[2023年11月28日]NSE7_OTS-6.4試験問題集を試そう!ベストNSE7_OTS-6.4試験問題
検証済みのNSE7_OTS-6.4テスト問題集で正確な37問題と解答
Fortinet NSE7_OTS -6.4(Fortinet NSE 7 -OT Security 6.4)認定試験は、運用技術(OT)ネットワークを保護するための知識とスキルをテストするために設計されています。この試験は、産業制御システム(ICS)およびSCADAネットワークの保護を担当する専門家に適しています。 NSE7_OTS-6.4の試験では、OTセキュリティの基礎、ICSおよびSCADAセキュリティ、脅威の検出と応答、ネットワークセグメンテーションなど、幅広いトピックをカバーしています。
Fortinet NSE 7 -OTセキュリティ6.4認定は、サイバーセキュリティ業界で非常に尊敬されており、OTセキュリティの専門知識を検証しています。この認定は、重要なインフラストラクチャを確保し、サイバーの脅威から保護するために必要なスキルと知識を持っていることを示しています。この認定を達成することは、あなたのキャリアを昇進させ、収益の可能性を高めるのにも役立ちます。 IoTデバイスの採用が増加し、OTセキュリティの重要性が高まっているため、NSE 7 -OTセキュリティ6.4認定を持つ専門家の需要が今後数年で増加すると予想されます。
Fortinet NSE7_OTS -6.4(Fortinet NSE 7 -OTセキュリティ6.4)認定試験は、運用技術(OT)セキュリティの分野でIT専門家の知識とスキルをテストするように設計されています。この認定試験は、産業制御システム(ICS)や監督制御およびデータ収集(SCADA)システムなどのOTシステムの保護と管理を担当する個人に最適です。この試験では、OTセキュリティの概念、ネットワーク設計とアーキテクチャ、セキュリティプロトコル、リスク管理、インシデント対応など、幅広いトピックをカバーしています。
質問 # 11
What can be assigned using network access control policies?
- A. FortiNAC device polling methods
- B. Layer 3 polling intervals
- C. Profiling rules
- D. Logical networks
正解:D
質問 # 12
When you create a user or host profile, which three criteria can you use? (Choose three.)
- A. Host or user attributes
- B. Host or user group memberships
- C. An existing access control policy
- D. Location
- E. Administrative group membership
正解:A、B、D
解説:
https://docs.fortinet.com/document/fortinac/9.2.0/administration-guide/15797/user-host-profiles
質問 # 13
You are investigating a series of incidents that occurred in the OT network over past 24 hours in FortiSIEM.
Which three FortiSIEM options can you use to investigate these incidents? (Choose three.)
- A. Risk
- B. IPS
- C. Security
- D. List
- E. Overview
正解:A、D、E
質問 # 14
An OT network administrator is trying to implement active authentication.
Which two methods should the administrator use to achieve this? (Choose two.)
- A. Two-factor authentication on FortiAuthenticator
- B. FSSO authentication on FortiGate
- C. Local authentication on FortiGate
- D. Role-based authentication on FortiNAC
正解:A、C
質問 # 15
Refer to the exhibit.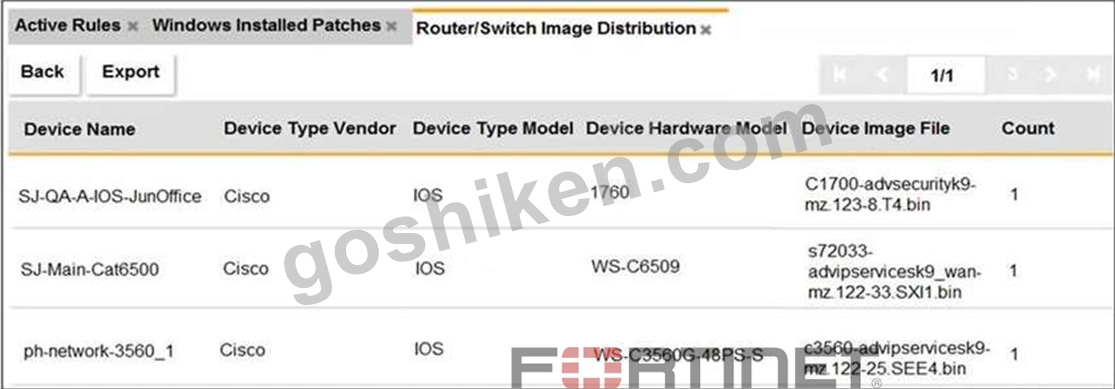
An OT administrator ran a report to identify device inventory in an OT network.
