[2022年03月] を試そう!リアルNSE7_OTS-6.4問題集で100%無料NSE7_OTS-6.4試験問題集
NSE7_OTS-6.4のPDF問題集試験問題 有効なNSE7_OTS-6.4問題集
Fortinet NSE7_OTS-6.4 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
質問 19
You are investigating a series of incidents that occurred in the OT network over past 24 hours in FortiSIEM.
Which three FortiSIEM options can you use to investigate these incidents? (Choose three.)
- A. Overview
- B. Security
- C. List
- D. Risk
- E. IPS
正解: A,C,D
質問 20
Refer to the exhibit and analyze the output.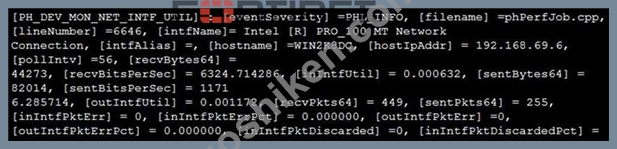
Which statement about the output is true?
- A. This is a sample of FortiGate interface statistics.
- B. This is a sample of an SNMP temperature control event log.
- C. This is a sample of a PAM event type.
- D. This is a sample of a FortiAnalyzer system interface event log.
正解: D
質問 21
An OT architect has deployed a Layer 2 switch in the OT network at Level 1 the Purdue model-process control. The purpose of the Layer 2 switch is to segment traffic between PLC1 and PLC2 with two VLANs. All the traffic between PLC1 and PLC2 must first flow through the Layer 2 switch and then through the FortiGate device in the Level 2 supervisory control network.
What statement about the traffic between PLC1 and PLC2 is true?
- A. In order to communicate, PLC1 must be in the same VLAN as PLC2.
- B. The Layer 2 switches routes any traffic to the FortiGate device through an Ethernet link.
- C. The Layer 2 switch rewrites VLAN tags before sending traffic to the FortiGate device.
- D. PLC1 and PLC2 traffic must flow through the Layer-2 switch trunk link to the FortiGate device.
正解: D
質問 22
An OT administrator deployed many devices to secure the OT network. However, the SOC team is reporting that there are too many alerts, and that many of the alerts are false positive. The OT administrator would like to find a solution that eliminates repetitive tasks, improves efficiency, saves time, and saves resources.
Which products should the administrator deploy to address these issues and automate most of the manual tasks done by the SOC team?
- A. FortiSIEM and FortiManager
- B. A syslog server and FortiSIEM
- C. FortiSandbox and FortiSIEM
- D. FortiSOAR and FortiSIEM
正解: D
質問 23
Refer to the exhibit.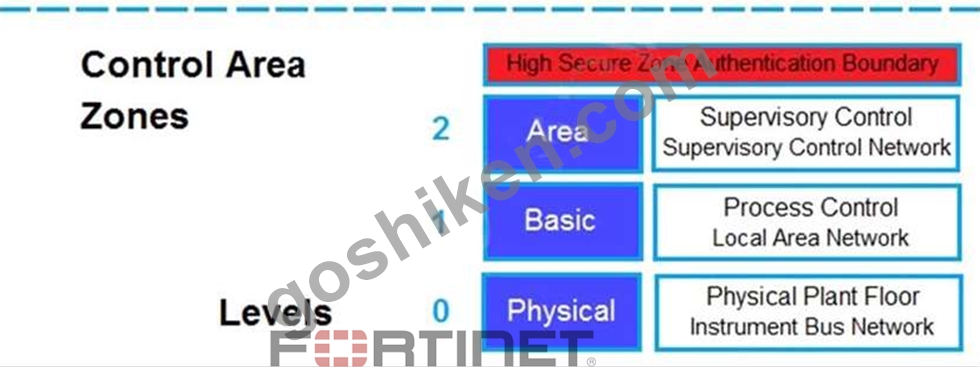
Based on the Purdue model, which three measures can be implemented in the control area zone using the Fortinet Security Fabric? (Choose three.)
- A. FortiNAC for network access control
- B. FortiEDR for endpoint detection
- C. FortiGate for application control and IPS
- D. FortiGate for SD-WAN
- E. FortiSIEM for security incident and event management
正解: A,C,E
質問 24
Which three criteria can a FortiGate device use to look for a matching firewall policy to process traffic? (Choose three.)
- A. Source defined as internet services in the firewall policy
- B. Highest to lowest priority defined in the firewall policy
- C. Destination defined as internet services in the firewall policy
- D. Services defined in the firewall policy.
