検証済みPCCET問題集と解答で2023年最新のPCCETをダウンロード
更新された100%カバー率リアルPCCET試験問題で100%合格保証付いてます
PCCET試験に合格することは、就職先の見込みの増加、高い給与、そしてより高い職場の安定性など、さまざまな利点を提供します。この認定は、個人がサイバー脅威から組織の情報や資産を保護するために必要な知識とスキルを持っていることを雇用主に示し、サイバーセキュリティ分野への献身と努力を認めています。
Palo Alto Networks PCCETは、サイバーセキュリティ技術者の初心者向けの認定試験であり、この分野での知識とスキルを証明したい人に設計されています。この試験は、世界中の組織にサイバーセキュリティソリューションを提供するリーディング企業であるPalo Alto Networksによって提供されます。この試験に合格すると、個人はサイバーセキュリティの分野での能力を証明する資格を取得することができます。
質問 # 11
Which three services are part of Prisma SaaS? (Choose three.)
- A. Threat Prevention
- B. Data Exposure Control
- C. DevOps
- D. Data Loss Prevention
- E. Denial of Service
正解:A、B、D
質問 # 12
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
- A. National security information
- B. Credit card number
- C. A symmetric encryption key
- D. Trade secret
正解:B
質問 # 13
Data Loss Prevention (DLP) and Cloud Access Security Broker (CASB) fall under which Prisma access service layer?
- A. Security
- B. Cloud
- C. Management
- D. Network
正解:A
解説:
Explanation
A SASE solution converges networking and security services into one unified, cloud-delivered solution (see Figure 3-12) that includes the following:
Networking
Software-defined wide-area networks (SD-WANs)
Virtual private networks (VPNs)
Zero Trust network access (ZTNA)
Quality of Service (QoS)
Security
Firewall as a service (FWaaS)
Domain Name System (DNS) security
Threat prevention
Secure web gateway (SWG)
Data loss prevention (DLP)
Cloud access security broker (CASB)
質問 # 14
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
- A. Accessibility
- B. Business
- C. Processes
- D. People
- E. Understanding
正解:B、C、D
解説:
Explanation
質問 # 15
Which technique changes protocols at random during a session?
- A. use of non-standard ports
- B. tunneling within commonly used services
- C. hiding within SSL encryption
- D. port hopping
正解:D
質問 # 16
Which native Windows application can be used to inspect actions taken at a specific time?
- A. Task Manager
- B. Timeline inspector
- C. Event Viewer
- D. Task Scheduler
正解:C
質問 # 17
If an endpoint does not know how to reach its destination, what path will it take to get there?
- A. The endpoint will broadcast to all connected network devices.
- B. The endpoint will send data to the specified default gateway.
- C. The endpoint will forward data to another endpoint to send instead.
- D. The endpoint will not send the traffic until a path is clarified.
正解:B
質問 # 18
Which statement describes DevOps?
- A. DevOps is a set of tools that assists the Development and Operations teams throughout the software delivery process
- B. DevOps is its own separate team
- C. DevOps is a culture that unites the Development and Operations teams throughout the software delivery process
- D. DevOps is a combination of the Development and Operations teams
正解:C
解説:
DevOps is not:
* A combination of the Dev and Ops teams: There still are two teams; they just operate in a communicative, collaborative way.
* Its own separate team: There is no such thing as a "DevOps engineer." Although some companies may appoint a "DevOps team" as a pilot when trying to transition to a DevOps culture, DevOps refers to a culture where developers, testers, and operations personnel cooperate throughout the entire software delivery lifecycle.
* A tool or set of tools: Although there are tools that work well with a DevOps model or help promote DevOps culture, DevOps ultimately is a strategy, not a tool.
* Automation: Although automation is very important for a DevOps culture, it alone does not define DevOps.
質問 # 19
Which type of Software as a Service (SaaS) application provides business benefits, is fast to deploy, requires minimal cost and is infinitely scalable?
- A. Tolerated
- B. Sanctioned
- C. Benign
- D. Secure
正解:B
質問 # 20
Which security component can detect command-and-control traffic sent from multiple endpoints within a corporate data center?
- A. Next-generation firewall
- B. Stateless firewall
- C. Port-based firewall
- D. Personal endpoint firewall
正解:A
質問 # 21
Which of the following is an AWS serverless service?
