2023年10月最新のCyberArk PAM-DEF問題集で更新された180問あります
PDF無料ダウンロードにはPAM-DEF有効な練習テスト問題
CyberArk PAM-DEF認定は、業界で高く評価され、CyberArk PAMソリューションの専門知識の基準として認められています。これは、特権アクセス管理に特化したセキュリティ専門家が、組織の重要な資産を保護するために必要な認定です。CyberArk PAM-DEF認定試験に合格することで、候補者は潜在的な雇用主に自分の知識とスキルを証明し、サイバーセキュリティの分野で新しいキャリアの機会を得ることができます。
サイバーアーク・ディフェンダー - PAM認定試験は、アイデンティティとアクセス管理、認証と認可、監査とログ記録、セキュリティポリシーとコンプライアンスなど、PAMに関連する様々なトピックをカバーした包括的なテストです。この試験は、様々な環境でサイバーアークのPAMソリューションを展開、設定、管理する能力をテストするように設計されています。
CyberArk PAM-DEF(CyberArk Defender - PAM)試験は、特権アカウントのセキュリティを確保し、機密データを保護するために必要な高度なスキルを学びたいサイバーセキュリティ専門家向けの認定プログラムです。この認定は、特権アクセス管理(PAM)に関する産業界で最も権威ある信頼できる資格の1つとして認められています。
質問 # 49
Which Automatic Remediation is configurable for a PTA detection of a "Suspected Credential Theft"?
- A. Reconcile Credentials
- B. Rotate Credentials
- C. Disable Account
- D. Add to Pending
正解:A
質問 # 50
Can the 'Connect' button be used to initiate an SSH connection, as root, to a Unix system when SSH access for root is denied?
- A. Yes, only if a logon account is associated with the root account and the user connects through the PSM-SSH connection component.
- B. No, it is not possible.
- C. Yes, if a logon account is associated with the root account.
- D. Yes, when using the connect button, CyberArk uses the PMTerminal.exe process which bypasses the root SSH restriction.
正解:A
質問 # 51
It is possible to restrict the time of day, or day of week that a [b]verify[/b] process can occur
- A. TRUE
- B. FALSE
正解:A
質問 # 52
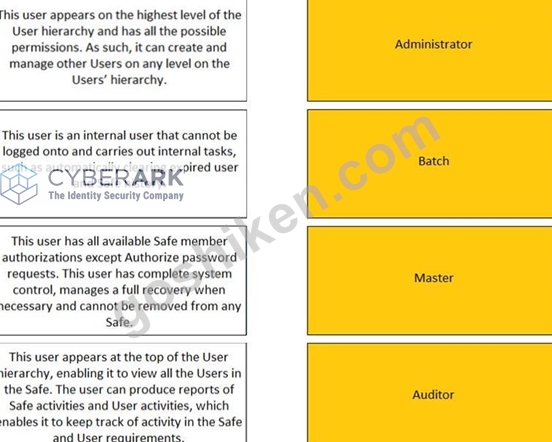
Match the built-in Vault User with the correct definition.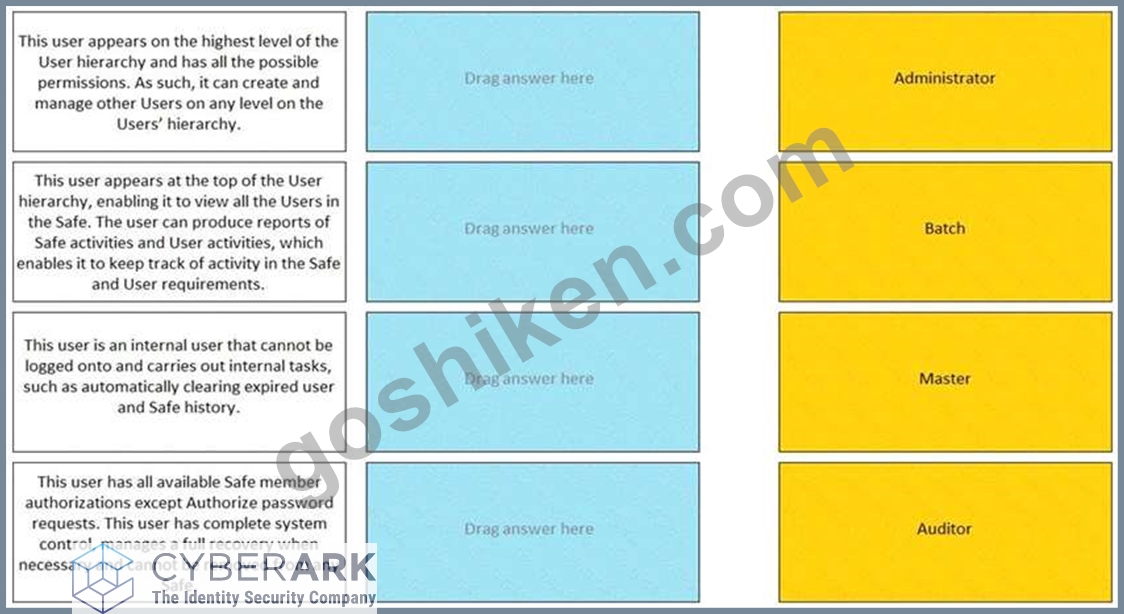
正解:
解説: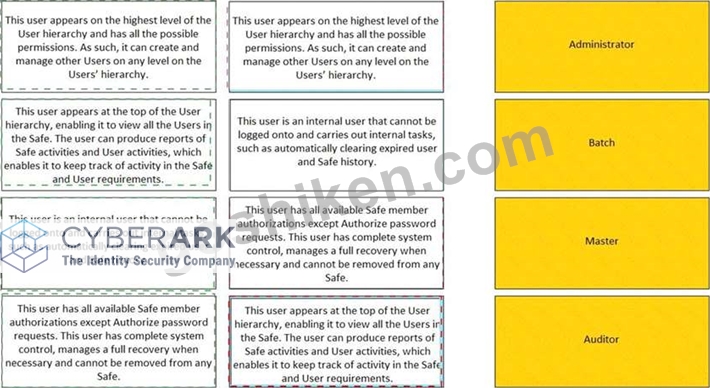
質問 # 53
A Vault Administrator team member can log in to CyberArk, but for some reason, is not given Vault Admin rights.