Based on the report results, which report was run?
- A. A FortiSIEM analytics report
- B. A FortiSIEM CMDB report
- C. A FortiAnalyzer device report
- D. A FortiSIEM incident report
正解:B
質問 # 16
Refer to the exhibit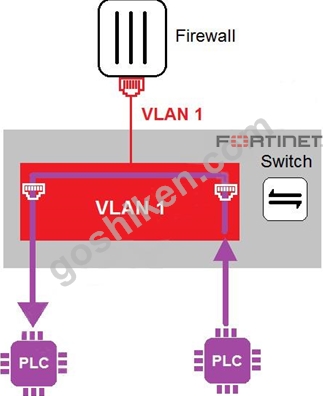
In the topology shown in the exhibit, both PLCs can communicate directly with each other, without going through the firewall.
Which statement about the topology is true?
- A. An administrator can create firewall policies in the switch to secure between PLCs.
- B. This integration solution expands VLAN capabilities from Layer 2 to Layer 3.
- C. PLCs use IEEE802.1Q protocol to communicate each other.
- D. There is no micro-segmentation in this topology.
正解:D
質問 # 17
An OT administrator configured and ran a default application risk and control report in FortiAnalyzer to learn more about the key application crossing the network. However, the report output is empty despite the fact that some related real-time and historical logs are visible in the FortiAnalyzer.
What are two possible reasons why the report output was empty? (Choose two.)
- A. The administrator selected the wrong logs to be indexed in FortiAnalyzer.
- B. The administrator selected the wrong time period for the report.
- C. The administrator selected the wrong hcache table for the report.
- D. The administrator selected the wrong devices in the Devices section.
正解:B、C
質問 # 18
Refer to the exhibit.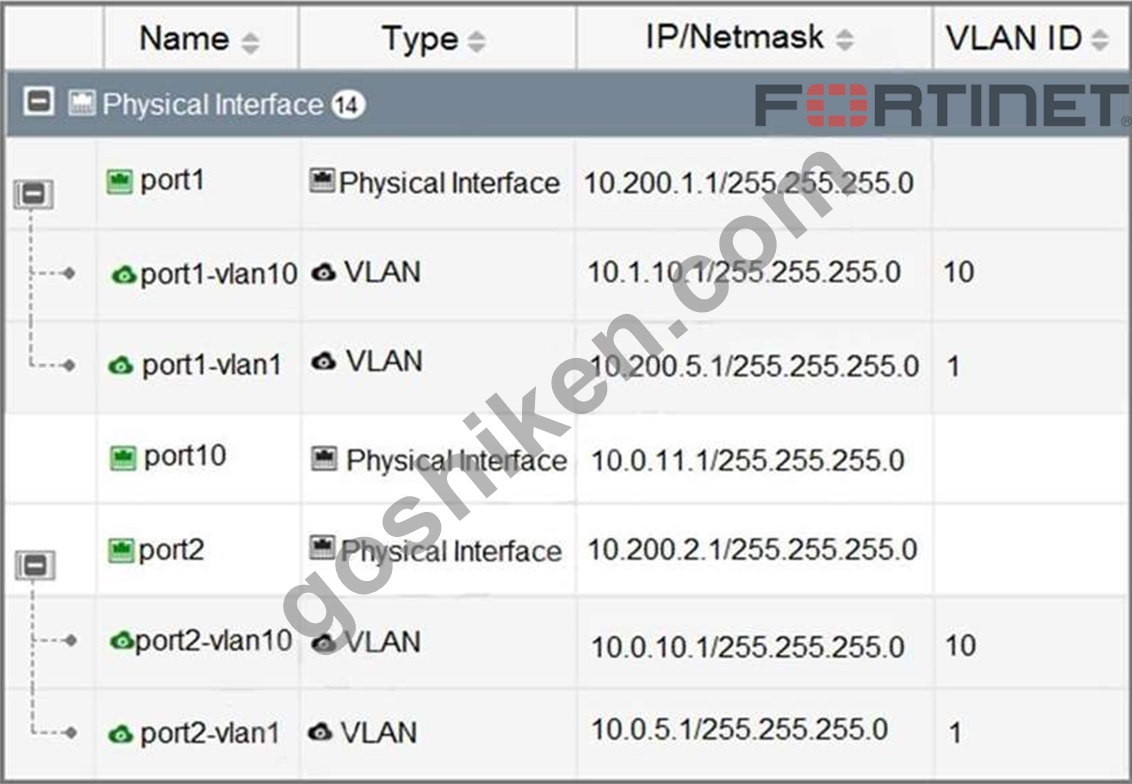
Which statement about the interfaces shown in the exhibit is true?
