2023年最新のGoShiken Palo Alto Networks PCCET問題集と試験テストエンジン
Palo Alto Networks PCCET問題集にはリアル試験問題解答
PCCET認定試験は、サイバーセキュリティ業界に新しく入る個人に基礎を提供するエントリーレベルの認定プログラムです。この認定プログラムは、Palo Alto Networks Certified Network Security Administrator(PCNSA)やPalo Alto Networks Certified Security Engineer(PCNSE)のような次のレベルの認定試験に備えるために設計されています。PCCET認定プログラムは、サイバーセキュリティにキャリアを開始し、この分野で成功するために必要な知識とスキルを獲得したい個人にとって、貴重な資産です。
PCCET認定は、サイバーセキュリティ業界で広く認知されており、ITプロフェッショナルの履歴書に優れた価値をもたらします。この認定は、個人がPalo Alto Networksの次世代ファイアウォールを構成、インストール、およびメンテナンスするために必要な知識とスキルを持っていることを証明します。さらに、この認定は、競争が激しい就職市場で個人が目立つ機会を提供し、収益能力を向上させるための素晴らしい手段です。全体的に、PCCET認定は、サイバーセキュリティのキャリアを開始したい個人にとって優れたスタート地点であり、Palo Alto Networksの次世代ファイアウォールを扱うすべての人にとって貴重な資産です。
質問 # 66
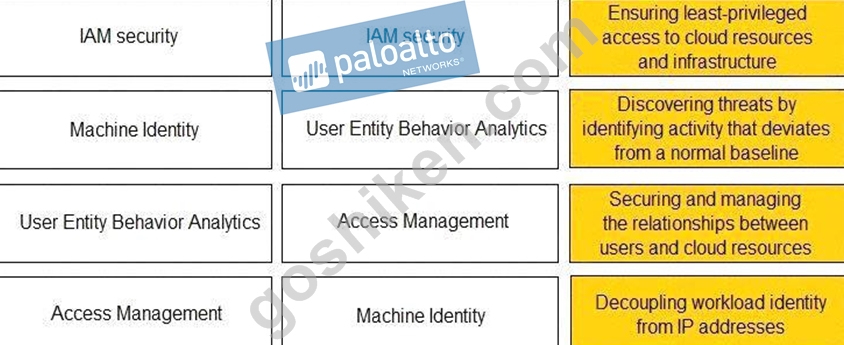
Match the Identity and Access Management (IAM) security control with the appropriate definition.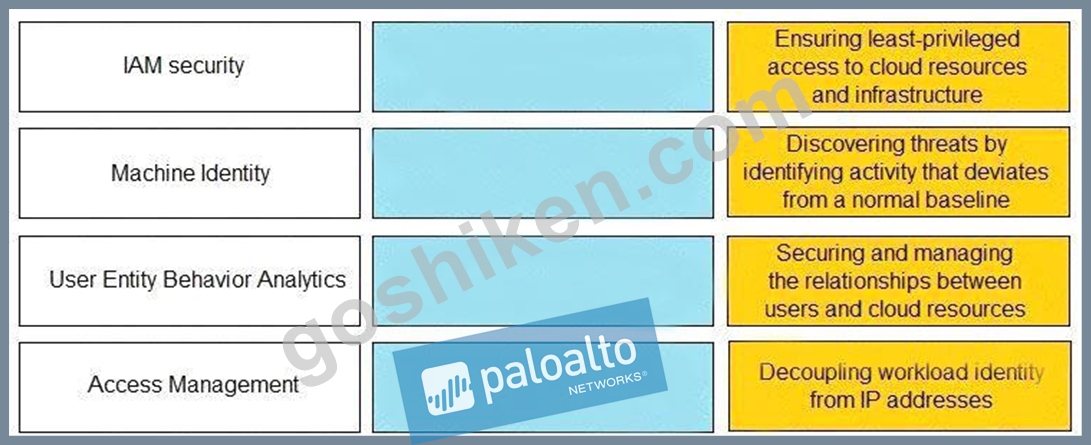
正解:
解説: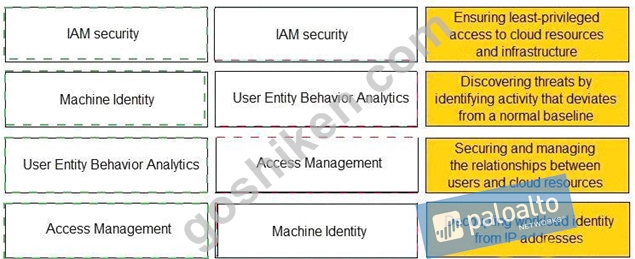
質問 # 67
Which model would a customer choose if they want full control over the operating system(s) running on their cloud computing platform?