- E. Lowest to highest policy ID number
正解: A,C,D
質問 25
As an OT administrator, it is important to understand how industrial protocols work in an OT network.
Which communication method is used by the Modbus protocol?
- A. It uses OSI Layer 2 and the primary device sends data based on request from secondary device.
- B. It uses OSI Layer 2 and both the primary/secondary devices send data based on a matching token ring.
- C. It uses OSI Layer 2 and the secondary device sends data based on request from primary device.
- D. It uses OSI Layer 2 and both the primary/secondary devices always send data during the communication.
正解: C
質問 26
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
- A. Each playbook can include multiple triggers.
- B. You cannot use Windows and Linux hosts security events with FortiSoC.
- C. You can automate SOC tasks through playbooks.
- D. You must set correct operator in event handler to trigger an event.
正解: A,C
解説:
Ref: https://docs.fortinet.com/document/fortianalyzer/7.0.0/administration-guide/268882/fortisoc
質問 27
Refer to the exhibit.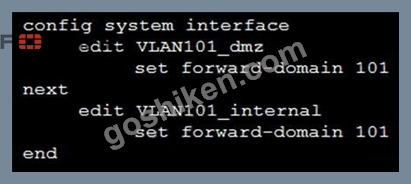
Given the configurations on the FortiGate, which statement is true?
- A. FortiGate is configured with forward-domains to forward only domain controller traffic.
- B. FortiGate is configured with forward-domains to forward only company domain website traffic.
- C. FortiGate is configured with forward-domains to reduce unnecessary traffic.
- D. FortiGate is configured with forward-domains to filter and drop non-domain controller traffic.
正解: C
質問 28
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
- A. Configure a firewall policy with LDAP users and place it on the top of list of firewall policies.
- B. Under config user settings configure set auth-on-demand implicit.
- C. Configure a firewall policy with FSSO users and place it on the top of list of firewall policies.
- D. Enable two-factor authentication with FSSO.
正解: B
質問 29
An OT supervisor needs to protect their network by implementing security with an industrial signature database on the FortiGate device.
Which statement about the industrial signature database on FortiGate is true?
- A. An administrator must create their own database using custom signatures.
- B. A supervisor can enable it through the FortiGate CLI.
- C. A supervisor must purchase an industrial signature database and import it to the FortiGate.
- D. By default, the industrial database is enabled.
正解: B
質問 30
Which three methods of communication are used by FortiNAC to gather visibility information? (Choose three.)
- A. SNMP
- B. RADIUS
- C. TACACS
- D. API
- E. ICMP
正解: A,B,D
質問 31
When device profiling rules are enabled, which devices connected on the network are evaluated by the device profiling rules?
- A. Rogue devices, each time they connect
- B. Known trusted devices, each time they change location
- C. All connected devices, each time they connect
- D. Rogue devices, only when they connect for the first time
正解: D
質問 32
Refer to the exhibit, which shows a non-protected OT environment.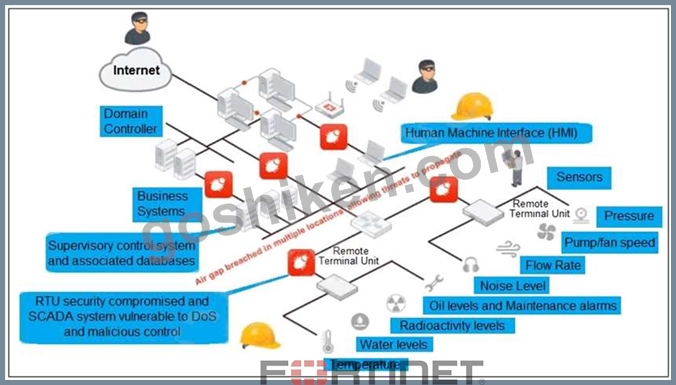
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
- A. Deploy an edge FortiGate between the internet and an OT network as a one-arm sniffer.
- B. Configure firewall policies with industrial protocol sensors
- C. Deploy a FortiGate device within each ICS network.
- D. Use segmentation
- E. Configure firewall policies with web filter to protect the different ICS networks.
正解: A,B,E
質問 33
......
究極のNSE7_OTS-6.4無料準備ガイド最新のFortinet練習テスト問題集:https://www.goshiken.com/Fortinet/NSE7_OTS-6.4-mondaishu.html
