[2023年最新] 高合格率なPCCETテストアンサーかつPalo Alto Networks PCCETテストPDF
完璧PCCET問題集試験問題と解答でパス保証されます
質問 # 48
Match the Palo Alto Networks WildFire analysis verdict with its definition.
正解:
解説: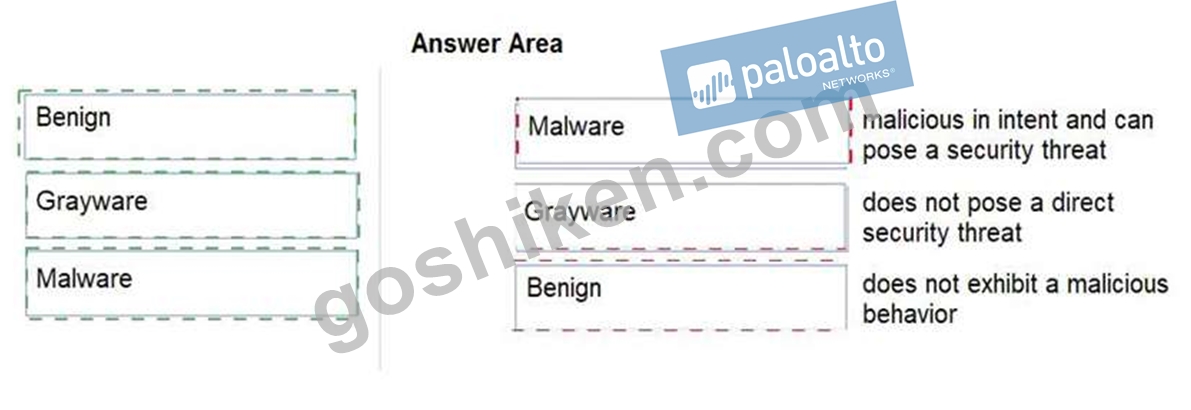
Explanation
Benign: Safe and does not exhibit malicious behavior
Grayware: No security risk but might display obtrusive behavior (for example, adware, spyware, and browser helper objects) Malware: Malicious in nature and intent and can pose a security threat (for example, viruses, worms, trojans, root kits, botnets, and remote-access toolkits) Phishing: Malicious attempt to trick the recipient into revealing sensitive data
質問 # 49
Which network firewall operates up to Layer 4 (Transport layer) of the OSI model and maintains information about the communication sessions which have been established between hosts on trusted and untrusted networks?
- A. Group policy
- B. Stateless
- C. Stateful
- D. Static packet-filter
正解:C
質問 # 50
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
- A. National security information
- B. Trade secret
- C. Credit card number
- D. A symmetric encryption key
正解:C
質問 # 51
Which two network resources does a directory service database contain? (Choose two.)
- A. Terminal shell types on endpoints
- B. /etc/shadow files
- C. Users
- D. Services
正解:C、D
解説:
Explanation
A directory service is a database that contains information about users, resources, and services in a network.
質問 # 52
In which situation would a dynamic routing protocol be the quickest way to configure routes on a router?
- A. the network is small
- B. the network needs backup routes
- C. the network is large
- D. the network has low bandwidth requirements
正解:C
解説:
Explanation
A static routing protocol requires that routes be created and updated manually on a router or other network device. If a static route is down, traffic can't be automatically rerouted unless an alternate route has been configured. Also, if the route is congested, traffic can't be automatically rerouted over the less congested alternate route. Static routing is practical only in very small networks or for very limited, special-case routing scenarios (for example, a destination that's used as a backup route or is reachable only via a single router).
However, static routing has low bandwidth requirements (routing information isn't broadcast across the network) and some built-in security (users can route only to destinations that are specified in statically defined routes).
質問 # 53
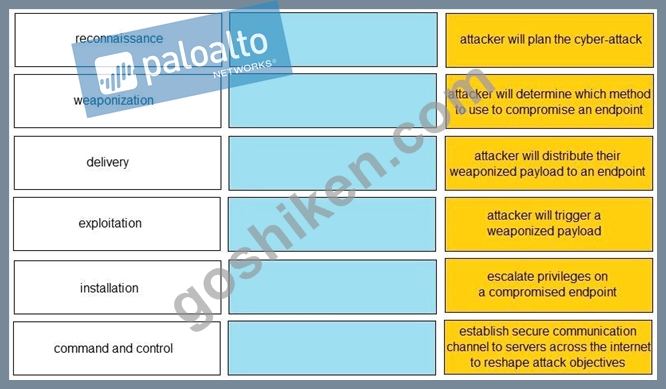
Given the graphic, match each stage of the cyber-attack lifecycle to its description.
正解:
解説: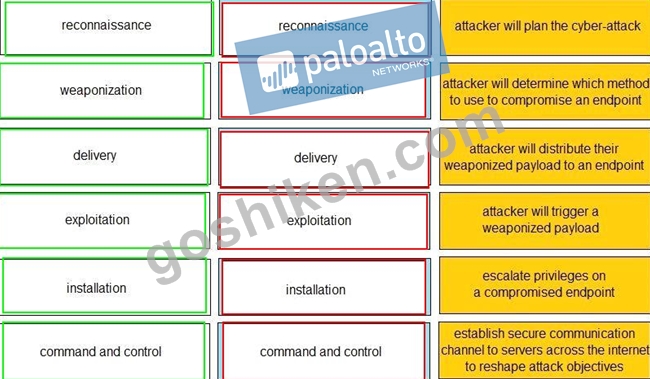
質問 # 54
Which option describes the "selective network security virtualization" phase of incrementally transforming data centers?