- A. Kappa
- B. Delta
- C. Beta
- D. Lambda
正解:D
解説:
Examples of serverless environments include Amazon Lambda and Azure Functions. Many PaaS offerings, such as Pivotal Cloud Foundry, also are effectively serverless even if they have not historically been marketed as such. Although serverless may appear to lack the container-specific, cloud native attribute, containers are extensively used in the underlying implementations, even if those implementations are not exposed to end users directly.
質問 # 22
Which of the following is a service that allows you to control permissions assigned to users in order for them to access and utilize cloud resources?
- A. Identity and Access Management (IAM)
- B. Lightweight Directory Access Protocol (LDAP)
- C. User-ID
- D. User and Entity Behavior Analytics (UEBA)
正解:A
解説:
Identity and access management (IAM) is a software service or framework that allows organizations to define user or group identities within software environments, then associate permissions with them. The identities and permissions are usually spelled out in a text file, which is referred to as an IAM policy.
質問 # 23
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
- A. control and protect inter-host traffic using routers configured to use the Border Gateway Protocol (BGP) dynamic routing protocol
- B. control and protect inter-host traffic by using IPv4 addressing
- C. control and protect inter-host traffic using physical network security appliances
- D. control and protect inter-host traffic by exporting all your traffic logs to a sysvol log server using the User Datagram Protocol (UDP)
正解:C
解説:
page 211 "Consolidating servers within trust levels: Organizations often consolidate servers within the same trust level into a single virtual computing environment: ... ... ... This virtual systems capability enables a single physical device to be used to simultaneously meet the unique requirements of multiple VMs or groups of VMs. Control and protection of inter-host traffic with physical network security appliances that are properly positioned and configured is the primary security focus."
質問 # 24
Match the Identity and Access Management (IAM) security control with the appropriate definition.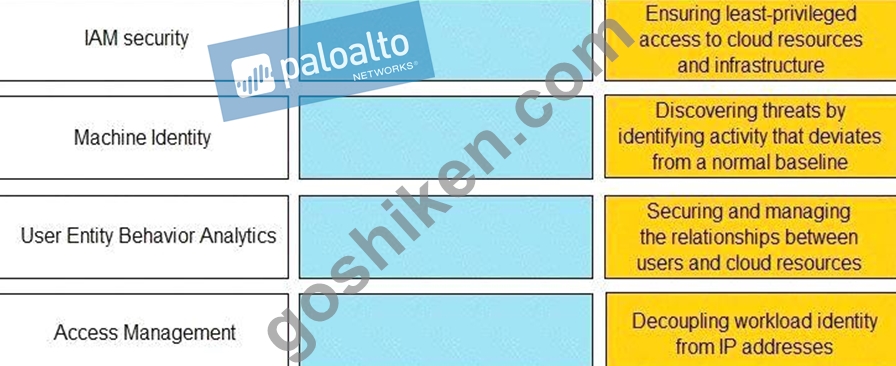
正解:
解説: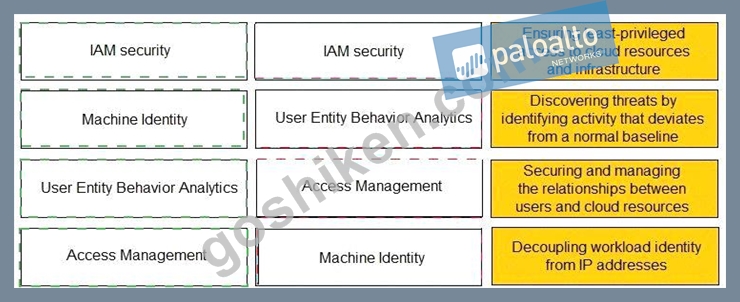
質問 # 25
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
- A. Static
- B. Dynamic
- C. Bare-metal
- D. Pre-exploit protection
正解:B
解説:
Explanation
The WildFire cloud-based malware analysis environment is a cyber threat prevention service that identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment.
質問 # 26
Which activities do local organization security policies cover for a SaaS application?
- A. how the data is backed up in one or more locations
- B. how the application can be used
- C. how the application processes the data
- D. how the application can transit the Internet
正解:B
質問 # 27
In which two cloud computing service models are the vendors responsible for vulnerability and patch management of the underlying operating system? (Choose two.)