- A. The VLAN ID of port1-vlan1 can be changed to the VLAN ID 10.
- B. port2, port2-vlan10, and port2-vlan1 are part of the software switch interface.
- C. port1-vlan10 and port2-vlan10 are part of the same broadcast domain
- D. port1, port1-vlan10, and port1-vlan1 are in different broadcast domains
正解:D
質問 # 19
Refer to the exhibit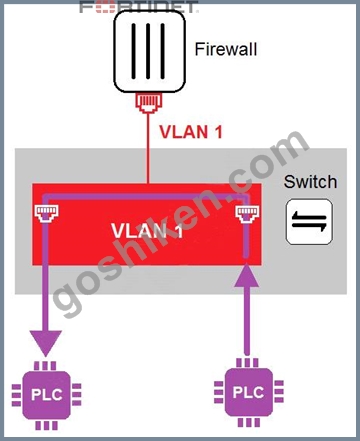
In the topology shown in the exhibit, both PLCs can communicate directly with each other, without going through the firewall.
Which statement about the topology is true?
- A. An administrator can create firewall policies in the switch to secure between PLCs.
- B. This integration solution expands VLAN capabilities from Layer 2 to Layer 3.
- C. PLCs use IEEE802.1Q protocol to communicate each other.
- D. There is no micro-segmentation in this topology.
正解:D
質問 # 20
Refer to the exhibit.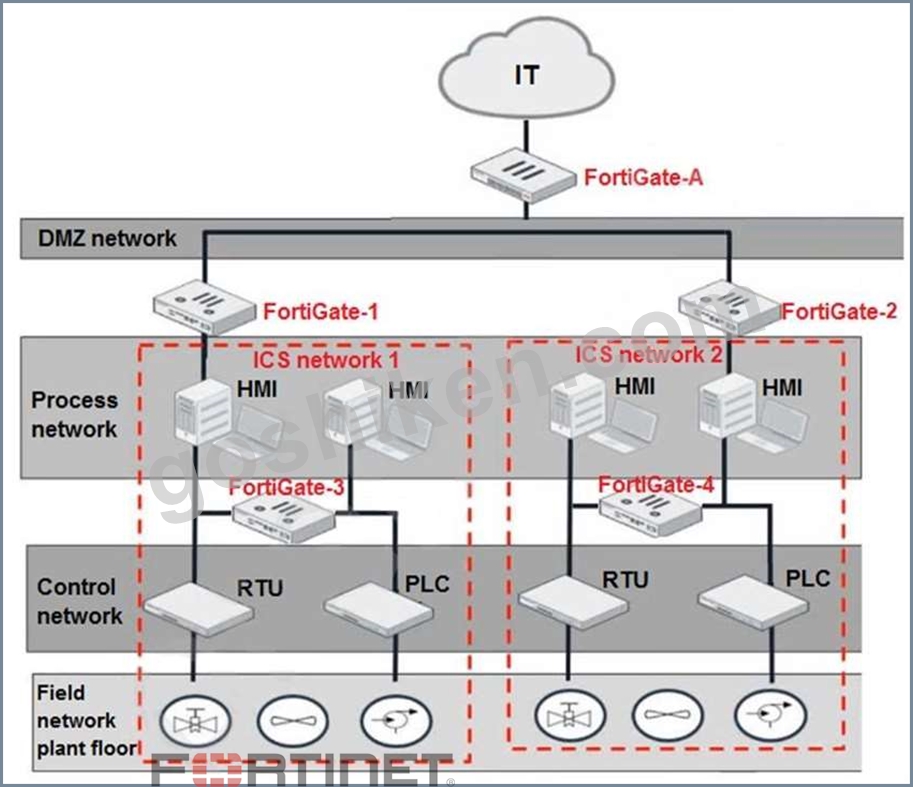
Based on the topology designed by the OT architect, which two statements about implementing OT security are true? (Choose two.)
