(2022)PCCET問題集と練習テスト(77問題)
ガイド(2022年最新)リアルなPalo Alto Networks PCCET試験問題
質問 32
In addition to integrating the network and endpoint components, what other component does Cortex integrate to speed up IoC investigations?
- A. Infrastructure
- B. Cloud
- C. Switch
- D. Computer
正解: A
質問 33
Which tool supercharges security operations center (SOC) efficiency with the world's most comprehensive operating platform for enterprise security?
- A. Prisma SAAS
- B. Cortex XDR
- C. WildFire
- D. Cortex XSOAR
正解: D
質問 34
Which two network resources does a directory service database contain? (Choose two.)
- A. Terminal shell types on endpoints
- B. Services
- C. /etc/shadow files
- D. Users
正解: B,D
質問 35
Data Loss Prevention (DLP) and Cloud Access Security Broker (CASB) fall under which Prisma access service layer?
- A. Cloud
- B. Network
- C. Management
- D. Security
正解: D
質問 36
Given the graphic, match each stage of the cyber-attack lifecycle to its description.
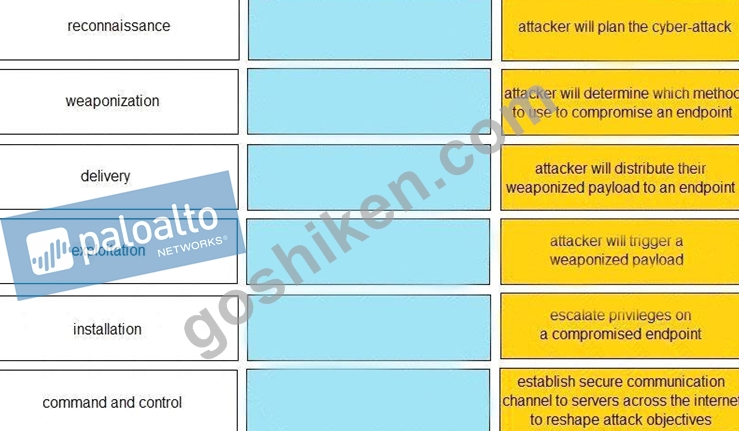
正解:
解説: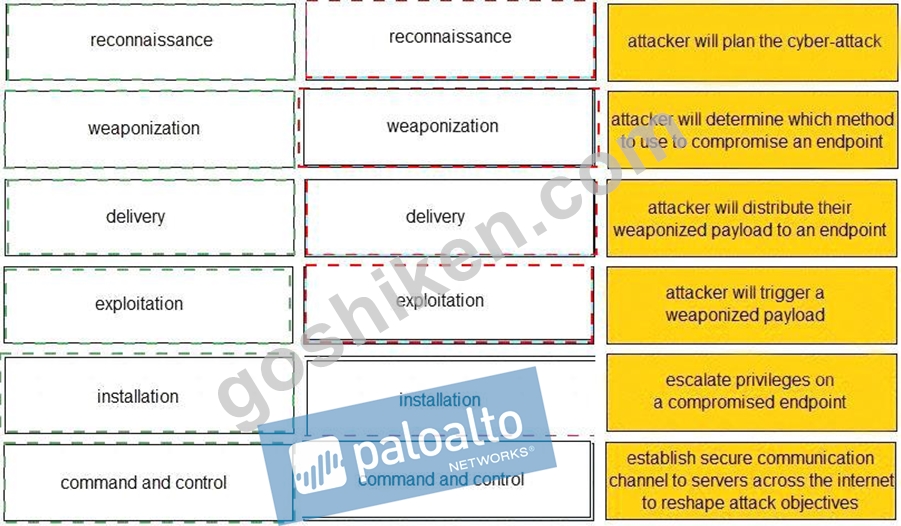
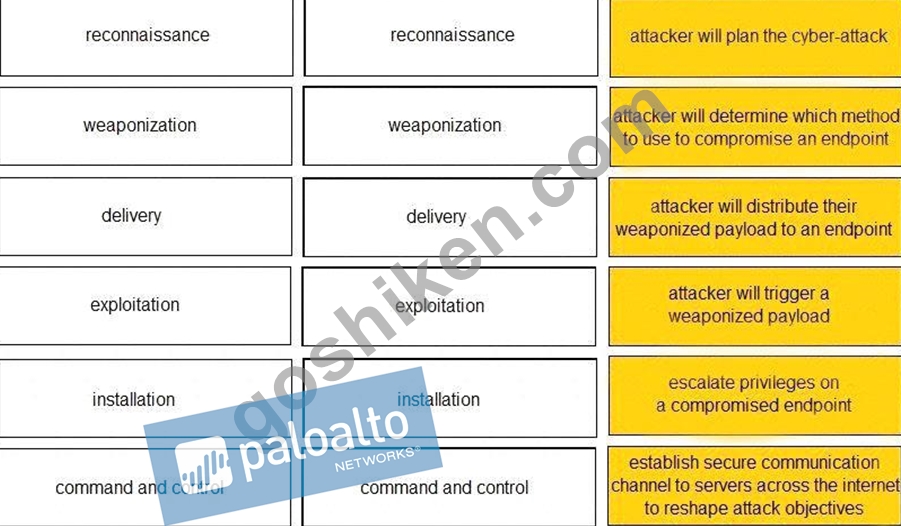
質問 37
Which term describes data packets that move in and out of the virtualized environment from the host network or a corresponding traditional data center?