Where can you check to verify that the Vault Admins directory mapping points to the correct AD group?
- A. PVWA > User Provisioning > LDAP Integration > Map Name
- B. PVWA > Administration > LDAP Integration > AD Groups
- C. PVWA > User Provisioning > LDAP Integration > Mapping Criteria
- D. PVWA > Administration > LDAP Integration > Mappings
正解:D
質問 # 54
Users are unable to launch Web Type Connection components from the PSM server. Your manager asked you to open the case with CyberArk Support.
Which logs will help the CyberArk Support Team debug the issue? (Choose three.)
- A. PSMDebug.log
- B. PSMConsole.log
- C. PSMTrace.log
- D. PMconsole.log
- E. <Session_ID>.Component.log
- F. ITAlog.log
正解:A、C、F
質問 # 55
It is possible to control the hours of the day during which a user may log into the vault.
- A. TRUE
- B. FALSE
正解:A
質問 # 56
A user requested access to view a password secured by dual-control and is unsure who to contact to expedite the approval process. The Vault Admin has been asked to look at the account and identify who can approve their request.
What is the correct location to identify users or groups who can approve?
- A. PrivateArk > Admin Tools > Users and Groups > Auditors (Group Membership)
- B. PVWA> Policies > Access Control (Safes) > Safe Members > Workflow > Authorize Password Requests
- C. PVWA> Account List > Edit > Show Advanced Settings > Dual Control > Direct Managers
- D. PVWA> Administration > Platform Configuration > Edit Platform > UI & Workflow > Dual Control> Approvers
正解:B
質問 # 57
Within the Vault each password is encrypted by:
- A. its own unique key
- B. the server key
- C. the recovery private key
- D. the recovery public key
正解:A
質問 # 58
You are creating a shared safe for the help desk.
What must be considered regarding the naming convention?
- A. Safe owners should determine the safe name to enable them to easily remember it.
- B. Ensure your naming convention is no longer than 20 characters.
- C. Combine environments, owners and platforms to minimize the total number of safes created.
- D. The use of these characters V:*<>".| is not allowed.
正解:D
質問 # 59
Which type of automatic remediation can be performed by the PTA in case of a suspected credential theft security event?
- A. Password change
- B. Password reconciliation
- C. Session suspension
- D. Session termination
正解:A
質問 # 60
Which keys are required to be present in order to start the PrivateArk Server service?
- A. Recovery private key
- B. Server key
- C. Safe key
- D. Recovery public key
正解:B、D
質問 # 61
Which report could show all accounts that are past their expiration dates?
- A. Privileged Account Inventory report
- B. Application Inventory report
- C. Activity log
- D. Privileged Account Compliance Status report
正解:D
質問 # 62
You are creating a Dual Control workflow for a team's safe.
Which safe permissions must you grant to the Approvers group?
- A. List accounts, Unlock accounts
- B. Retrieve accounts, Access Safe without confirmation
- C. Retrieve accounts, Authorize account request
- D. List accounts, Authorize account request
正解:C
質問 # 63
PTA can automatically suspend sessions if suspicious activities are detected in a privileged session, but only if the session is made via the CyberArk PSM.
- A. True
- B. False, the PTA can suspend sessions whether the session is made via the PSM or not
正解:B
質問 # 64
CyberArk recommends implementing object level access control on all Safes.
- A. True
- B. False
正解:B
質問 # 65
Which service should NOT be running on the DR Vault when the primary Production Vault is up?
- A. CyberArk Logical Container
- B. PrivateArk Database
- C. PrivateArk Server
- D. CyberArk Vault Disaster Recovery (DR) service
正解:C
質問 # 66
What is the maximum number of levels of authorization you can set up in Dual Control?
- A. 0
- B. 1
- C. 2
- D. 3
正解:C
質問 # 67
To enable the Automatic response "Add to Pending" within PTA when unmanaged credentials are found, what are the minimum permissions required by PTAUser for the PasswordManager_pending safe?
- A. Add accounts (includes update properties), Update Account content, Update Account properties, View Audit
- B. List Accounts, Add accounts (includes update properties), Delete Accounts, Manage Safe
- C. List Accounts, View Safe members, Add accounts (includes update properties), Update Account content, Update Account properties
- D. View Accounts, Update Account content, Update Account properties, Access Safe without confirmation, Manage Safe, View Audit
正解:C
質問 # 68
For a safe with Object Level Access enabled you can turn off Object Level Access Control when it no longer needed on the safe.
- A. TRUE
- B. FALSE
正解:B
質問 # 69
VAULT authorizations may be granted to_____.
- A. LDAP Users
- B. LDAP Groups
- C. Vault Groups
- D. Vault Users
正解:A、D
質問 # 70
......
PAM-DEFテストエンジンお試しセット、PAM-DEF問題集PDF:https://www.goshiken.com/CyberArk/PAM-DEF-mondaishu.html
最新のCyberArk PAM-DEFのPDFと問題集で(2023)無料試験問題解答はここ:https://drive.google.com/open?id=1UYD8Oj7SjIMRl27ENPp4rOoAj2PH9OtH
