NSE7_OTS-6.4問題集最新版を今すぐ試そう![2022年01月] 試験準備には欠かせません!
有能な受験者がシミュレーション済みのNSE7_OTS-6.4試験PDF問題を試そう
質問 20
Which three criteria can a FortiGate device use to look for a matching firewall policy to process traffic? (Choose three.)
- A. Source defined as internet services in the firewall policy
- B. Highest to lowest priority defined in the firewall policy
- C. Destination defined as internet services in the firewall policy
- D. Services defined in the firewall policy.
- E. Lowest to highest policy ID number
正解: A,C,D
質問 21
Refer to the exhibit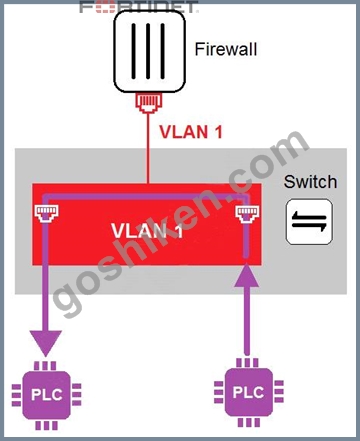
In the topology shown in the exhibit, both PLCs can communicate directly with each other, without going through the firewall.
Which statement about the topology is true?
- A. This integration solution expands VLAN capabilities from Layer 2 to Layer 3.
- B. An administrator can create firewall policies in the switch to secure between PLCs.
- C. There is no micro-segmentation in this topology.
- D. PLCs use IEEE802.1Q protocol to communicate each other.
正解: C
質問 22
As an OT administrator, it is important to understand how industrial protocols work in an OT network.
Which communication method is used by the Modbus protocol?
- A. It uses OSI Layer 2 and the primary device sends data based on request from secondary device.
- B. It uses OSI Layer 2 and both the primary/secondary devices send data based on a matching token ring.
- C. It uses OSI Layer 2 and the secondary device sends data based on request from primary device.
- D. It uses OSI Layer 2 and both the primary/secondary devices always send data during the communication.
正解: C
質問 23
Which three common breach points can be found in a typical OT environment? (Choose three.)
- A. Global hat
- B. RTU exploits
- C. Black hat
- D. VLAN exploits
- E. Hard hat
正解: B,C,D
質問 24
An OT administrator deployed many devices to secure the OT network. However, the SOC team is reporting that there are too many alerts, and that many of the alerts are false positive. The OT administrator would like to find a solution that eliminates repetitive tasks, improves efficiency, saves time, and saves resources.
Which products should the administrator deploy to address these issues and automate most of the manual tasks done by the SOC team?
- A. FortiSIEM and FortiManager
- B. A syslog server and FortiSIEM
- C. FortiSandbox and FortiSIEM
- D. FortiSOAR and FortiSIEM
正解: D
質問 25
Refer to the exhibit.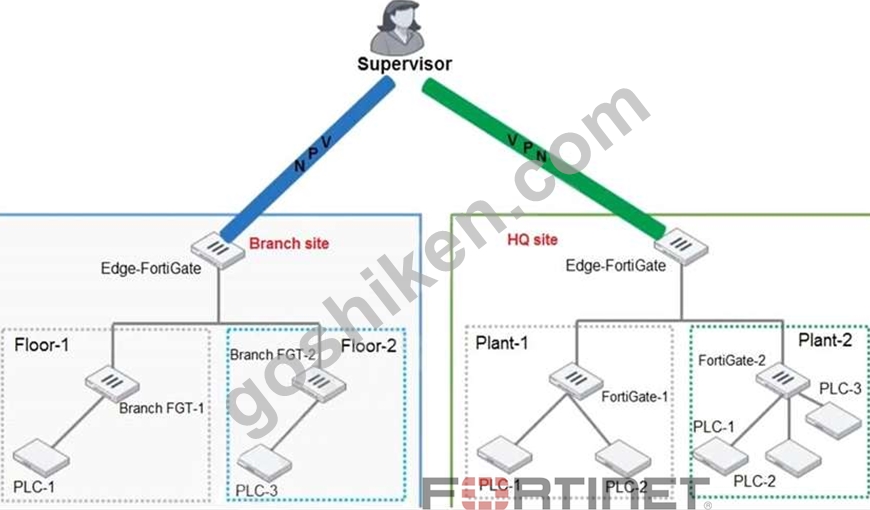
You need to configure VPN user access for supervisors at the breach and HQ sites using the same soft FortiToken. Each site has a FortiGate VPN gateway.
What must you do to achieve this objective?
- A. You must register the same FortiToken on more than one FortiGate.
- B. You must use the user self-registration server.
- C. You must use a FortiAuthenticator.
- D. You must use a third-party RADIUS OTP server.
正解: C
質問 26
Refer to the exhibit and analyze the output.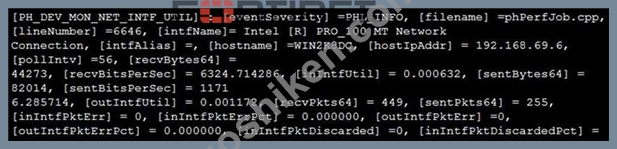
Which statement about the output is true?
- A. This is a sample of FortiGate interface statistics.
- B. This is a sample of an SNMP temperature control event log.
- C. This is a sample of a PAM event type.
- D. This is a sample of a FortiAnalyzer system interface event log.
