Condition set to "any." There is one link group configured containing member interfaces ethernet1/1 and ethernet1/2 with a Group Failure Condition set to "all." Which HA state will the Active firewall go into if ethernet1/1 link goes down due to a failure?
- A. Non-functional
- B. Active-Secondary
- C. Passive
- D. Active
正解: D
質問 125
A customer has an application that is being identified as unknown-top for one of their custom PostgreSQL database connections. Which two configuration options can be used to correctly categorize their custom database application? (Choose two.)
- A. Security policy to identify the custom application.
- B. Application Override policy.
- C. Custom application.
- D. Custom Service object.
正解: B,C
解説:
Explanation
Unlike the App-ID engine, which inspects application packet contents for unique signature elements, the Application Override policy's matching conditions are limited to header-based data only. Traffic matched by an Application Override policy is identified by the App-ID entered in the Application entry box.Choices are limited to applications currently in the App-ID database.Because this traffic bypasses all Layer 7 inspection, the resulting security is that of a Layer-4 firewall. Thus, this traffic should be trusted without the need for Content-ID inspection. The resulting application assignment can be used in other firewall functions such as Security policy and QoS.Use CasesThree primary uses cases for Application Override Policy are:
To identify "Unknown" App-IDs with a different or custom application signature To re-identify an existing application signature To bypass the Signature Match Engine (within the SP3 architecture) to improve processing timesA discussion of typical uses of application override and specific implementation examples is here:https://live.paloaltonetworks.com/t5/Learning-Articles/Tips-amp-Tricks-How-to-Create-an-Application- Ov
質問 126
Which option would an administrator choose to define the certificate and protocol that Panorama and its
managed devices use for SSL/TLS services?
- A. Configure an SSL/TLS Profile.
- B. Configure a Decryption Profile and select SSL/TLS services.
- C. Set up Security policy rule to allow SSL communication.
- D. Set up SSL/TLS under Polices > Service/URL Category>Service.
正解: A
解説:
Explanation/Reference:
Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/web-interface-help/device/device-
certificate-management-ssltls-service-profile
質問 127
An administrator needs to implement an NGFW between their DMZ and Core network. EIGRP Routing between the two environments is required. Which interface type would support this business requirement?
- A. Tunnel interfaces to terminate EIGRP routing on an IPsec tunnel (with the GlobalProtect License to support LSVPN and EIGRP protocols)
- B. Layer 3 interfaces, but configuring EIGRP on the attached virtual router
- C. Layer 3 or Aggregate Ethernet interfaces, but configuring EIGRP on subinterfaces only
- D. Virtual Wire interfaces to permit EIGRP routing to remain between the Core and DMZ
正解: C
質問 128
An Administrator is configuring an IPSec VPN toa Cisco ASA at the administrator's home and experiencing issues completing the connection. The following is th output from the command:
less mp-log ikemgr.log: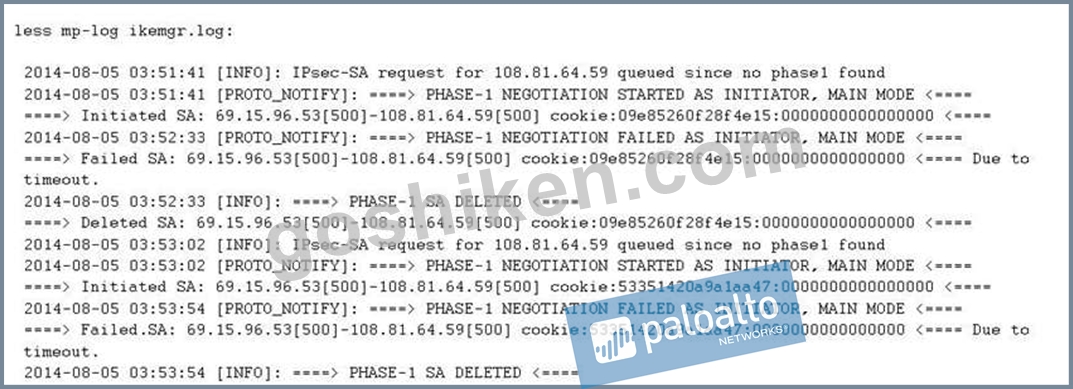
What could be the cause of this problem?
- A. The shared secerts do not match between the Palo Alto firewall and the ASA
- B. The public IP addresse do not match for both the Palo Alto Networks Firewall and the ASA.
- C. The Proxy IDs on the Palo Alto Networks Firewall do not match the settings on the ASA.
- D. The deed peer detection settings do not match between the Palo Alto Networks Firewall and the ASA
正解: C
質問 129
Which User-ID method should be configured to map IP addresses to usernames for users connected through a terminal server?
