[2023年10月] 問題集練習試験問題学習ガイドは500-220試験合格させます
500-220問題集には練習試験問題解答
質問 # 32
Which API endpoint clones a new Organization?
- A. POST /organizations/{organizationId}/new
- B. PUT /organizations/{organizationId}/clone
- C. POST /organizations/clone/{organizationId}
- D. POST /organizations/{organizationId}/clone
正解:A
質問 # 33
What is the role of the Meraki Dashboard as the service provider when using SAML for single sign-on to the Dashboard?
- A. The Dashboard generates the SAML request.
- B. The Dashboard generates the SAML response.
- C. The Dashboard provides user access credentials.
- D. The Dashboard parses the SAML request and authenticates users.
正解:A
質問 # 34
Refer to the exhibit.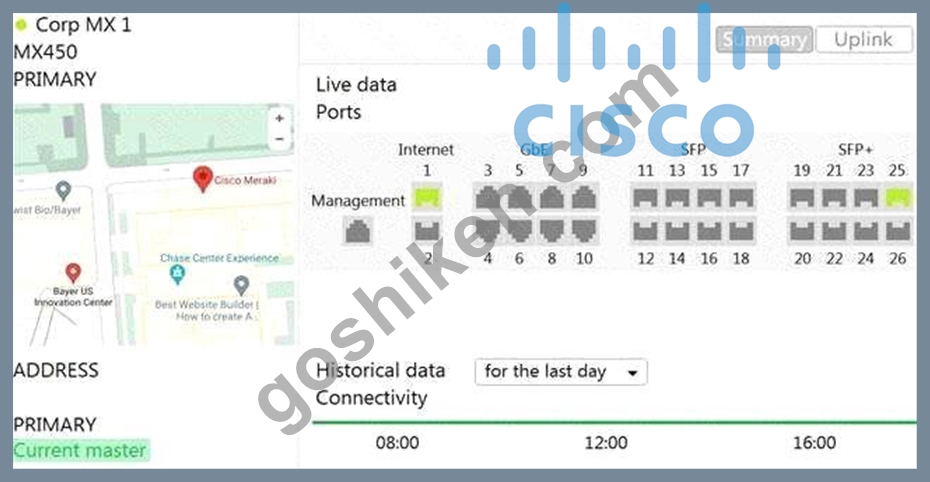
The VPN concentrator is experiencing issues. Which action should be taken to ensure a stable environment?
- A. Configure the MX appliance to Routed mode on the Addressing & VLANS page.
- B. Add a deny any/any firewall rule to the end of the firewall rules.
- C. Physically disconnect all LAN ports.
- D. Remove the connection from Internet 1.
正解:C
解説:
Explanation
Before deploying MXs as one-arm VPN concentrators, place them into Passthrough or VPN Concentrator mode on the Addressing and VLANs page. In one-armed VPN concentrator mode, the units in the pair are connected to the network "only" via their respective 'Internet' ports. Make sure they are NOT connected directly via their LAN ports. Each MX must be within the same IP subnet and able to communicate with each other, as well as with the Meraki dashboard. Only VPN traffic is routed to the MX, and both ingress and egress packets are sent through the same interface.
https://documentation.meraki.com/Architectures_and_Best_Practices/Cisco_Meraki_Best_Practice_Design/Best
質問 # 35
One thousand concurrent users stream video to their laptops. A 30/70 split between 2.4 GHz and 5 GHz is used.
Based on client count, how many APs (rounded to the nearest whole number) are needed?
- A. 0
- B. 1
- C. 2
- D. 3
正解:C
解説:
Explanation
https://documentation.meraki.com/Architectures_and_Best_Practices/Cisco_Meraki_Best_Practice_Design/Best
質問 # 36
Which configuration step is necessary when automatic updating is required of iOS apps provisioned through Systems Manager that are found in the App Store?
- A. No configuration step is necessary; automatic updating is the default behavior.
- B. Create a profile with automatic update enabled and apply it to iOS devices.
- C. Create a security policy that enables automatic updates.
- D. Configure automatic updating of iOS devices in the Meraki installed profile.
正解:C
質問 # 37
Which design requirement is met by implementing syslog versus SNMP?