- A. IT and OT networks are separated by segmentation.
- B. Micro-segmentation can be achieved only by replacing FortiGate-3 and FortiGate-4 with a pair of FortiSwitch devices.
- C. Firewall policies should be configured on FortiGate-3 and FortiGate-4 with industrial protocol sensors.
- D. FortiGate-3 and FortiGate-4 devices must be in a transparent mode.
正解:A、C
質問 # 21
Which three criteria can a FortiGate device use to look for a matching firewall policy to process traffic? (Choose three.)
- A. Source defined as internet services in the firewall policy
- B. Destination defined as internet services in the firewall policy
- C. Highest to lowest priority defined in the firewall policy
- D. Lowest to highest policy ID number
- E. Services defined in the firewall policy.
正解:A、B、E
質問 # 22
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
- A. You cannot use Windows and Linux hosts security events with FortiSoC.
- B. Each playbook can include multiple triggers.
- C. You must set correct operator in event handler to trigger an event.
- D. You can automate SOC tasks through playbooks.
正解:C、D
解説:
Ref: https://docs.fortinet.com/document/fortianalyzer/7.0.0/administration-guide/268882/fortisoc
質問 # 23
What two advantages does FortiNAC provide in the OT network? (Choose two.)
- A. It can be used for industrial intrusion detection and prevention.
- B. It can be used for network micro-segmentation.
- C. It can be used for IoT device detection.
- D. It can be used for device profiling.
正解:C、D
解説:
Typically, in a microsegmented network, NGFWs are used in conjunction with VLANs to implement security policies and to inspect and filter network communications. Fortinet FortiSwitch and FortiGate NGFW offer an integrated approach to microsegmentation.
質問 # 24
Refer to the exhibit, which shows a non-protected OT environment.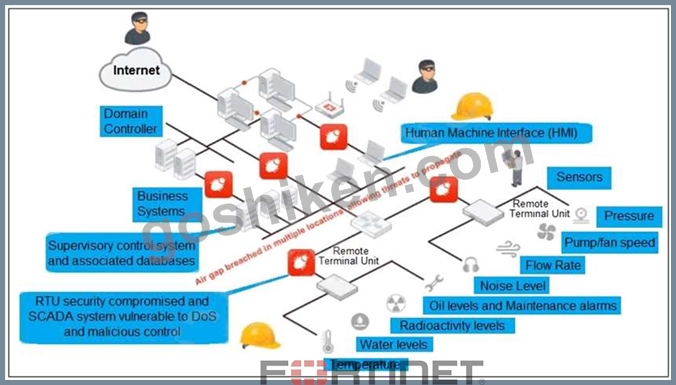
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
- A. Configure firewall policies with web filter to protect the different ICS networks.
- B. Use segmentation
- C. Deploy a FortiGate device within each ICS network.
- D. Deploy an edge FortiGate between the internet and an OT network as a one-arm sniffer.
- E. Configure firewall policies with industrial protocol sensors
正解:A、D、E
質問 # 25
Refer to the exhibit, which shows a non-protected OT environment.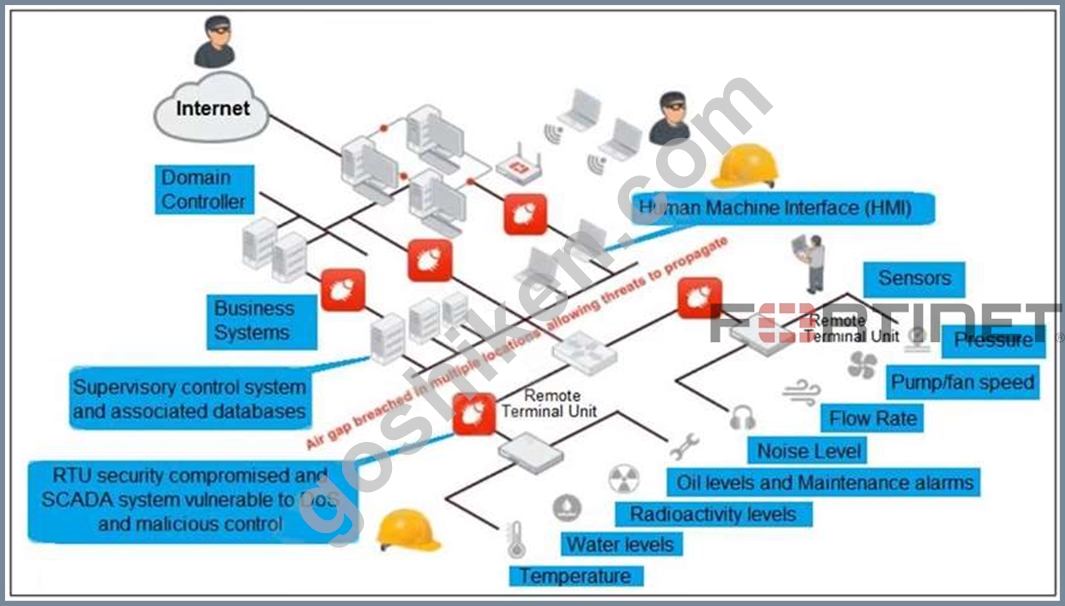
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
- A. Configure firewall policies with web filter to protect the different ICS networks.
