[2022年04月11日] 最新版を今すぐ試そうNSE7_OTS-6.4練習テスト問題解答
NSE7_OTS-6.4問題集と試験テストエンジン
Fortinet NSE7_OTS-6.4 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
質問 13
What two advantages does FortiNAC provide in the OT network? (Choose two.)
- A. It can be used for network micro-segmentation.
- B. It can be used for device profiling.
- C. It can be used for industrial intrusion detection and prevention.
- D. It can be used for IoT device detection.
正解: A,B
質問 14
As an OT administrator, it is important to understand how industrial protocols work in an OT network.
Which communication method is used by the Modbus protocol?
- A. It uses OSI Layer 2 and the primary device sends data based on request from secondary device.
- B. It uses OSI Layer 2 and both the primary/secondary devices send data based on a matching token ring.
- C. It uses OSI Layer 2 and the secondary device sends data based on request from primary device.
- D. It uses OSI Layer 2 and both the primary/secondary devices always send data during the communication.
正解: C
質問 15
What triggers Layer 2 polling of infrastructure devices connected in the network?
- A. A failed Layer 3 poll
- B. A matched profiling rule
- C. A matched security policy
- D. A linkup or linkdown trap
正解: D
質問 16
Which three criteria can a FortiGate device use to look for a matching firewall policy to process traffic? (Choose three.)
- A. Source defined as internet services in the firewall policy
- B. Highest to lowest priority defined in the firewall policy
- C. Destination defined as internet services in the firewall policy
- D. Services defined in the firewall policy.
- E. Lowest to highest policy ID number
正解: A,C,D
質問 17
An OT supervisor needs to protect their network by implementing security with an industrial signature database on the FortiGate device.
Which statement about the industrial signature database on FortiGate is true?
- A. An administrator must create their own database using custom signatures.
- B. A supervisor can enable it through the FortiGate CLI.
- C. A supervisor must purchase an industrial signature database and import it to the FortiGate.
- D. By default, the industrial database is enabled.
正解: B
質問 18
An OT network administrator is trying to implement active authentication.
Which two methods should the administrator use to achieve this? (Choose two.)
- A. Role-based authentication on FortiNAC
- B. Local authentication on FortiGate
- C. FSSO authentication on FortiGate
- D. Two-factor authentication on FortiAuthenticator
正解: A,D
質問 19
Refer to the exhibit.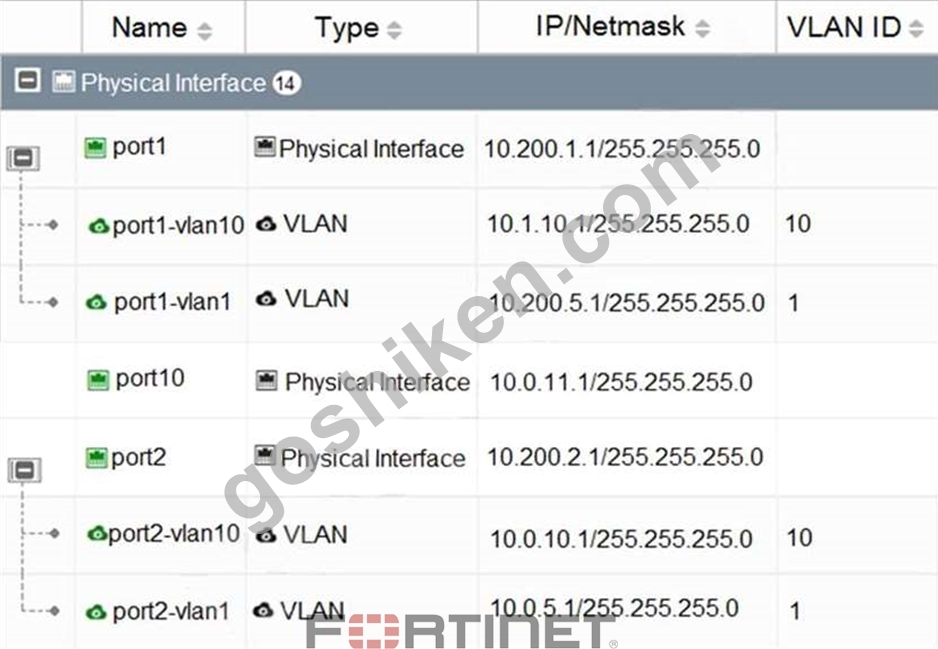
Which statement about the interfaces shown in the exhibit is true?
- A. The VLAN ID of port1-vlan1 can be changed to the VLAN ID 10.
- B. port1, port1-vlan10, and port1-vlan1 are in different broadcast domains
- C. port1-vlan10 and port2-vlan10 are part of the same broadcast domain
- D. port2, port2-vlan10, and port2-vlan1 are part of the software switch interface.