- A. Interzone traffic
- B. Intrazone traffic
- C. East-West traffic
- D. North-South traffic
正解: D
質問 38
In SecOps, what are two of the components included in the identify stage? (Choose two.)
- A. Initial Research
- B. Change Control
- C. Content Engineering
- D. Breach Response
正解: A,C
質問 39
Which statement describes DevOps?
- A. DevOps is a combination of the Development and Operations teams
- B. DevOps is a culture that unites the Development and Operations teams throughout the software delivery process
- C. DevOps is its own separate team
- D. DevOps is a set of tools that assists the Development and Operations teams throughout the software delivery process
正解: D
質問 40
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
- A. SecDevOps
- B. DevOps
- C. NetOps
- D. SecOps
正解: D
質問 41
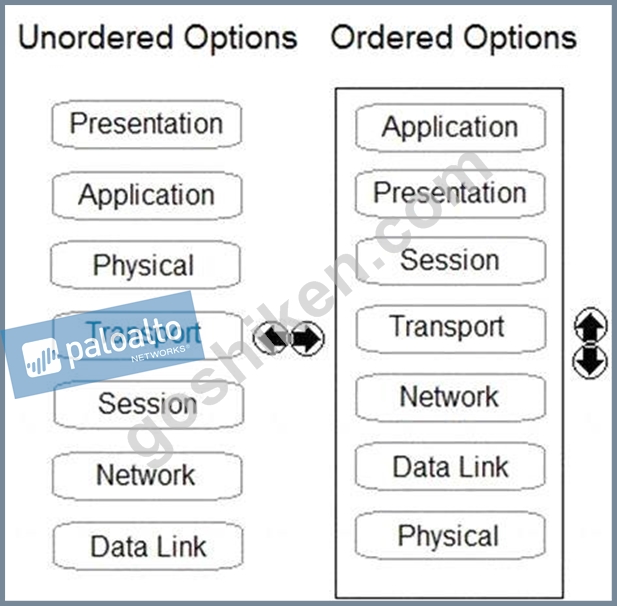
Order the OSI model with Layer7 at the top and Layer1 at the bottom.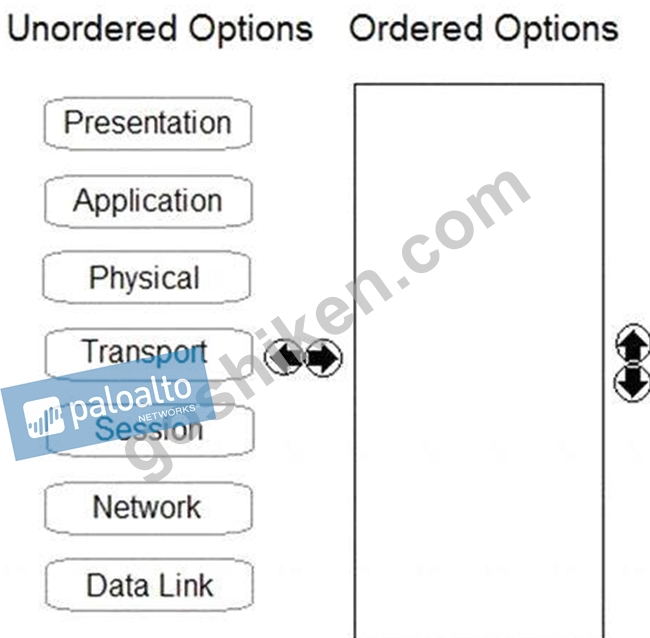
正解:
解説: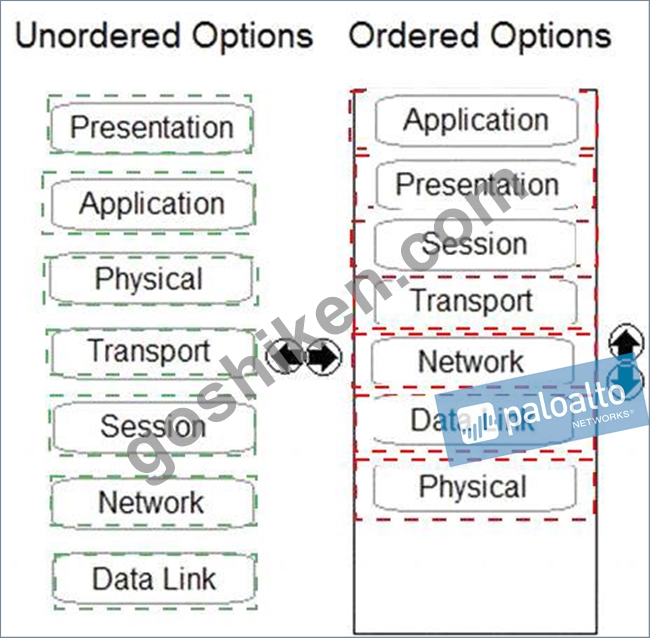
質問 42
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
- A. AutoFocus
- B. MineMeld
- C. WildFire
- D. Cortex XDR
正解: D
質問 43
When signature-based antivirus software detects malware, what three things does it do to provide protection?
(Choose three.)
- A. alert system administrators
- B. delete the infected file
- C. remove the infected file's extension
- D. quarantine the infected file
- E. decrypt the infected file using base64
正解: B,C,D
解説:
Explanation
質問 44
When signature-based antivirus software detects malware, what three things does it do to provide protection?
(Choose three.)
- A. alert system administrators