正解: D
質問 27
Refer to the exhibit.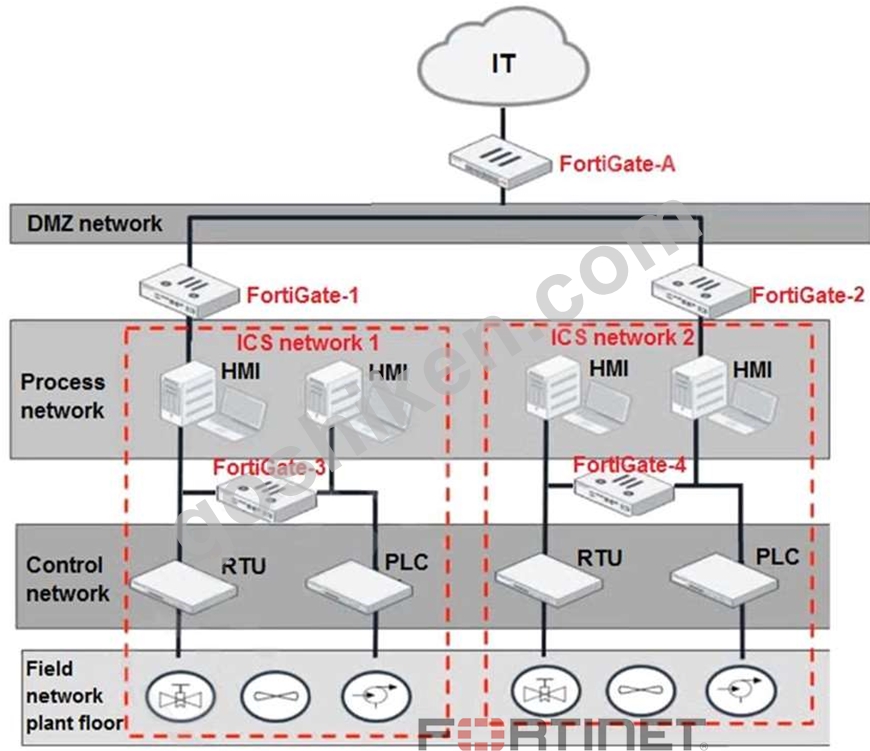
Based on the topology designed by the OT architect, which two statements about implementing OT security are true? (Choose two.)
- A. IT and OT networks are separated by segmentation.
- B. Micro-segmentation can be achieved only by replacing FortiGate-3 and FortiGate-4 with a pair of FortiSwitch devices.
- C. FortiGate-3 and FortiGate-4 devices must be in a transparent mode.
- D. Firewall policies should be configured on FortiGate-3 and FortiGate-4 with industrial protocol sensors.
正解: A,C
質問 28
You are investigating a series of incidents that occurred in the OT network over past 24 hours in FortiSIEM.
Which three FortiSIEM options can you use to investigate these incidents? (Choose three.)
- A. Overview
- B. Security
- C. List
- D. Risk
- E. IPS
正解: A,C,D
質問 29
Which three methods of communication are used by FortiNAC to gather visibility information? (Choose three.)
- A. SNMP
- B. RADIUS
- C. TACACS
- D. API
- E. ICMP
正解: A,B,D
質問 30
An OT network architect needs to secure control area zones with a single network access policy to provision devices to any number of different networks.
On which device can this be accomplished?
- A. FortiNAC
- B. FortiEDR
- C. FortiSwitch
- D. FortiGate
正解: A
質問 31
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
- A. Each playbook can include multiple triggers.
- B. You cannot use Windows and Linux hosts security events with FortiSoC.
- C. You can automate SOC tasks through playbooks.
- D. You must set correct operator in event handler to trigger an event.
正解: A,C
解説:
Ref: https://docs.fortinet.com/document/fortianalyzer/7.0.0/administration-guide/268882/fortisoc
質問 32
What are two benefits of a Nozomi integration with FortiNAC? (Choose two.)
- A. Enhanced point of connection details
- B. Adapter consolidation for multi-adapter hosts
- C. Direct VLAN assignment
- D. Importation and classification of hosts
正解: A,C
質問 33
Refer to the exhibit.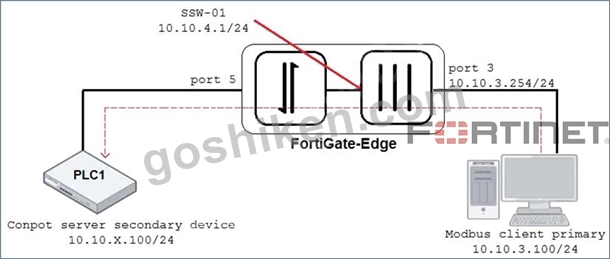
An OT architect has implemented a Modbus TCP with a simulation server Conpot to identify and control the Modus traffic in the OT network. The FortiGate-Edge device is configured with a software switch interface ssw-01.
Based on the topology shown in the exhibit, which two statements about the successful simulation of traffic between client and server are true? (Choose two.)
- A. Port5 is not a member of the software switch.
- B. NAT is disabled in the FortiGate firewall policy from port3 to ssw-01.
- C. The FortiGate-Edge device must be in NAT mode.
- D. The FortiGate devices is in offline IDS mode.
正解: C,D
質問 34
......
Fortinet NSE7_OTS-6.4 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
検証済み材料を使うならまずNSE7_OTS-6.4テストエンジンを試そう:https://www.goshiken.com/Fortinet/NSE7_OTS-6.4-mondaishu.html