- A. PaaS
- B. SaaS
- C. On-premises
- D. IaaS
正解:A、B
質問 # 28
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
- A. NetOps
- B. DevOps
- C. SecOps
- D. SecDevOps
正解:C
解説:
Explanation
Security operations (SecOps) is a necessary function for protecting the digital way of life, for global businesses and customers. SecOps requires continuous improvement in operations to handle fast-evolving threats. SecOps needs to arm security operations professionals with high-fidelity intelligence, contextual data, and automated prevention workflows to quickly identify and respond to these threats. SecOps must leverage automation to reduce strain on analysts and execute the Security Operation Center's (SOC) mission to identify, investigate, and mitigate threats.
質問 # 29
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
- A. NetOps
- B. DevOps
- C. SecOps
- D. SecDevOps
正解:C
質問 # 30
Which of the following is an AWS serverless service?
- A. Kappa
- B. Delta
- C. Beta
- D. Lambda
正解:D
解説:
Explanation
Examples of serverless environments include Amazon Lambda and Azure Functions. Many PaaS offerings, such as Pivotal Cloud Foundry, also are effectively serverless even if they have not historically been marketed as such. Although serverless may appear to lack the container-specific, cloud native attribute, containers are extensively used in the underlying implementations, even if those implementations are not exposed to end users directly.
質問 # 31
Match the IoT connectivity description with the technology.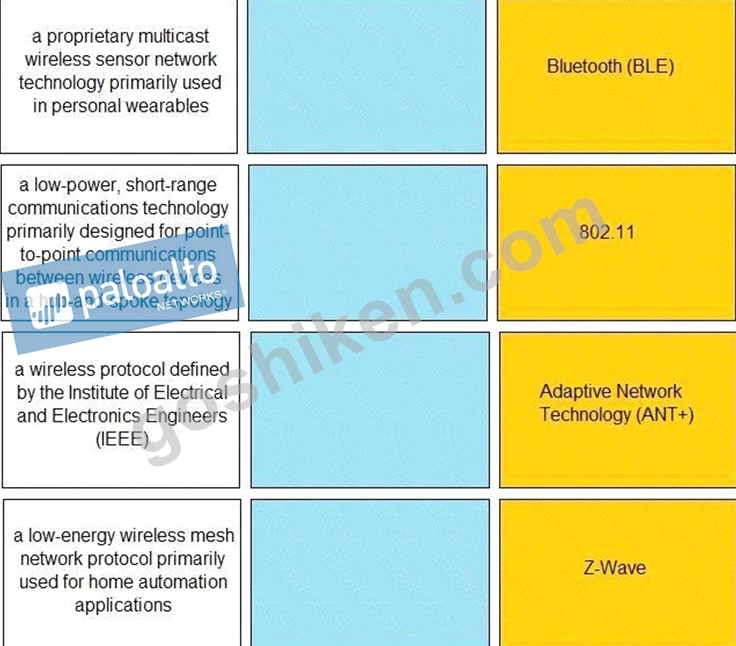
正解:
解説: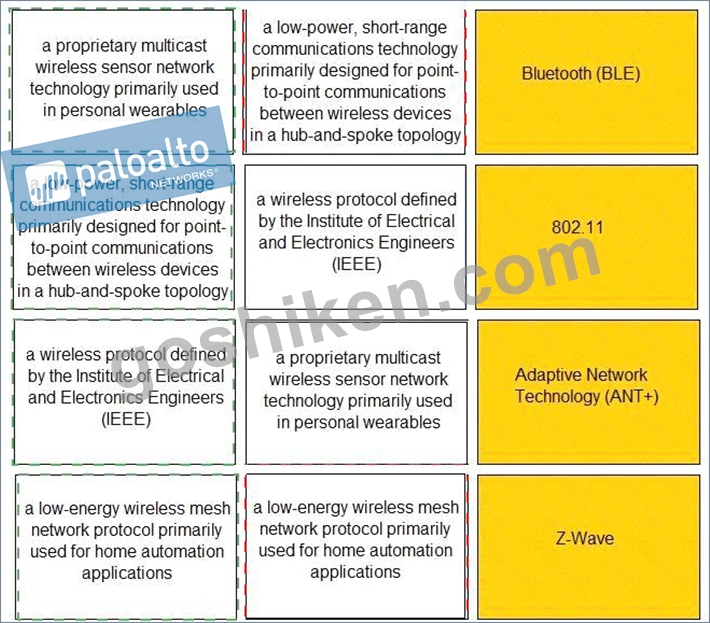
Explanation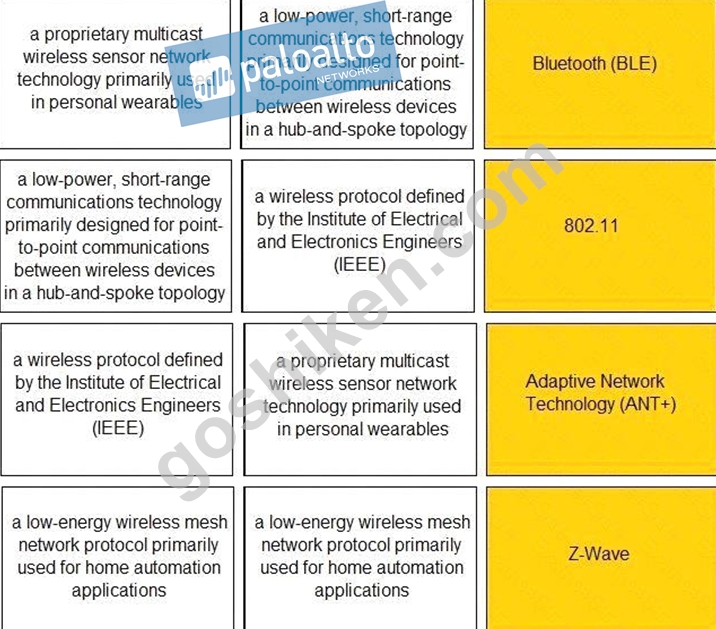
Short-range wireless:
Adaptive Network Technology+ (ANT+): ANT+ is a proprietary multicast wireless sensor network technology primarily used in personal wearables, such as sports and fitness sensors.