- A. during the selective network security virtualization phase, all intra-host communication paths are strictly controlled
- B. during the selective network security virtualization phase, all intra-host traffic is encapsulated and encrypted using the IPSEC protocol
- C. during the selective network security virtualization phase, all intra-host traffic is load balanced
- D. during the selective network security virtualization phase, all intra-host traffic is forwarded to a Web proxy server
正解:A
解説:
Selective network security virtualization: Intra-host communications and live migrations are architected at this phase. All intra-host communication paths are strictly controlled to ensure that traffic between VMs at different trust levels is intermediated either by an on-box, virtual security appliance or by an off-box, physical security appliance.
質問 # 55
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
- A. WildFire
- B. AutoFocus
- C. Cortex XDR
- D. MineMeld
正解:B
解説:
Explanation
"Palo Alto Networks AutoFocus enables a proactive, prevention-based approach to network security that puts automation to work for security professionals. Threat intelligence from the service is made directly accessible in the Palo Alto Networks platform, including PAN-OS software and Panorama. AutoFocus speeds the security team's existing workflows, which allows for in-depth investigation into suspicious activity, without additional specialized resources."
質問 # 56
On an endpoint, which method should you use to secure applications against exploits?
- A. strong user passwords
- B. software patches
- C. endpoint-based firewall
- D. full-disk encryption
正解:B
解説:
New software vulnerabilities and exploits are discovered all the time and thus diligent software patch management is required by system and security administrators in every organization.
質問 # 57
A native hypervisor runs:
- A. with extreme demands on network throughput
- B. within an operating system's environment
- C. only on certain platforms
- D. directly on the host computer's hardware
正解:D
質問 # 58
In SecOps, what are two of the components included in the identify stage? (Choose two.)
- A. Initial Research
- B. Change Control
- C. Content Engineering
- D. Breach Response
正解:A、C
質問 # 59
Which option is an example of a North-South traffic flow?
- A. Lateral movement within a cloud or data center
- B. An internal three-tier application
- C. Client-server interactions that cross the edge perimeter
- D. Traffic between an internal server and internal user
正解:C
解説:
Explanation
North-south refers to data packets that move in and out of the virtualized environment from the host network or a corresponding traditional data center. North-south traffic is secured by one or more physical form factor perimeter edge firewalls.
質問 # 60
Systems that allow for accelerated incident response through the execution of standardized and automated playbooks that work upon inputs from security technology and other data flows are known as what?
- A. STEP
- B. SOAR
- C. SIEM
- D. XDR
正解:B
質問 # 61
Which Palo Alto Networks subscription service complements App-ID by enabling you to configure the next- generation firewall to identify and control access to websites and to protect your organization from websites hosting malware and phishing pages?
- A. Threat Prevention
- B. DNS Security
- C. WildFire
- D. URL Filtering
正解:D
解説:
The URL Filtering service complements App-ID by enabling you to configure the next-generation firewall to identify and control access to websites and to protect your organization from websites that host malware and phishing pages.
質問 # 62
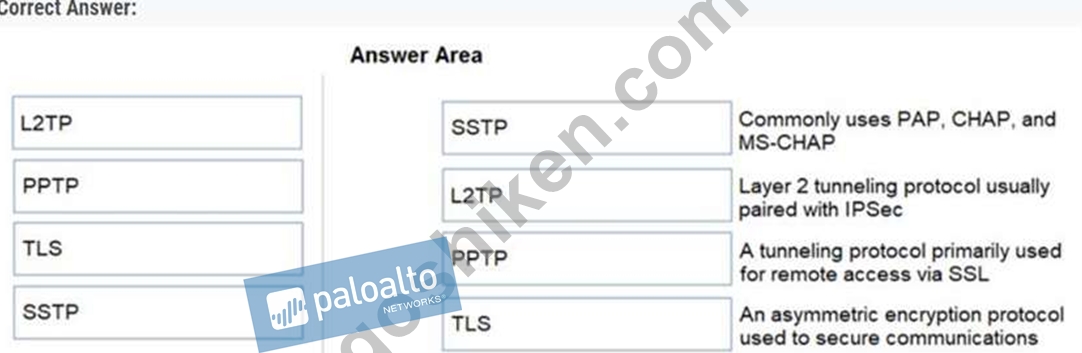
Match each tunneling protocol to its definition.
正解:
解説:
質問 # 63
Which network analysis tool can be used to record packet captures?
- A. Angry IP Scanner
- B. Smart IP Scanner
- C. Wireshark
- D. Netman
正解:C
質問 # 64
A native hypervisor runs:
- A. with extreme demands on network throughput
- B. within an operating system's environment
- C. only on certain platforms
- D. directly on the host computer's hardware
正解:D
解説:
Explanation
Type 1 (native or bare metal). Runs directly on the host computer's hardware Type 2 (hosted). Runs within an operating system environment
質問 # 65
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
- A. National security information
- B. Trade secret
- C. Credit card number
- D. A symmetric encryption key
正解:C
解説:
Explanation/Reference:
質問 # 66
......
PCCET試験問題高合格率なPCCET問題集PDF:https://www.goshiken.com/Palo-Alto-Networks/PCCET-mondaishu.html
PCCETのPDF問題集最近更新された問題:https://drive.google.com/open?id=1DeY6MDtQseH76RThMDs3FzGnaU0EnkoP