- B. Use segmentation
- C. Deploy a FortiGate device within each ICS network.
- D. Deploy an edge FortiGate between the internet and an OT network as a one-arm sniffer.
- E. Configure firewall policies with industrial protocol sensors
正解:A、D、E
質問 # 26
Refer to the exhibit.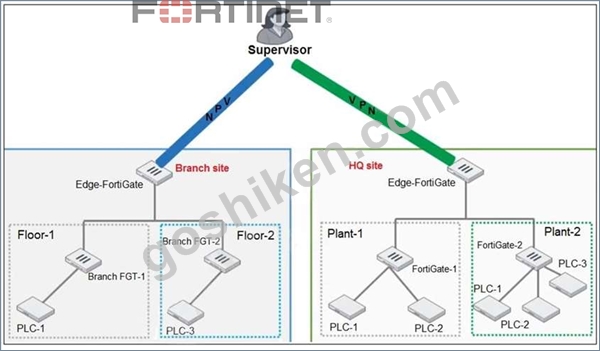
You need to configure VPN user access for supervisors at the breach and HQ sites using the same soft FortiToken. Each site has a FortiGate VPN gateway.
What must you do to achieve this objective?
- A. You must use a FortiAuthenticator.
- B. You must register the same FortiToken on more than one FortiGate.
- C. You must use a third-party RADIUS OTP server.
- D. You must use the user self-registration server.
正解:A
質問 # 27
Which three Fortinet products can be used for device identification in an OT industrial control system (ICS)? (Choose three.)
- A. FortiSIEM
- B. FortiNAC
- C. FortiAnalyzer
- D. FortiGate
- E. FortiManager
正解:A、B、D
解説:
1. FortiNAC - FortiNAC is a network access control solution that provides visibility and control over network devices. It can identify devices, enforce access policies, and automate threat response.
2. FortiSIEM - FortiSIEM is a security information and event management solution that can collect and analyze data from multiple sources, including network devices and servers. It can help identify potential security threats, as well as monitor compliance with security policies and regulations.
3. FortiAnalyzer - FortiAnalyzer is a central logging and reporting solution that collects and analyzes data from multiple sources, including FortiNAC and FortiSIEM. It can provide insights into network activity and help identify anomalies or security threats.
Reference:
Fortinet NSE 7 - OT Security 6.4 Study Guide, Chapter 4: OT Security Devices, page 4-20.
質問 # 28
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
- A. Enable two-factor authentication with FSSO.
- B. Under config user settings configure set auth-on-demand implicit.
- C. Configure a firewall policy with FSSO users and place it on the top of list of firewall policies.
- D. Configure a firewall policy with LDAP users and place it on the top of list of firewall policies.
正解:C
解説:
The OT supervisor should configure a firewall policy with FSSO users and place it on the top of list of firewall policies in order to achieve the goal of authenticating users against passive authentication first and, if passive authentication is not successful, then challenging them with active authentication.