- A. client probing
- B. server monitoring
- C. XFF headers
- D. port mapping
正解: D
解説:
Reference: https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/user- id/configure-user-mapping-for-terminal-server- users
質問 130
Which User-ID method should be configured to map IP addresses to usernames for users connected
through a terminal server?
- A. client probing
- B. server monitoring
- C. XFF headers
- D. port mapping
正解: D
解説:
Explanation/Reference:
Reference: https://www.paloaltonetworks.com/documentation/71/pan-os/pan-os/user-id/configure-user-
mapping-for-terminal-server-users
質問 131
Refer to the exhibit.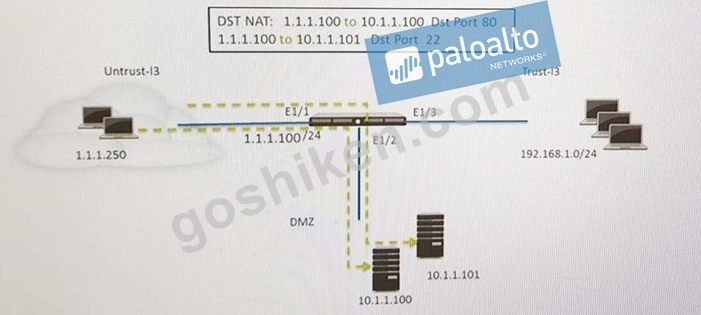
An administrator is using DNAT to map two servers to a single public IP address. Traffic will be steered to the specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and HOST B (10.1.1.101) receives SSH traffic.)
Which two security policy rules will accomplish this configuration? (Choose two.)
- A. Untrust (Any) to DMZ (1.1.1.100), SSH -Allow
- B. Untrust (Any) to DMZ (10.1.1.100.10.1.1.101), ssh, web-browsing -Allow
- C. Untrust (Any) to DMZ (1.1.1.100), web-browsing -Allow
- D. Untrust (Any) to Untrust (10.1.1.1), SSH -Allow
- E. Untrust (Any) to Untrust (10.1.1.1), web-browsing -Allow
正解: A,C
解説:
https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-admin/networking/nat/nat-configuration-examples/destination-nat-exampleone-to-many-mapping#
質問 132
What type of address object would be useful for internal devices where the addressing structure assigns meaning to certain bits in the address, as illustrated in the diagram?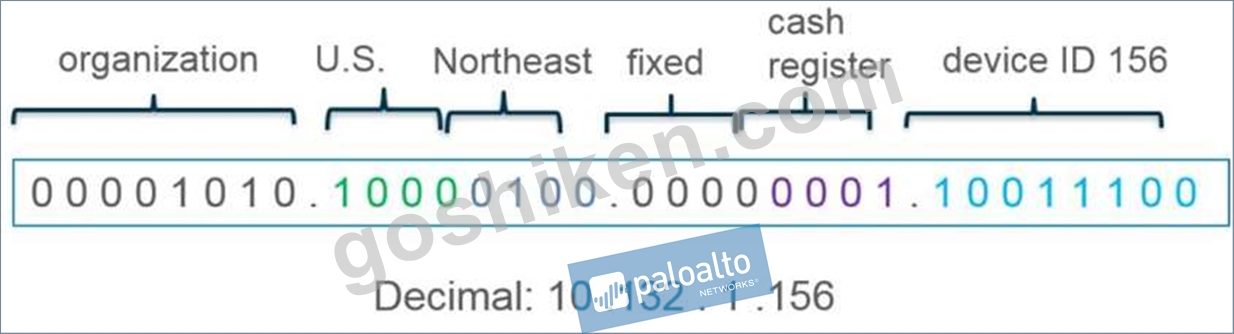
- A. IP Range
- B. IP Address
- C. IP Wildcard Mask
- D. IP Netmask
正解: C
解説:
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-new-features/networking-features/wildcard-address
質問 133
A client is concerned about resource exhaustion because of denial-of-service attacks against their DNS
servers.
Which option will protect the individual servers?
- A. Use the DNS App-ID with application-default.
- B. Apply an Anti-Spyware Profile with DNS sinkholing.
- C. Enable packet buffer protection on the Zone Protection Profile.
- D. Apply a classified DoS Protection Profile.
正解: C
質問 134
The company's Panorama server (IP 10.10.10.5) is not able to manage a firewall that was recently deployed. The firewall's dedicated management port is being used to connect to the management network.
Which two commands may be used to troubleshoot this issue from the CLI of the new firewall?
(Choose two)
- A. test panoramas-connect 10.10.10.5
- B. show panoramas-status
- C. topdump filter "host 10.10.10.5
- D. debug dataplane packet-diag set capture on
- E. show arp all I match 10.10.10.5
正解: B,C
質問 135
in a template you can configure which two objects? (Choose two.)