- A. when information such as flows and client connectivity must be gathered
- B. when proactive alerts for critical events must be generated
- C. when automation capabilities are needed
- D. when organization-wide information must be collected
正解:A
解説:
Explanation
Implementing syslog versus SNMP can meet the design requirement of gathering information such as flows and client connectivity. Syslog can collect and report various types of events, such as VPN connectivity, uplink connectivity, DHCP leases, firewall rules, IDS alerts, and security events. Syslog can also provide detailed information about the flows and client connectivity on the network devices, such as source and destination IP addresses, ports, protocols, bytes transferred, etc. SNMP, on the other hand, can collect and report various statistics and information about the network devices, such as CPU utilization, interface status, memory usage, etc. However, SNMP does not provide as much information about the flows and client connectivity as syslog does.
質問 # 38
Which VLAN is used to source pings across the site-to-site VPN when using the MX Live tools?
- A. highest VLAN ID that is configured and set to NO to use VPN
- B. highest VLAN ID that is configured and set to YES to use VPN
- C. lowest VLAN ID configured and set to NO to use VPN
- D. lowest VLAN ID that is configured and set to YES to use VPN
正解:B
解説:
Reference:
Using_the_Ping_Live_Tool
質問 # 39
Refer to the exhibit.
For an AP that displays this alert, which network access control method must be in use?
- A. splash page with my RADIUS server
- B. preshared key
- C. WPA2-enterprise with my RADIUS server
- D. MAC-based access control with RADIUS server
正解:C
解説:
Explanation
This is because the alert mentions 802.1X failure, which is a network access control method that is used with WPA2-enterprise and RADIUS servers1.
This question is related to the topic of Wireless Access Points Quick Start in the Cisco Meraki documentation.
You can find more information about this topic in the Wireless Access Points Quick Start article or the Using the Cisco Meraki Device Local Status Page page.
質問 # 40
Which Cisco Meraki product must be deployed in addition to Systems Manager so that Systems Manager Sentry enrollment can be used?
- A. MS Switch
- B. Meraki Insight
- C. MR Access Point
- D. MV Smart Camera
正解:C
解説:
Explanation
https://documentation.meraki.com/MR/MR_Splash_Page/Systems_Manager_Sentry_Enrollment
質問 # 41
What is the best practice Systems Manager enrollment method when deploying corporate-owned iOS devices?
- A. Apple Configurator
- B. DEP
- C. manual
- D. Sentry enrollment
正解:B
解説:
Explanation
iOS devices that are using Apple's Device Enrollment Program (DEP) can be supervised and enrolled over-the-air anytime they are factory reset. DEP is the best way to permanently force your devices to be owned and managed by your organization, and it is important to assign your DEP settings properly before deployment.
https://documentation.meraki.com/SM/Device_Enrollment/Enrolling_and_Supervising_iOS_Devices_using_App
質問 # 42
Refer to the exhibit.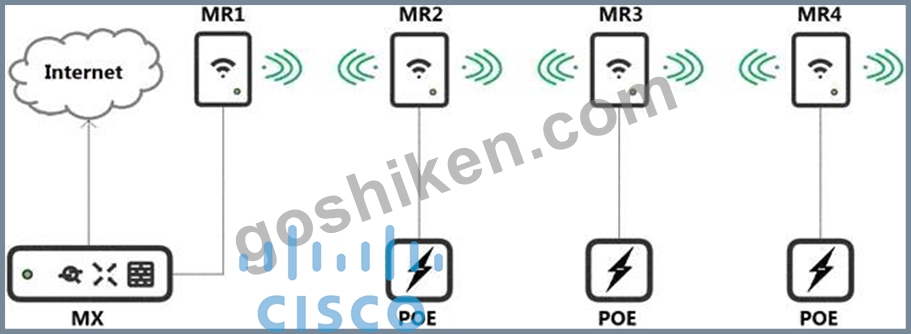
Which design recommendation should be considered?
- A. A 50-percent throughput loss occurs for every hop. Cisco Meraki best practice recommends a 1-hop maximum.
- B. A 25-percent throughput loss occurs for every hop. Cisco Meraki best practice recommends a 1-hop maximum.
- C. A 50-percent throughput loss occurs for every hop. Cisco Meraki best practice recommends a 2-hop maximum.
- D. A 25-percent throughput loss occurs for every hop. Cisco Meraki best practice recommends a 2-hop maximum.
正解:A
解説:
Explanation
https://documentation.meraki.com/MR/Deployment_Guides/Mesh_Deployment_Guide There will be a throughput reduction (~50% reduction) with each "hop" in a mesh. It is recommended that a mesh network be designed for no more than one mesh hop from the gateway to client device.