- A. DaaS
- B. PaaS
- C. SaaS
- D. IaaS
正解:D
質問 # 68
From which resource does Palo Alto Networks AutoFocus correlate and gain URL filtering intelligence?
- A. BrightCloud
- B. PAN-DB
- C. Unit 52
- D. MineMeld
正解:B
解説:
Explanation
When you enable URL Filtering, all web traffic is compared against the URL Filtering database, PAN-DB, which contains millions of URLs that have been grouped into about 65 categories.
質問 # 69
In addition to local analysis, what can send unknown files to WildFire for discovery and deeper analysis to rapidly detect potentially unknown malware?
- A. Cortex XDR
- B. Cortex XSOAR
- C. AutoFocus
- D. MineMild
正解:A
質問 # 70
Which TCP/IP sub-protocol operates at the Layer7 of the OSI model?
- A. SNMP
- B. UDP
- C. MAC
- D. NFS
正解:A
解説:
Explanation
Application (Layer 7 or L7): This layer identifies and establishes availability of communication partners, determines resource availability, and synchronizes communication.
Presentation (Layer 6 or L6): This layer provides coding and conversion functions (such as data representation, character conversion, data compression, and data encryption) to ensure that data sent from the Application layer of one system is compatible with the Application layer of the receiving system.
Session (Layer 5 or L5): This layer manages communication sessions (service requests and service responses) between networked systems, including connection establishment, data transfer, and connection release.
Transport (Layer 4 or L4): This layer provides transparent, reliable data transport and end-to-end transmission control.
質問 # 71
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
- A. NetOps
- B. DevOps
- C. SecOps
- D. SecDevOps
正解:C
解説:
Security operations (SecOps) is a necessary function for protecting the digital way of life, for global businesses and customers. SecOps requires continuous improvement in operations to handle fast-evolving threats. SecOps needs to arm security operations professionals with high-fidelity intelligence, contextual data, and automated prevention workflows to quickly identify and respond to these threats. SecOps must leverage automation to reduce strain on analysts and execute the Security Operation Center's (SOC) mission to identify, investigate, and mitigate threats.
質問 # 72
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
- A. AutoFocus
- B. MineMeld
- C. WildFire
- D. Cortex XDR
正解:A
解説:
Explanation
"Palo Alto Networks AutoFocus enables a proactive, prevention-based approach to network security that puts automation to work for security professionals. Threat intelligence from the service is made directly accessible in the Palo Alto Networks platform, including PAN-OS software and Panorama. AutoFocus speeds the security team's existing workflows, which allows for in-depth investigation into suspicious activity, without additional specialized resources."
質問 # 73
Which network firewall operates up to Layer 4 (Transport layer) of the OSI model and maintains information about the communication sessions which have been established between hosts on trusted and untrusted networks?
- A. Static packet-filter
- B. Group policy
- C. Stateful
- D. Stateless
正解:C
解説:
Explanation
Stateful packet inspection firewalls Second-generation stateful packet inspection (also known as dynamic packet filtering) firewalls have the following characteristics:
They operate up to Layer 4 (Transport layer) of the OSI model and maintain state information about the communication sessions that have been established between hosts on the trusted and untrusted networks.
They inspect individual packet headers to determine source and destination IP address, protocol (TCP, UDP, and ICMP), and port number (during session establishment only) to determine whether the session should be allowed, blocked, or dropped based on configured firewall rules.
After a permitted connection is established between two hosts, the firewall creates and deletes firewall rules for individual connections as needed, thus effectively creating a tunnel that allows traffic to flow between the two hosts without further inspection of individual packets during the session.
This type of firewall is very fast, but it is port-based and it is highly dependent on the trustworthiness of the two hosts because individual packets aren't inspected after the connection is established.
質問 # 74
How does adopting a serverless model impact application development?
- A. costs more to develop application code because it uses more compute resources
- B. slows down the deployment of application code, but it improves the quality of code development
- C. reduces the operational overhead necessary to deploy application code
- D. prevents developers from focusing on just the application code because you need to provision the underlying infrastructure to run the code
正解:C
解説:
List three advantages of serverless computing over
CaaS: - Reduce costs - Increase agility - Reduce operational overhead
質問 # 75
Which SOAR feature coordinates across technologies, security teams, and external users for centralized data visibility and action?
- A. Ticketing system
- B. Case management
- C. Integrations
- D. Playbooks
正解:D
質問 # 76
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
- A. control and protect inter-host traffic using routers configured to use the Border Gateway Protocol (BGP) dynamic routing protocol
- B. control and protect inter-host traffic by using IPv4 addressing
- C. control and protect inter-host traffic using physical network security appliances
- D. control and protect inter-host traffic by exporting all your traffic logs to a sysvol log server using the User Datagram Protocol (UDP)
正解:C
質問 # 77
What differentiates knowledge-based systems from behavior-based systems?