Bluetooth/Bluetooth Low-Energy (BLE): Bluetooth is a low-power, short-range communications technology primarily designed for point-to-point communications between wireless devices in a hub-and-spoke topology. BLE (also known as Bluetooth Smart or Bluetooth 4.0+) devices consume significantly less power than Bluetooth devices and can access the internet directly through 6LoWPAN connectivity.
Internet Protocol version 6 (IPv6) over Low-Power Wireless Personal Area Networks (6LoWPAN): 6LoWPAN allows IPv6 traffic to be carried over low-power wireless mesh networks. 6LoWPAN is designed for nodes and applications that require wireless internet connectivity at relatively low data rates in small form factors, such as smart light bulbs and smart meters.
Wi-Fi/802.11: The Institute of Electrical and Electronics Engineers (IEEE) defines the 802 LAN protocol standards. 802.11 is the set of standards used for Wi-Fi networks typically operating in the 2.4GHz and 5GHz frequency bands. The most common implementations today include:
802.11n (labeled Wi-Fi 4 by the Wi-Fi Alliance), which operates on both 2.4GHz and 5GHz bands at ranges from 54Mbps to 600Mbps
802.11ac (Wi-Fi 5), which operates on the 5GHz band at ranges from 433Mbps to 3.46 Gbps
802.11ax (Wi-Fi 6), which operates on the 2.4GHz and 5GHz bands (and all bands between 1 and 6GHz, when they become available for 802.11 use) at ranges up to 11Gbps Z-Wave: Z-Wave is a low-energy wireless mesh network protocol primarily used for home automation applications such as smart appliances, lighting control, security systems, smart thermostats, windows and locks, and garage doors.
Zigbee/802.14: Zigbee is a low-cost, low-power wireless mesh network protocol based on the IEEE 802.15.4 standard. Zigbee is the dominant protocol in the low-power networking market, with a large installed base in industrial environments and smart home products.
質問 # 32
......
リアル問題集で100%無料PCCET試験問題集を試そう:https://www.goshiken.com/Palo-Alto-Networks/PCCET-mondaishu.html
実際のPCCET問題集最新練習テスト問題集:https://drive.google.com/open?id=1DeY6MDtQseH76RThMDs3FzGnaU0EnkoP