- B. delete the infected file
- C. remove the infected file's extension
- D. quarantine the infected file
- E. decrypt the infected file using base64
正解: B,C,D
質問 45
Routing Information Protocol (RIP), uses what metric to determine how network traffic should flow?
- A. Split Horizon
- B. Path Vector
- C. Shortest Path
- D. Hop Count
正解: D
質問 46
Which subnet does the host 192.168.19.36/27 belong?
- A. 192.168.19.32
- B. 192.168.19.64
- C. 192.168.19.16
- D. 192.168.19.0
正解: A
質問 47
Which characteristic of serverless computing enables developers to quickly deploy application code?
- A. Using cloud service spot pricing to reduce the cost of using virtual machines to run their application code
- B. Using Container as a Service (CaaS) to deploy application containers to run their code.
- C. Uploading cloud service autoscaling services to deploy more virtual machines to run their application code based on user demand
- D. Uploading the application code itself, without having to provision a full container image or any OS virtual machine components
正解: C
質問 48
Which endpoint tool or agent can enact behavior-based protection?
- A. DNS Security
- B. AutoFocus
- C. MineMeld
- D. Cortex XDR
正解: D
質問 49
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
- A. Credit card number
- B. A symmetric encryption key
- C. Trade secret
- D. National security information
正解: A
解説:
Explanation/Reference:
質問 50
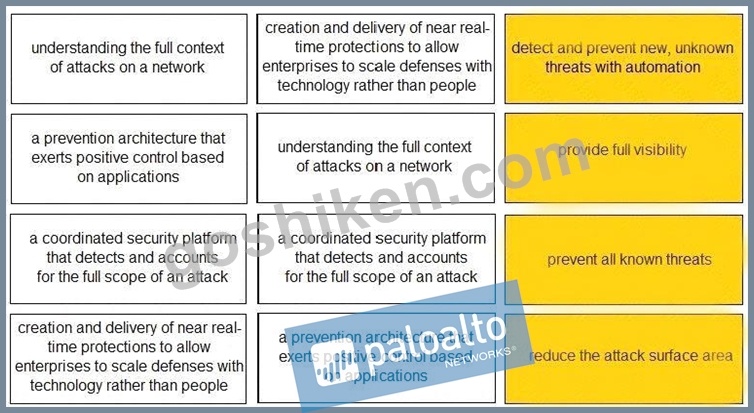
Match each description to a Security Operating Platform key capability.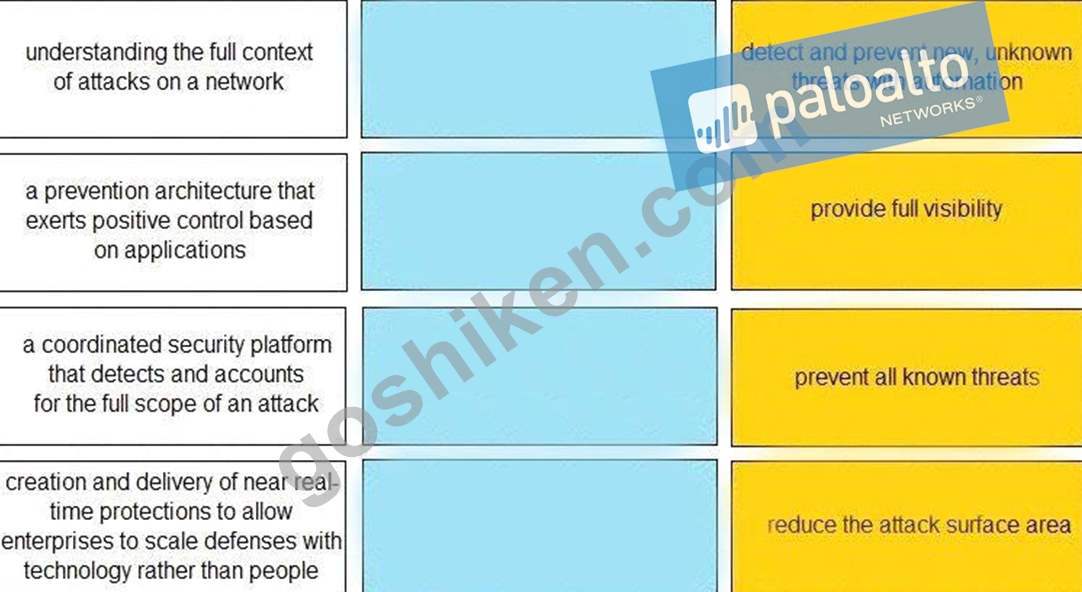
正解:
解説: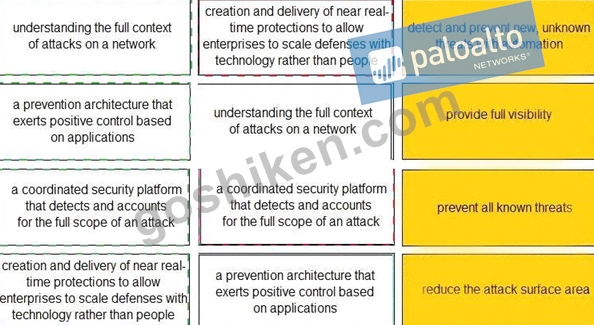
