PCCET練習問題集で検証済みで更新された77問題あります
更新されたPCCET試験問題集でPDF問題とテストエンジン
質問 31
Which TCP/IP sub-protocol operates at the Layer7 of the OSI model?
- A. MAC
- B. SNMP
- C. UDP
- D. NFS
正解: B
質問 32
Which tool supercharges security operations center (SOC) efficiency with the world's most comprehensive operating platform for enterprise security?
- A. Cortex XDR
- B. Prisma SAAS
- C. Cortex XSOAR
- D. WildFire
正解: C
質問 33
When signature-based antivirus software detects malware, what three things does it do to provide protection?
(Choose three.)
- A. remove the infected file's extension
- B. decrypt the infected file using base64
- C. alert system administrators
- D. quarantine the infected file
- E. delete the infected file
正解: A,D,E
解説:
Explanation
質問 34
Which model would a customer choose if they want full control over the operating system(s) running on their cloud computing platform?
- A. IaaS
- B. SaaS
- C. PaaS
- D. DaaS
正解: A
質問 35
Which option describes the "selective network security virtualization" phase of incrementally transforming data centers?
- A. during the selective network security virtualization phase, all intra-host traffic is encapsulated and encrypted using the IPSEC protocol
- B. during the selective network security virtualization phase, all intra-host communication paths are strictly controlled
- C. during the selective network security virtualization phase, all intra-host traffic is forwarded to a Web proxy server
- D. during the selective network security virtualization phase, all intra-host traffic is load balanced
正解: B
質問 36
Which endpoint tool or agent can enact behavior-based protection?
- A. AutoFocus
- B. DNS Security
- C. MineMeld
- D. Cortex XDR
正解: D
質問 37
Which option is an example of a North-South traffic flow?
- A. Lateral movement within a cloud or data center
- B. Traffic between an internal server and internal user
- C. Client-server interactions that cross the edge perimeter
- D. An internal three-tier application
正解: C
質問 38
Given the graphic, match each stage of the cyber-attack lifecycle to its description.
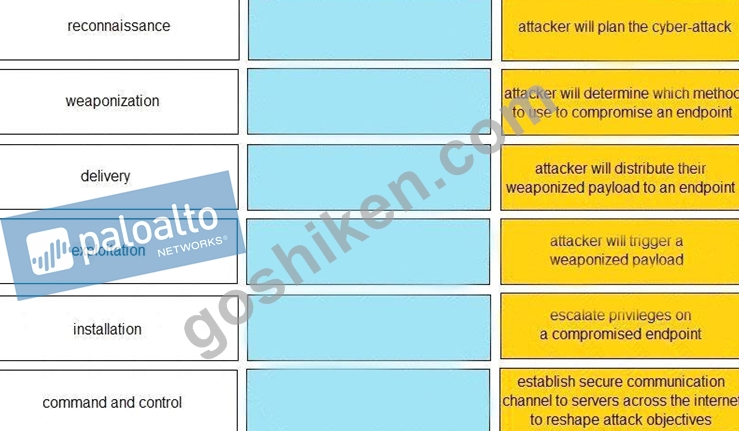
正解:
解説: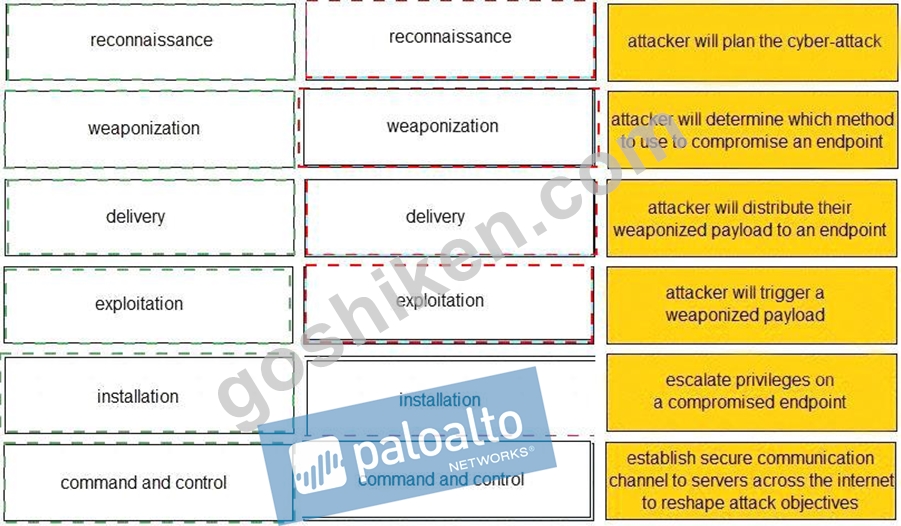
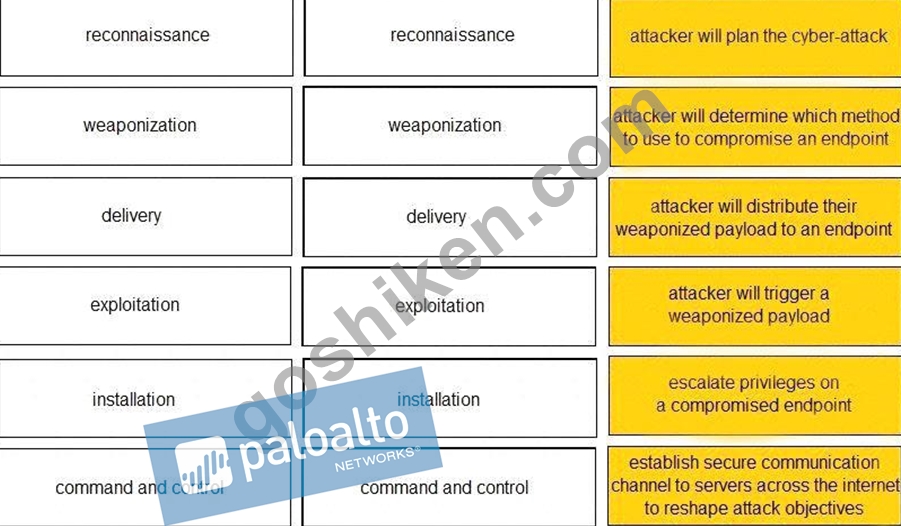
質問 39
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
- A. DevOps
- B. SecOps
- C. NetOps
- D. SecDevOps
正解: B
質問 40
How does Prisma SaaS provide protection for Sanctioned SaaS applications?
- A. Prisma SaaS connects to an organizations internal print and file sharing services to provide protection and sharing visibility
- B. Prisma SaaS connects directly to sanctioned external service providers SaaS application service to provide protection and sharing visibility