正解: B
質問 20
Refer to the exhibit.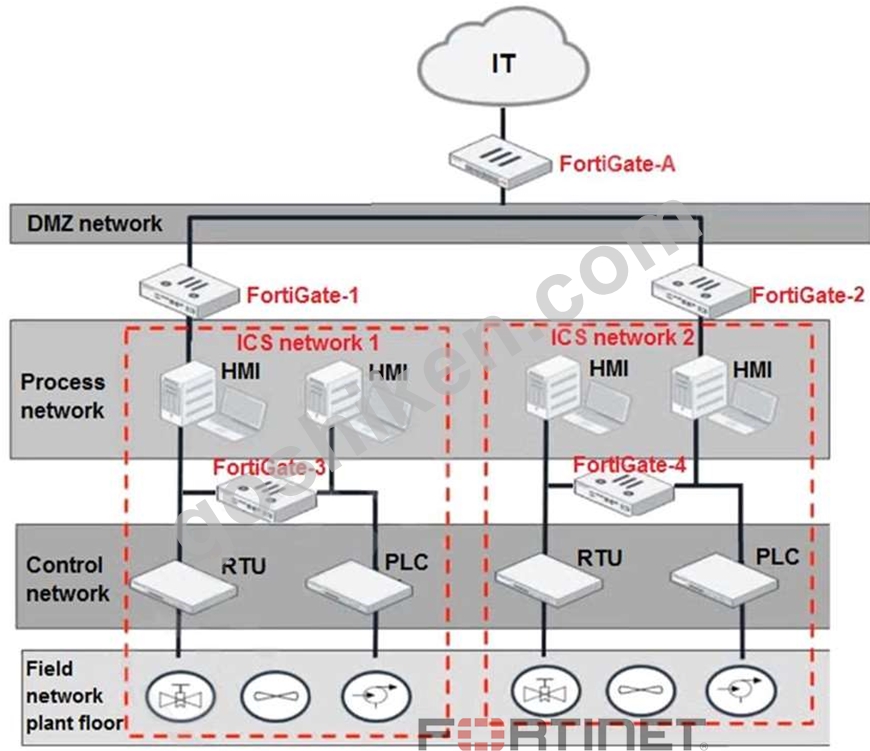
Based on the topology designed by the OT architect, which two statements about implementing OT security are true? (Choose two.)
- A. IT and OT networks are separated by segmentation.
- B. Micro-segmentation can be achieved only by replacing FortiGate-3 and FortiGate-4 with a pair of FortiSwitch devices.
- C. FortiGate-3 and FortiGate-4 devices must be in a transparent mode.
- D. Firewall policies should be configured on FortiGate-3 and FortiGate-4 with industrial protocol sensors.
正解: A,C
質問 21
When device profiling rules are enabled, which devices connected on the network are evaluated by the device profiling rules?
- A. Rogue devices, each time they connect
- B. Known trusted devices, each time they change location
- C. All connected devices, each time they connect
- D. Rogue devices, only when they connect for the first time
正解: D
質問 22
An OT architect has deployed a Layer 2 switch in the OT network at Level 1 the Purdue model-process control. The purpose of the Layer 2 switch is to segment traffic between PLC1 and PLC2 with two VLANs. All the traffic between PLC1 and PLC2 must first flow through the Layer 2 switch and then through the FortiGate device in the Level 2 supervisory control network.
What statement about the traffic between PLC1 and PLC2 is true?
- A. In order to communicate, PLC1 must be in the same VLAN as PLC2.
- B. The Layer 2 switches routes any traffic to the FortiGate device through an Ethernet link.
- C. The Layer 2 switch rewrites VLAN tags before sending traffic to the FortiGate device.
- D. PLC1 and PLC2 traffic must flow through the Layer-2 switch trunk link to the FortiGate device.
正解: D
質問 23
An OT network architect needs to secure control area zones with a single network access policy to provision devices to any number of different networks.
On which device can this be accomplished?
- A. FortiNAC
- B. FortiEDR
- C. FortiSwitch
- D. FortiGate
正解: A
質問 24
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
- A. Each playbook can include multiple triggers.
- B. You cannot use Windows and Linux hosts security events with FortiSoC.
- C. You can automate SOC tasks through playbooks.
- D. You must set correct operator in event handler to trigger an event.
正解: A,C
解説:
Ref: https://docs.fortinet.com/document/fortianalyzer/7.0.0/administration-guide/268882/fortisoc
質問 25
An OT administrator configured and ran a default application risk and control report in FortiAnalyzer to learn more about the key application crossing the network. However, the report output is empty despite the fact that some related real-time and historical logs are visible in the FortiAnalyzer.
What are two possible reasons why the report output was empty? (Choose two.)
- A. The administrator selected the wrong time period for the report.
- B. The administrator selected the wrong hcache table for the report.
- C. The administrator selected the wrong devices in the Devices section.
- D. The administrator selected the wrong logs to be indexed in FortiAnalyzer.
正解: A,B
質問 26
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
- A. Configure a firewall policy with LDAP users and place it on the top of list of firewall policies.
- B. Under config user settings configure set auth-on-demand implicit.
- C. Configure a firewall policy with FSSO users and place it on the top of list of firewall policies.
- D. Enable two-factor authentication with FSSO.
正解: B
質問 27
......
2022年最新のGoShiken NSE7_OTS-6.4のPDFで最近更新された問題です:https://www.goshiken.com/Fortinet/NSE7_OTS-6.4-mondaishu.html