質問 51
In which step of the cyber-attack lifecycle do hackers embed intruder code within seemingly innocuous files?
- A. exploitation
- B. weaponization
- C. reconnaissance
- D. delivery
正解: D
質問 52
Which IPsec feature allows device traffic to go directly to the Internet?
- A. d.Authentication Header (AH)
- B. Diffie-Hellman groups
- C. IKE Security Association
- D. Split tunneling
正解: D
質問 53
What is the key to "taking down" a botnet?
- A. install openvas software on endpoints
- B. prevent bots from communicating with the C2
- C. use LDAP as a directory service
- D. block Docker engine software on endpoints
正解: B
質問 54
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
- A. Pre-exploit protection
- B. Dynamic
- C. Static
- D. Bare-metal
正解: B
質問 55
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
- A. People
- B. Processes
- C. Understanding
- D. Business
- E. Accessibility
正解: A,B,D
質問 56
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
- A. control and protect inter-host traffic using routers configured to use the Border Gateway Protocol (BGP) dynamic routing protocol
- B. control and protect inter-host traffic using physical network security appliances
- C. control and protect inter-host traffic by exporting all your traffic logs to a sysvol log server using the User Datagram Protocol (UDP)
- D. control and protect inter-host traffic by using IPv4 addressing
正解: B
質問 57
......
PCCET試験問題集パスできる2022年最新の認証された試験問題:https://www.goshiken.com/Palo-Alto-Networks/PCCET-mondaishu.html
PCCET試験問題リアルな最新問題PDF:https://drive.google.com/open?id=1DeY6MDtQseH76RThMDs3FzGnaU0EnkoP