- C. Prisma access uses Uniform Resource Locator (URL) Web categorization to provide protection and sharing visibility
- D. Prisma SaaS does not provide protection for Sanctioned SaaS applications because they are secure
正解: B
質問 41
Which characteristic of serverless computing enables developers to quickly deploy application code?
- A. Uploading cloud service autoscaling services to deploy more virtual machines to run their application code based on user demand
- B. Using cloud service spot pricing to reduce the cost of using virtual machines to run their application code
- C. Using Container as a Service (CaaS) to deploy application containers to run their code.
- D. Uploading the application code itself, without having to provision a full container image or any OS virtual machine components
正解: A
質問 42
A native hypervisor runs:
- A. within an operating system's environment
- B. with extreme demands on network throughput
- C. directly on the host computer's hardware
- D. only on certain platforms
正解: C
質問 43
How does adopting a serverless model impact application development?
- A. costs more to develop application code because it uses more compute resources
- B. prevents developers from focusing on just the application code because you need to provision the underlying infrastructure to run the code
- C. reduces the operational overhead necessary to deploy application code
- D. slows down the deployment of application code, but it improves the quality of code development
正解: C
質問 44
Which IPsec feature allows device traffic to go directly to the Internet?
- A. d.Authentication Header (AH)
- B. IKE Security Association
- C. Split tunneling
- D. Diffie-Hellman groups
正解: C
質問 45
Which network firewall operates up to Layer 4 (Transport layer) of the OSI model and maintains information about the communication sessions which have been established between hosts on trusted and untrusted networks?
- A. Static packet-filter
- B. Stateless
- C. Group policy
- D. Stateful
正解: D
質問 46
Which not-for-profit organization maintains the common vulnerability exposure catalog that is available through their public website?
- A. Office of Cyber Security and Information Assurance
- B. MITRE
- C. Department of Homeland Security
- D. Cybersecurity Vulnerability Research Center
正解: B
質問 47
......
最新(2022)Palo Alto Networks PCCET試験問題集:https://www.goshiken.com/Palo-Alto-Networks/PCCET-mondaishu.html
最適な練習法にはPalo Alto Networks PCCET試験の素晴らしいPCCET試験問題PDF:https://drive.google.com/open?id=1DeY6MDtQseH76RThMDs3FzGnaU0EnkoP