質問 # 43
A Cisco Meraki MX security appliance is trying to route a packet to the destination IP address of
172.18.24.12. Which routes contained in its routing table does it select?
- A. directly connected 172.18.16.0/20
- B. static route 172.16.0.0/12
- C. Auto VPN route 172.18.0.0/16
- D. non-Meraki VPN route 172.18.24.0/24
正解:D
解説:
Explanation
Route Priority
Each type of route configured on the MX has a specific priority in comparison with other types of routes. The priority is as follows:
Directly Connected
Client VPN
Static Routes
AutoVPN Routes
Non-Meraki VPN Peers
BGP learned Routes
NAT*
https://documentation.meraki.com/MX/Networks_and_Routing/MX_Routing_Behavior
質問 # 44
Which API endpoint clones a new Organization?
- A. POST /organizations/{organizationId}/new
- B. POST /organizations/{organizationId}/clone
- C. PUT /organizations/{organizationId}/clone
- D. POST /organizations/clone/{organizationId}
正解:B
解説:
Explanation
https://developer.cisco.com/meraki/api-v1/#!clone-organization
質問 # 45
When an SSID is configured with Sign-On Splash page enabled, which two settings must be configured for unauthenticated clients to have full network access and not be allow listed? (Choose two.)
- A. Captive Portal strength
- B. Controller disconnection behavior
- C. Simultaneous logins
- D. RADIUS for splash page settings
- E. Firewall & traffic shaping
正解:A、B
解説:
Explanation
To clarify, when an SSID is configured with Sign-On Splash page enabled, the two settings that must be configured for unauthenticated clients to have full network access and not be allow listed are:
Controller disconnection behavior: This setting determines how the clients are treated when the Meraki cloud controller is unreachable. The options are Restricted or Unrestricted. The former option blocks all traffic from unauthenticated clients until the controller is reachable again. The latter option allows unauthenticated clients to access the network without signing on until the controller is reachable again1.
Captive Portal strength: This setting determines how often the clients are redirected to the splash page for authentication. The options are Block all access until sign-on is complete or Allow non-HTTP traffic prior to sign-on. The latter option allows unauthenticated clients to access other protocols such as DNS, DHCP, ICMP, etc., but blocks HTTP and HTTPS traffic until they sign on. This option is recommended for compatibility with devices that do not support web-based authentication1.
質問 # 46
Where should a network admin navigate to investigate wireless mesh information between Meraki APs?
- A. Wireless > Monitor > Access Points > AP > RF
- B. Wireless > Monitor > Wireless Health
- C. Wireless > Monitor > RF Spectrum
- D. Wireless > Configure > Radio Settings
正解:A
解説:
Explanation
See Monitoring Mesh section Mesh monitoring tools are located at the bottom of every AP detail page, which can be accessed by navigating to Wireless > Monitor > Access Points, then clicking on an Access Point.
https://documentation.meraki.com/MR/Wi-Fi_Basics_and_Best_Practices/Wireless_Mesh_Networking
質問 # 47
When wireless SSIDs are configured in Dashboard, which setting on the Access Control page affects the ability of a 2.4 GHz only client device from associating to the WLAN for the first time?
- A. Content filtering
- B. 802.11r
- C. Bridge mode
- D. Dual band operating with Band Steering
正解:D
質問 # 48
Which Cisco Meraki best practice method preserves complete historical network event logs?
- A. Configuring the preserved event period to unlimited.
- B. Configuring Dashboard logging to preserve only certain event types.
- C. Configuring a syslog server for the network.
- D. Configuring the preserved event number to maximize logging.
正解:C
解説:
Explanation
Configuring a syslog server for the network is the Cisco Meraki best practice method to preserve complete historical network event logs. A syslog server can be configured to store messages for reporting purposes from MX Security Appliances, MR Access Points, and MS switches1. The syslog server can collect various types of events, such as VPN connectivity, uplink connectivity, DHCP leases, firewall rules, IDS alerts, and security events2. The syslog server can also help with troubleshooting and monitoring the network performance and security.
質問 # 49
......
無料Cisco Meraki Solutions Specialist 500-220試験問題:https://www.goshiken.com/Cisco/500-220-mondaishu.html
500-220はCisco Meraki Solutions Specialist実際の無料試験練習テスト:https://drive.google.com/open?id=1OpO58slaJfE4AJDN-26Nz4aUSWOvkxW3