- A. Behavior-based systems pull from a previously stored database that distinguishes "bad".
- B. Knowledge-based systems pull from a previously stored database that distinguishes "bad". C.
Knowledge-based systems try to find new, distinct traits to find "bad" things. - C. Behavior-based systems find the data that knowledge-based systems store.
正解:A
質問 # 78
Data Loss Prevention (DLP) and Cloud Access Security Broker (CASB) fall under which Prisma access service layer?
- A. Cloud
- B. Management
- C. Security
- D. Network
正解:C
解説:
A SASE solution converges networking and security services into one unified, cloud-delivered solution (see Figure 3-12) that includes the following:
* Networking
* Software-defined wide-area networks (SD-WANs)
* Virtual private networks (VPNs)
* Zero Trust network access (ZTNA)
* Quality of Service (QoS)
* Security
* Firewall as a service (FWaaS)
* Domain Name System (DNS) security
* Threat prevention
* Secure web gateway (SWG)
* Data loss prevention (DLP)
* Cloud access security broker (CASB)
質問 # 79
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
- A. Dynamic
- B. Pre-exploit protection
- C. Bare-metal
- D. Static
正解:A
解説:
The WildFire cloud-based malware analysis environment is a cyber threat prevention service that identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment.
質問 # 80
How does adopting a serverless model impact application development?
- A. costs more to develop application code because it uses more compute resources
- B. slows down the deployment of application code, but it improves the quality of code development
- C. reduces the operational overhead necessary to deploy application code
- D. prevents developers from focusing on just the application code because you need to provision the underlying infrastructure to run the code
正解:C
解説:
Explanation
List three advantages of serverless computing over
CaaS: - Reduce costs - Increase agility - Reduce operational overhead
質問 # 81
A native hypervisor runs:
- A. with extreme demands on network throughput
- B. within an operating system's environment
- C. directly on the host computer's hardware
- D. only on certain platforms
正解:C
解説:
Explanation
Type 1 (native or bare metal). Runs directly on the host computer's hardware Type 2 (hosted). Runs within an operating system environment
質問 # 82
Which IPsec feature allows device traffic to go directly to the Internet?
- A. d.Authentication Header (AH)
- B. Diffie-Hellman groups
- C. Split tunneling
- D. IKE Security Association
正解:C
解説:
"Or split tunneling can be configured to allow internet traffic from the device to go directly to the internet, while other specific types of traffic route through the IPsec tunnel, for acceptable protection with much less performance degradation."
質問 # 83
Which method is used to exploit vulnerabilities, services, and applications?
- A. DNS tunneling
- B. encryption
- C. port evasion
- D. port scanning
正解:C
解説:
Explanation
Attack communication traffic is usually hidden with various techniques and tools, including:
Encryption with SSL, SSH (Secure Shell), or some other custom or proprietary encryption Circumvention via proxies, remote access tools, or tunneling. In some instances, use of cellular networks enables complete circumvention of the target network for attack C2 traffic.
Port evasion using network anonymizers or port hopping to traverse over any available open ports Fast Flux (or Dynamic DNS) to proxy through multiple infected endpoints or multiple, ever-changing C2 servers to reroute traffic and make determination of the true destination or attack source difficult DNS tunneling is used for C2 communications and data infiltration
質問 # 84
Which product from Palo Alto Networks enables organizations to prevent successful cyberattacks as well as simplify and strengthen security processes?
- A. Cortex XDR
- B. AutoFocus
- C. Expedition
- D. MineMeld
正解:A
解説:
Explanation
From a business perspective, XDR platforms enable organizations to prevent successful cyberattacks as well as simplify and strengthen security processes.
質問 # 85
Anthem server breaches disclosed Personally Identifiable Information (PII) from a number of its servers. The infiltration by hackers was attributed to which type of vulnerability?
- A. a phishing scheme that captured a database administrator's password
- B. access by using a third-party vendor's password
- C. exploitation of an unpatched security vulnerability
- D. an intranet-accessed contractor's system that was compromised
正解:A
質問 # 86
......
2023年最新のGoShiken PCCETのPDFで最近更新された問題です:https://www.goshiken.com/Palo-Alto-Networks/PCCET-mondaishu.html
PCCET試験には保証が付きます。更新されたのは145問があります:https://drive.google.com/open?id=1DeY6MDtQseH76RThMDs3FzGnaU0EnkoP