- A. IPsec tunnel
- B. application group
- C. Monitor profile
- D. SD WAN path quality profile
正解: A,D
質問 136
An administrator needs to determine why users on the trust zone cannot reach certain websites. The only information available is shown on the following image. Which configuration change should the administrator make?
A)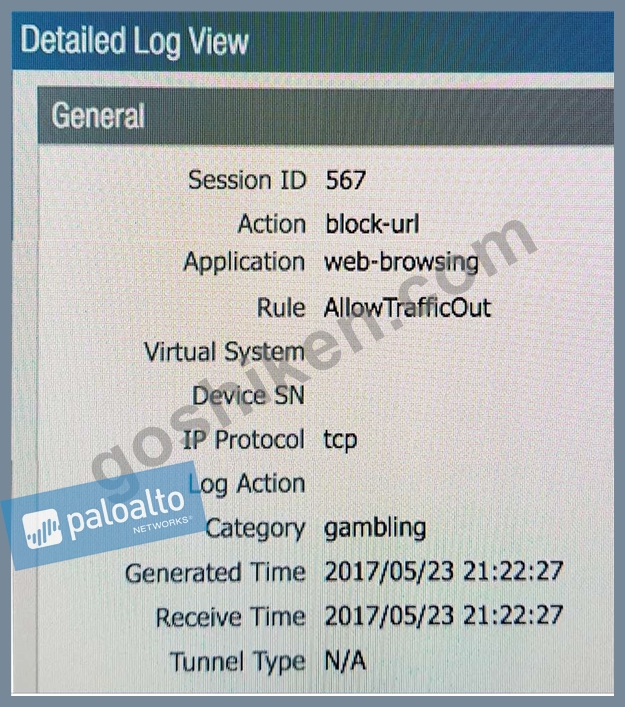
B)
C)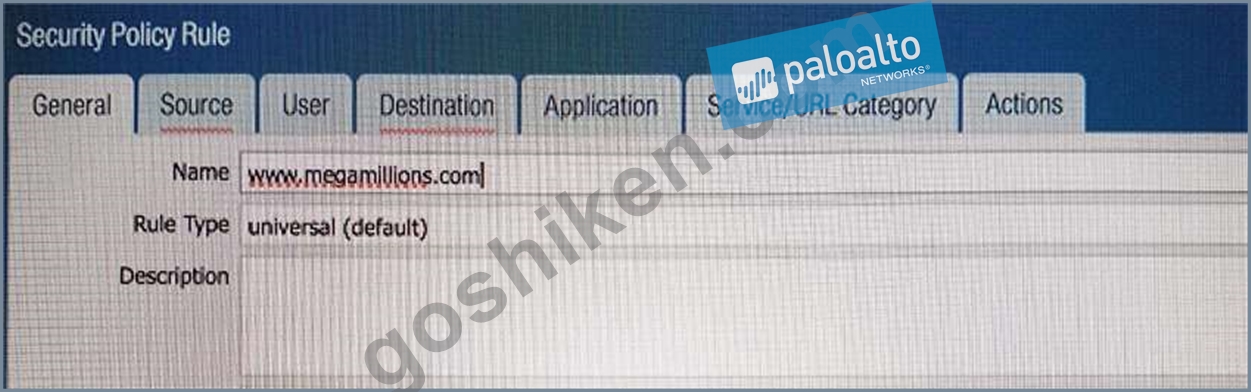
D)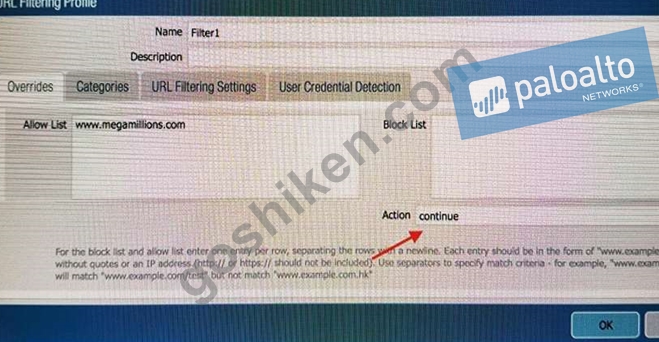
E)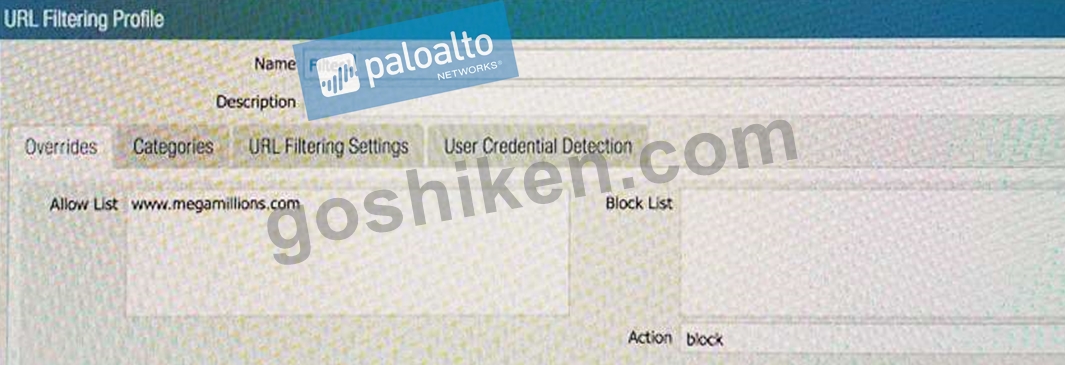
- A. Option C
- B. Option D
- C. Option B
- D. Option A
- E. Option E
正解: B
質問 137
Which three authentication services can administrator use to authenticate admins into the Palo Alto Networks NGFW without defining a corresponding admin account on the local firewall? (Choose three.)