質問 # 29
Refer to the exhibit.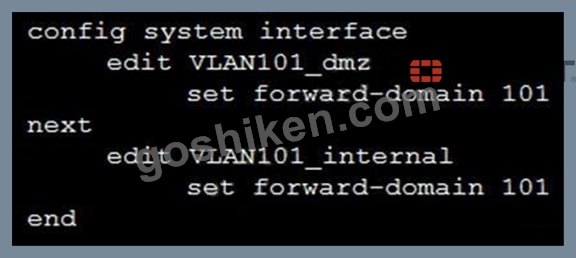
Given the configurations on the FortiGate, which statement is true?
- A. FortiGate is configured with forward-domains to forward only company domain website traffic.
- B. FortiGate is configured with forward-domains to forward only domain controller traffic.
- C. FortiGate is configured with forward-domains to reduce unnecessary traffic.
- D. FortiGate is configured with forward-domains to filter and drop non-domain controller traffic.
正解:C
質問 # 30
An OT network administrator is trying to implement active authentication.
Which two methods should the administrator use to achieve this? (Choose two.)
- A. Role-based authentication on FortiNAC
- B. Two-factor authentication on FortiAuthenticator
- C. Local authentication on FortiGate
- D. FSSO authentication on FortiGate
正解:A、B
質問 # 31
Refer to the exhibit.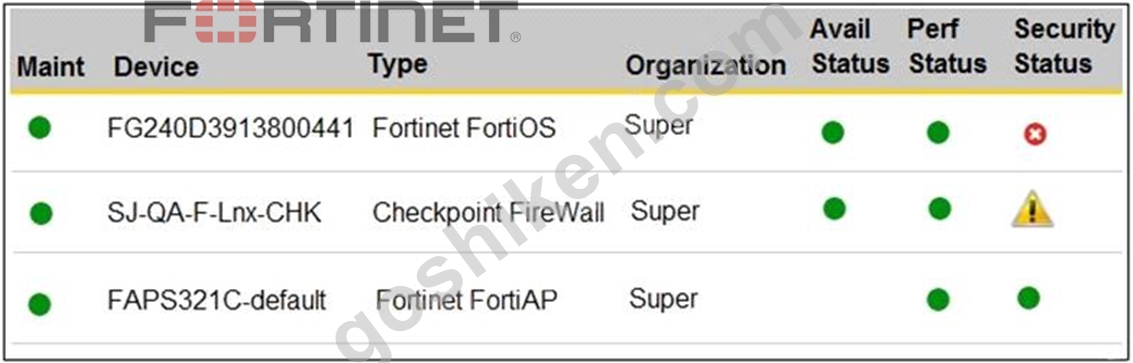
You are navigating through FortiSIEM in an OT network.
How do you view information presented in the exhibit and what does the FortiGate device security status tell you?
- A. In the PCI logging dashboard and there are one or more high-severity security incidents for the FortiGate device.
- B. In the widget dashboard and there are one or more high-severity incidents for the FortiGate device.
- C. In the summary dashboard and there are one or more high-severity security incidents for the FortiGate device.
- D. In the business service dashboard and there are one or more high-severity security incidents for the FortiGate device.
正解:C
質問 # 32
Refer to the exhibit.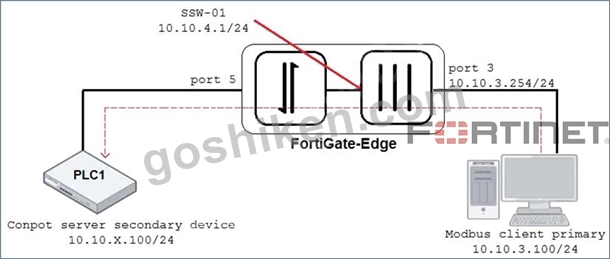
An OT architect has implemented a Modbus TCP with a simulation server Conpot to identify and control the Modus traffic in the OT network. The FortiGate-Edge device is configured with a software switch interface ssw-01.
Based on the topology shown in the exhibit, which two statements about the successful simulation of traffic between client and server are true? (Choose two.)
- A. NAT is disabled in the FortiGate firewall policy from port3 to ssw-01.
- B. Port5 is not a member of the software switch.
- C. The FortiGate devices is in offline IDS mode.
- D. The FortiGate-Edge device must be in NAT mode.
正解:C、D
質問 # 33
......
Fortinet NSE7_OTS-6.4テストエンジンPDFで全問 無料問題集:https://www.goshiken.com/Fortinet/NSE7_OTS-6.4-mondaishu.html