- A. SAML
- B. PAP
- C. Kerberos
- D. RADIUS
- E. LDAP
- F. TACACS+
正解: A,D,F
解説:
Explanation
https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-admin/firewall-administration/manage-firewall-administrat The administrative accounts are defined on an external SAML, TACACS+, or RADIUS server. The server performs both authentication and authorization. For authorization, you define Vendor-Specific Attributes (VSAs) on the TACACS+ or RADIUS server, or SAML attributes on the SAML server.
PAN-OS maps the attributes to administrator roles, access domains, user groups, and virtual systems that you define on the firewall. For details, see:
Configure SAML AuthenticationConfigure TACACS+ AuthenticationConfigure RADIUS Authentication
質問 138
How does an administrator schedule an Applications and Threats dynamic update while delaying installation of the update for a certain amount of time?
- A. Automatically "download and install" but with the "disable new applications" option used.
- B. Configure the option for "Threshold".
- C. Disable automatic updates during weekdays.
- D. Automatically "download only" and then install Applications and Threats later, after the administrator approves the update.
正解: B
解説:
For Antivirus and Applications and Threats updates, you have the option to set a minimum Threshold of time that a content update must be available before the firewall installs it. Very rarely, there can be an error in a content update and this threshold ensures that the firewall only downloads content releases that have been available and functioning in customer environments for the specified amount of time. https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-web-interface-help/device/device-dynamic-updates
https://docs.paloaltonetworks.com/pan-os/10-0/pan-os-web-interface-help/device/device-dynamic-updates.html
質問 139
An administrator needs to evaluate a recent policy change that was committed and pushed to a firewall device group.
How should the administrator identify the configuration changes?
- A. context-switch to the affected firewall and use the configuration audit tool
- B. review the configuration logs on the Monitor tab
- C. click Preview Changes under Push Scope
- D. use Test Policy Match to review the policies in Panorama
正解: C
解説:
Explanation
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-web-interface-help/panorama-web-interface/panorama-com
質問 140
With the default TCP and UDP settings on the firewall, what will be the identified application in the following session?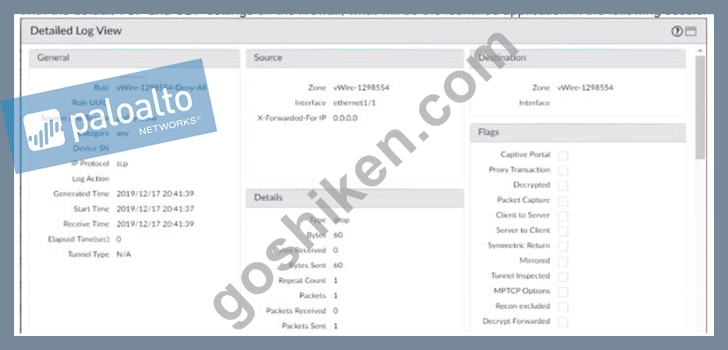
- A. Incomplete
- B. unknown-udp
- C. not-applicable
- D. Insufficient-data
正解: B
質問 141
Which configuration task is best for reducing load on the management plane?
- A. Disable pre-defined reports
- B. Disable logging on the default deny rule
- C. Set the URL filtering action to send alerts
- D. Enable session logging at start
正解: B
質問 142
......
究極のガイドはPCNSE最新時間限定今すぐダウンロード!:https://www.goshiken.com/Palo-Alto-Networks/PCNSE-mondaishu.html
2023年最新のな厳密検証された合格できるPCNSE試験にはリアル問題と解答:https://drive.google.com/open?id=1ce7TdI6ASs9iAHlLOOL5tpYv3XvfcHjw
